TotalCloud™ - The Risk-minded CNAPP
Your Cloud. De-risked.
The AI-powered Cloud Native Application Protection Platform (CNAPP) for Cloud and Container environments.
De-risk your Cloud and Container environments with one prioritized view of risk so you can fix what matters most … first!
Measure Risk
with
360° scanning
to detect vulnerabilities
Detect Malware
with up to
99%+ Accuracy
thanks to AI-powered deep learning threat detection
Protect Cloud Infra & SaaS Apps up to
85%+ faster
with a unified, prioritized view of risk
TotalCloud™ – A unified CNAPP solution for multiple use cases
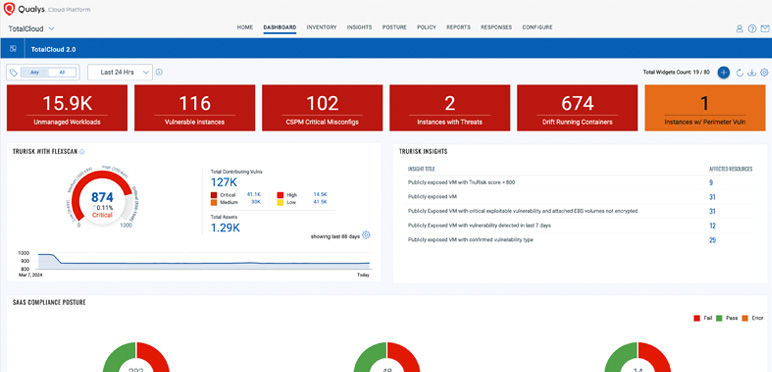
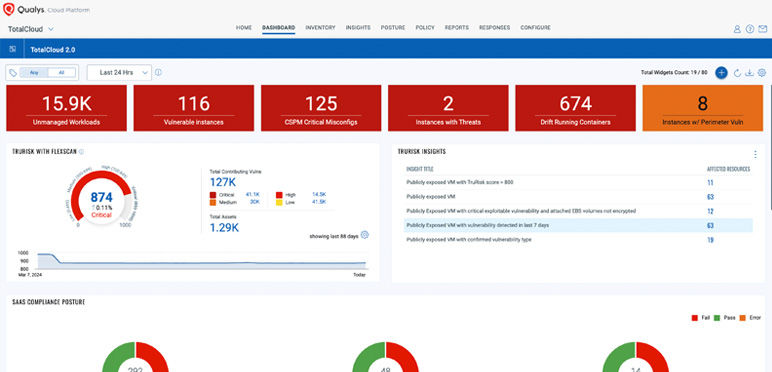
Correlate unique cloud security risk indicators from diverse Qualys sources with a holistic view of risk.
Empower your security team to measure, communicate, and help eliminate risk across your multi-cloud and container environments through a unified approach that lets you detect active threats and malware in real time.
TotalCloud™ - Powerful Cloud Security Features
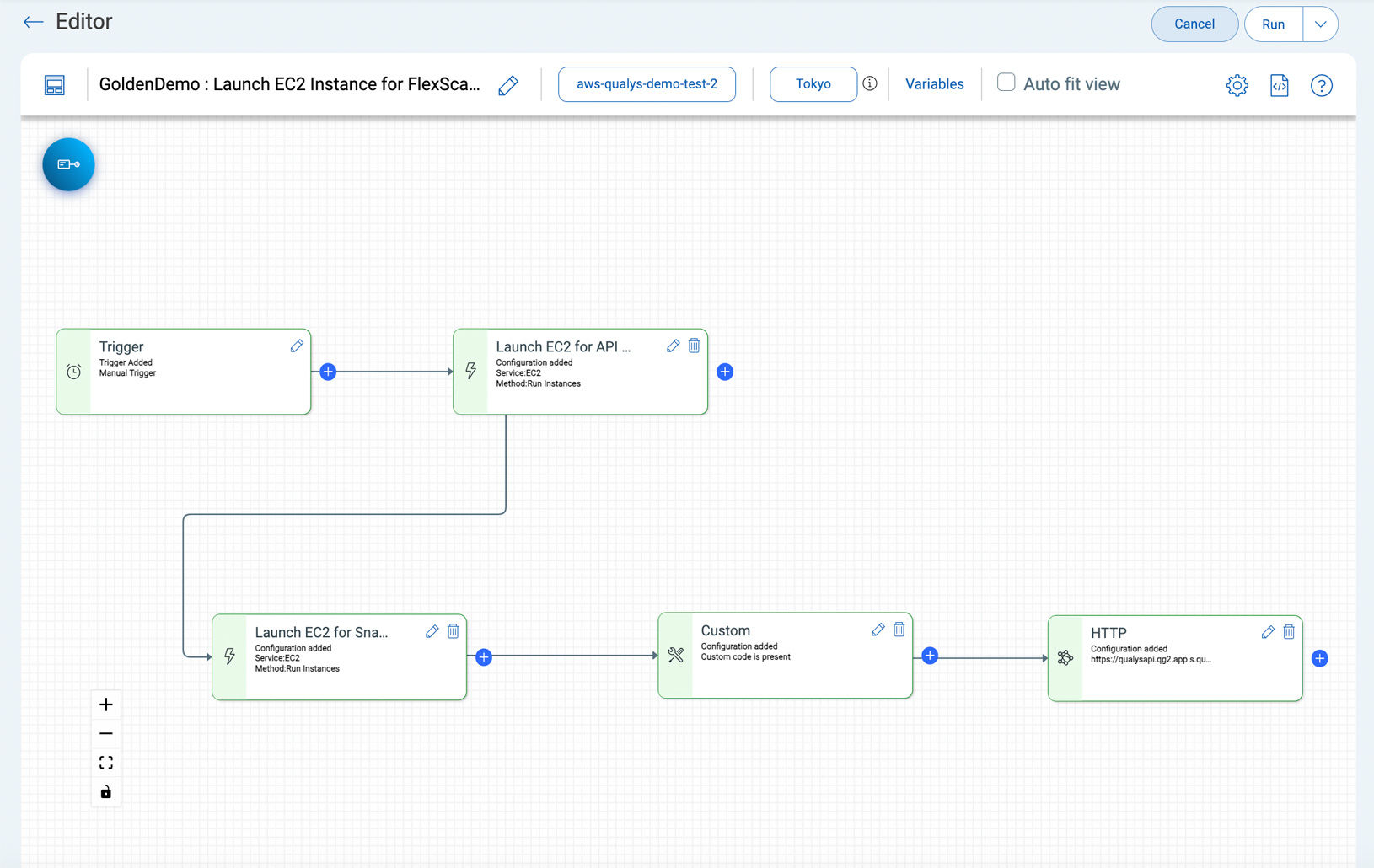
Prioritize Real Risk With FlexScan Coverage
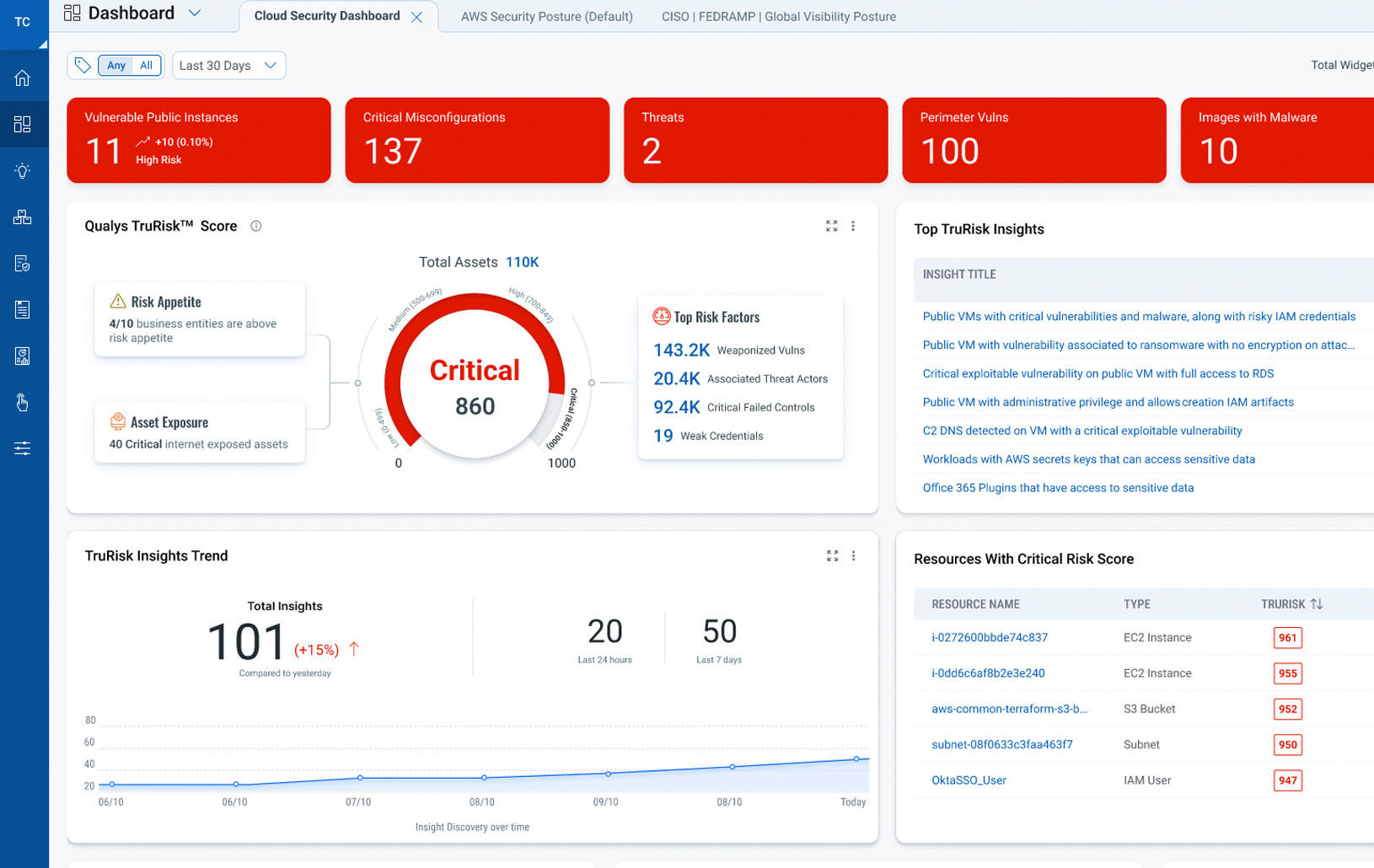
Prioritize business-Informed, exploitable risk with TruRisk scoring.
Qualys FlexScan-Flexible coverage for both long-lived and ephemeral workloads using agent, agentless, network and API-based scanning.

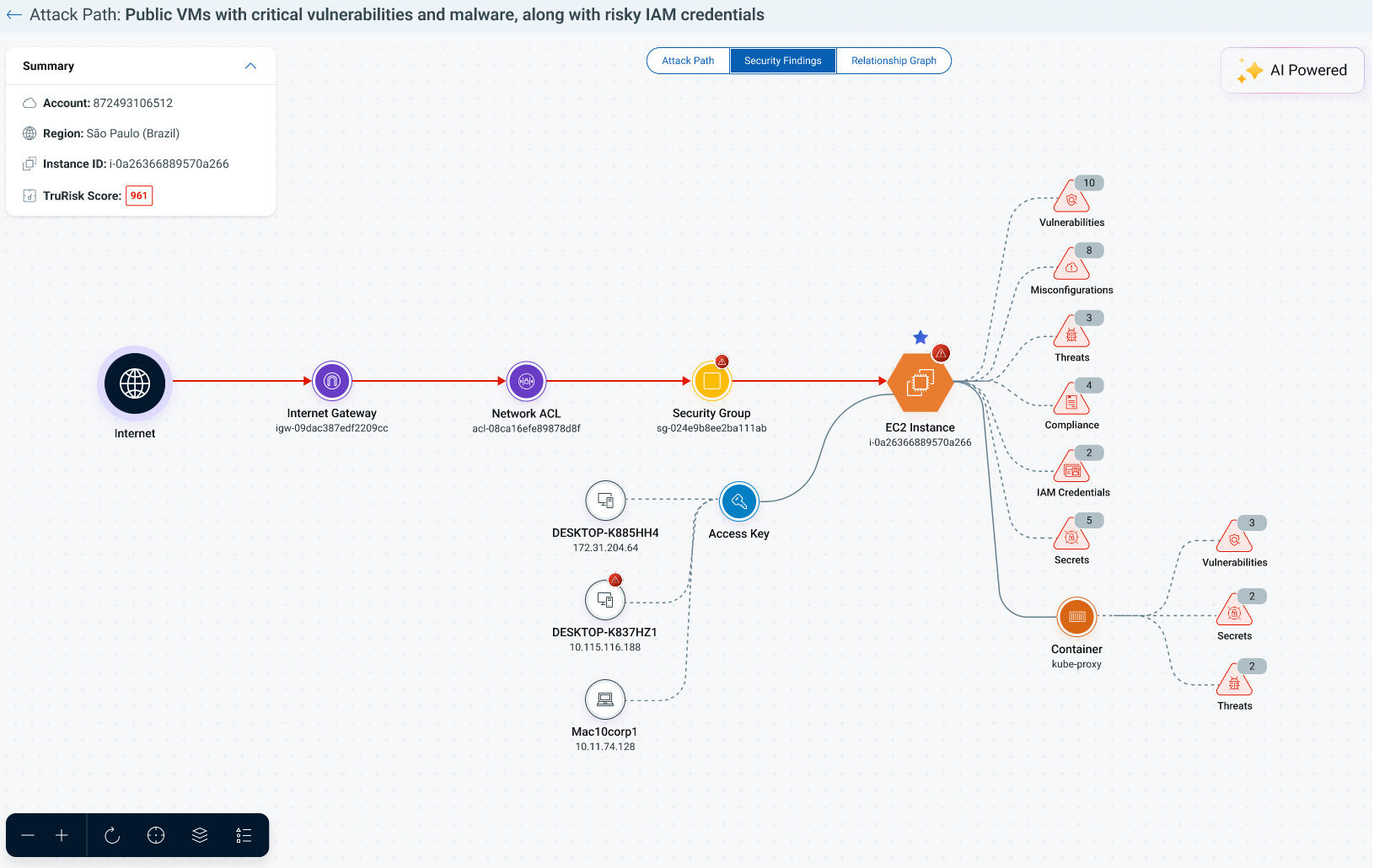
Contextualize The Impact With Attack Path Analysis
Contextualize the impact of vulnerabilities by mapping active attack paths to lateral movements and crown jewel assets. Assess additional blast radius impact from insecure developer endpoints.

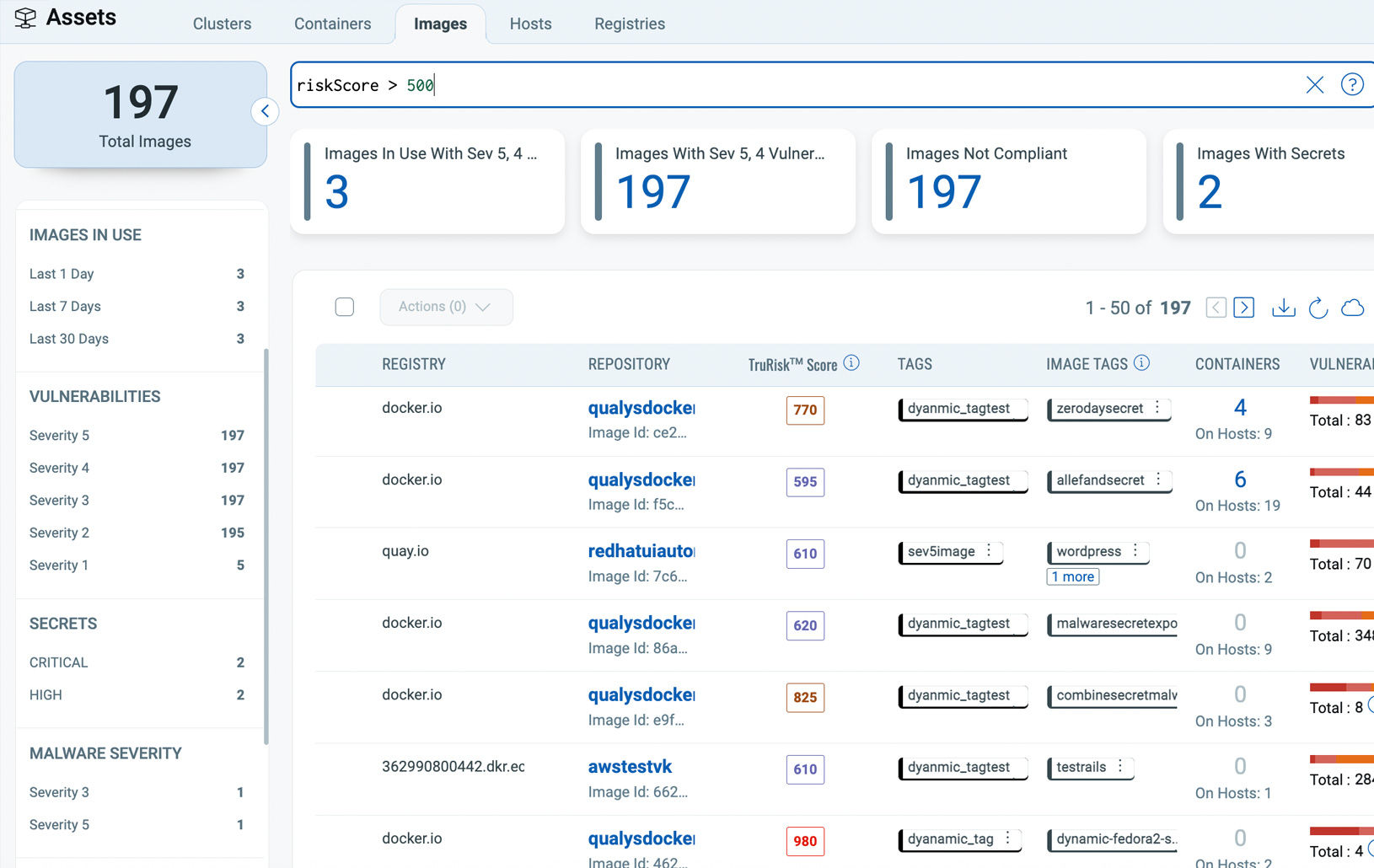
Secure Kubernetes And Containers From Build To Runtime
Continuously discover and assess images and containers across Kubernetes, Docker Hosts, Registries, and CI/CD Pipelines for vulnerabilities, malware, secrets, and SBOM.

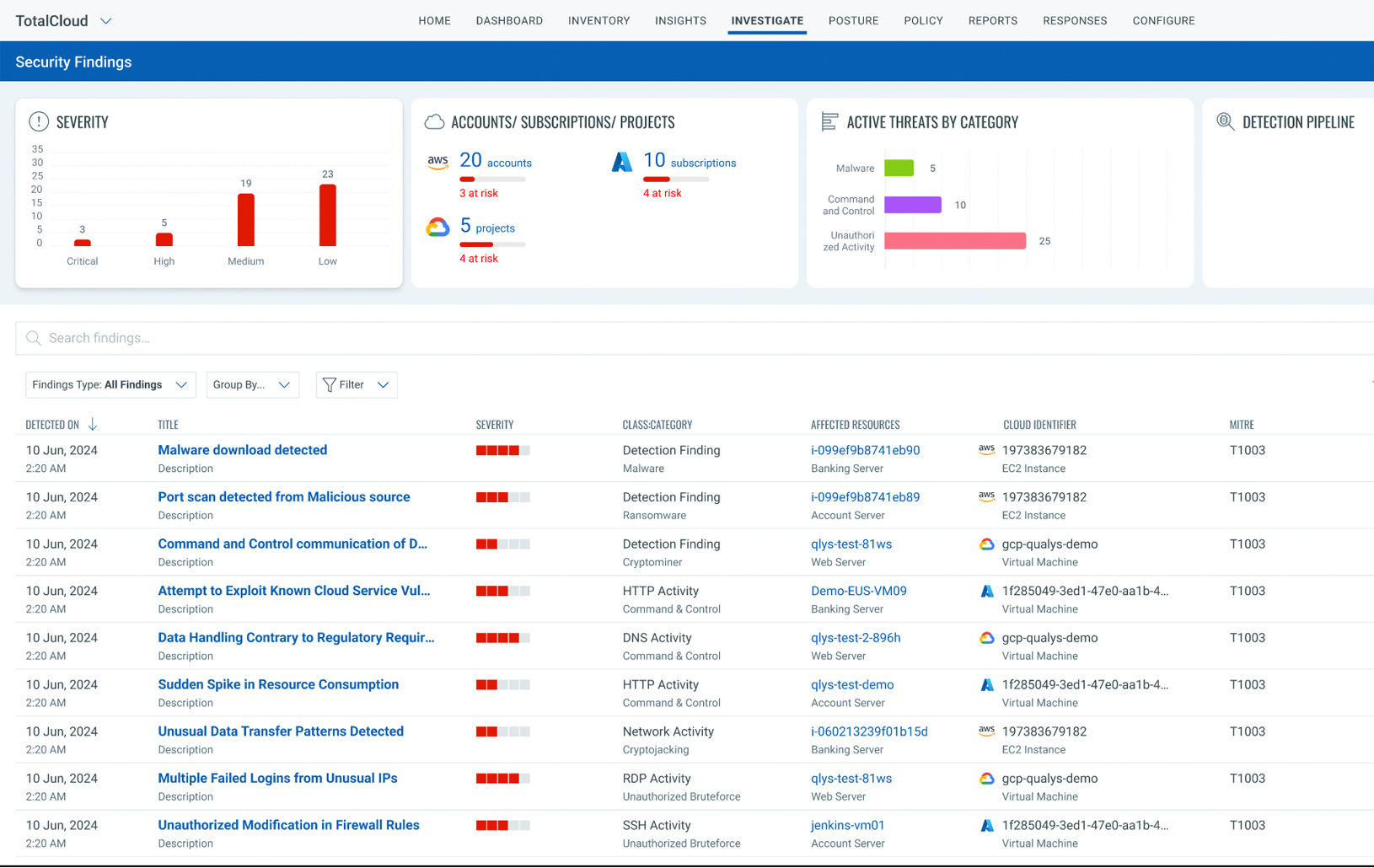
Stay Resilient Against Malicious Threats
Detect and stop Zero-Day Threats and Malware with Deep Learning AI based detection and correlation of Cloud Trail and Real-Time workload events.

Achieve Audit-Readiness With Continuous Compliance
Support for over 40+ Mandates across Regions and Verticals. Qualys enables policy audit across CIS, NIST, HIPAA, PCI and more in runtime as well as laC to ensure you deploy safely and securely.

Remediate With No-Code Automation Playbooks
Remediate your risk from build to runtime with low-code no-code drag and drop automation, customize workflows to meet your business needs including integrations with JIRA and ServiceNow.

Complete posture visibility in under 10 minutes
Rapidly assess all your cloud resources, including transient and ephemeral resources, for vulnerabilities and misconfigurations with a risk-based view in under 10 minutes.
Continuous scanning to reduce exposure to vulnerabilities
Continuous, multi-vector scanning with no-touch, agentless, API- and snapshot-based scanning and agent- and network-based scanning for in-depth assessment.
Manage security posture and risk across your entire SaaS application stack
Provides a protective shield for your favorite enterprise SaaS apps like Microsoft 365, Salesforce, Zoom, Google Workspace, and more, keeping them just as secure as your core cloud environment.
Detect vulnerabilities that other solutions miss
Up to Six Sigma (99.99966%) accuracy with any scanning method avoids alert fatigue to reduce the risk of breaches.
85% time saving with a unified view of risk
One prioritized view of risk to fix what matters most instead of looking at siloed data.
Real-time detection
Continuous detection of known and unknown threats - ransomware, malware, and active exploitation in real-time.
Explore TotalCloud CNAPP Product Tours
Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.