Threat Protection Solutions: Threat Protection
With thousands of new vulnerabilities disclosed annually, not even the largest and most efficient IT department can promptly patch every single one within their environment. And even if they could, it wouldn’t be smart of them to take this approach, because vulnerabilities carry different levels of risk, ranging from trivial to critical.
Consequently, organizations must be highly selective when drafting their vulnerability remediation plans. They can’t base the process on guesswork or on an arbitrary patching schedule. Instead, they must pinpoint which IT assets must be patched with the greatest urgency at any given time.
Prioritize Your Vulnerability Remediation Work with Qualys Threat Protection
Qualys built Threat Protection to address this problem of vulnerability and threat disclosure overload by automating the large-scale and continuous data analysis that the process demands. Threat Protection continuously correlates real-time threat information against your vulnerabilities and IT asset inventory, giving you a clear and comprehensive view of your organization’s threat landscape.
Features
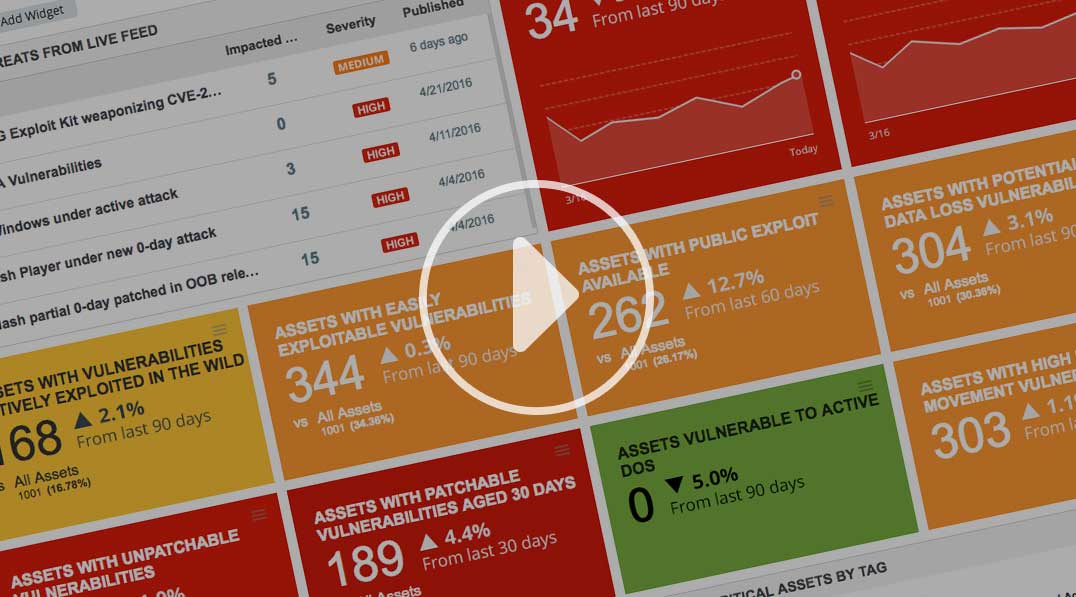
Centralized Control and Visualization Panel
A single, dynamic dashboard includes customizable views, graphs and charts.
Threat Context from Qualys and Outside Experts
Threat Protection appends relevant threat indicators to each vulnerability, such as “zero day” status, inclusion in an exploit kit and high data loss potential.
The Live Feed
The Live Threat Intelligence Feed displays the latest vulnerability disclosures and maps them to your impacted IT assets.
Powerful Search Function
The search engine lets you look for specific assets and vulnerabilities by crafting ad-hoc queries with multiple variables and criteria. Queries can be saved and turned into dashboard widgets.
Native Component of the Enterprise TruRisk Platform
No need to export our scan data for prioritization. This now integrated functionality is delivered with speed, convenience and accuracy unmatched by external tools.
Robust Data Analysis
Threat Protection's back end analysis engine continuously correlates external threat information with internal vulnerability and asset data.
Learn more about Qualys Threat Protection
Free Trial