Qualys scanning accuracy.
6+ billion scans per year 99.99966% Six Sigma accuracy
We identified false positives in every scanner but Qualys.
![]()
Why accuracy is important
Vulnerability and configuration scanning helps you discover hidden systems and identify vulnerabilities before attackers do. The accuracy of these scans determines how well the results can be used by your IT teams to find and fix your highest-priority security and compliance issues.
Accurate results
Inaccurate results
Qualys Accuracy
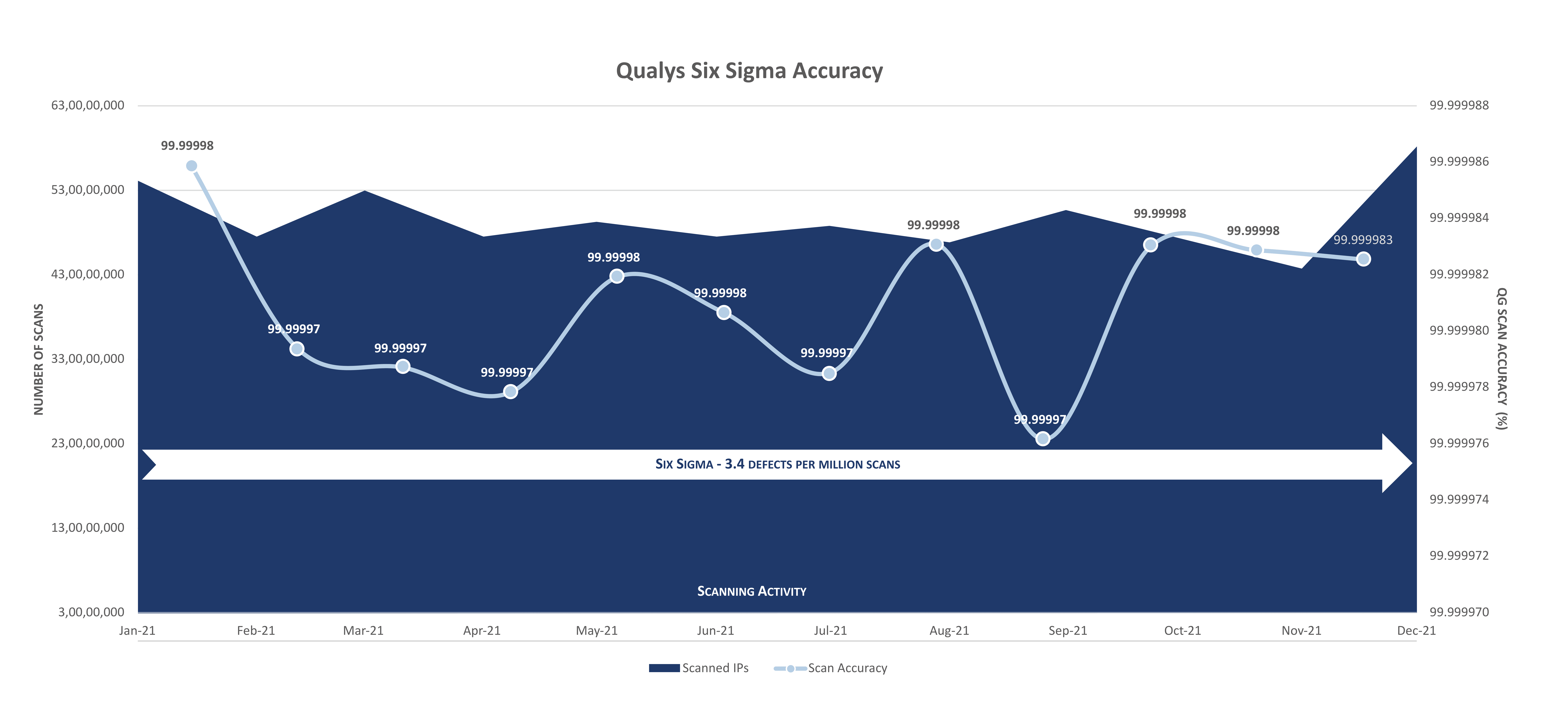
The Enterprise TruRisk Platform has performed more than 6 billion scans in the past year. Its vulnerability and configuration scans, the most difficult type of scans, consistently exceed Six Sigma 99.99966% accuracy, the industry standard for high quality. This level of accuracy creates a foundation for strong security and reliable compliance that enables you to efficiently zero in on potential risks before you get attacked.
Qualys exceeds Six Sigma
Qualys has achieved Six Sigma for over 10 years straight
The Six Sigma technique is well-suited to improving the quality of vulnerability and configuration scanning necessary for giving organizations continuous, real-time visibility of all of their IT assets. This sophisticated, multi-step process requires commitment across the entire organization to achieve the desired results. Comparing quality levels over time against the volume of scans conducted shows whether a security and compliance solution can be relied upon, especially as the number of IT assets multiply – whether on premises, at endpoints and in clouds.
In the twelve months ending in December 2020, the Enterprise TruRisk Platform performed over 6 billion security and compliance scans, while keeping defect levels low:

Qualys exceeds Six Sigma
Qualys’ unique methodology
Qualys exceeds Six Sigma accuracy by combining cloud technology with finely-tuned business processes to anticipate and avoid problems at each stage in the vulnerability scanning process:
Potential problem
How Qualys
prevents the problem
Scanners improperly provisioned
Vulnerability scanners are complex combinations of software, databases, and networking technology that need to work seamlessly together.
Qualys is a pure cloud-based platform that is heavily optimized for use with complex networks. It is professionally administered 24x7x365 in data centers around the world and requires no purchases, setup or maintenance of servers, databases or other software by customers.
Devices not scanned realistically
Scanning Internet-facing systems from inside a corporate network can present an inaccurate view of what attackers will encounter.
Qualys combines Internet-based scans for external perimeter devices with internal scans from remotely managed scanning appliances and Cloud Agents to provide a comprehensive view of your systems — on the Internet, in your corporate network, or in the cloud.
Device crashes
Some devices have hardware or operating systems that are sensitive to scanning and can fail when pushed beyond their limits.
Qualys automatically adjusts its scans according to how devices react, to avoid overloading them.
Device OSes misidentified
Devices with unusual configurations (esp. hardened appliances) can be tricky to identify correctly.
Qualys has spent more than 10 years tuning its recognition algorithms and is constantly updating them to handle new devices and OS versions.
Service crashes on devices
Sometimes a network service on a device may stop functioning after a scan even if the device itself keeps running.
Qualys tailors each scan to the OS that is detected and dynamically adjusts the intensity of scanning to avoid overloading services on the device.
False negatives
Scanners that aren’t kept up-to-date can miss potential risks.
Qualys continually updates its knowledgebase of vulnerability definitions to address new and evolving threats. All customers swiftly benefit from new vulnerabilities found anywhere in the world.
False positives
Scanners that aren’t tuned properly or that have inaccurate vulnerability definitions may flag issues that aren’t true risks.
Qualys automatically tests all vulnerability definitions before they’re deployed, as well as while they’re active, to verify that definitions are up-to-date. In addition, Qualys enables users to flag vulnerability definitions they think need adjusting. Such requests are immediately investigated by Qualys’ worldwide team of engineers and are typically resolved in less than 72 hours — often even within the same day.
The bottom line
Qualys goes beyond simply identifying vulnerabilities; it also helps you download the particular vendor fixes and updates needed to address each vulnerability. This patch-centric approach helps you prioritize which problems to address first and frees you from having to weed through long, repetitive lists of issues.
The impact of Qualys' Six Sigma accuracy is directly reflected in the low rate of issues that get submitted to Qualys Customer Support.
With Qualys’ high accuracy, your teams in charge of securing on-premises infrastructure, cloud infrastructure, endpoints, DevOps, compliance and web apps can each efficiently focus on reducing risk and not just detecting it. There is no security without accuracy.
See for yourself. Try Qualys for free.
Start your free trial today. No software to download or install. Email us or call us at 1 (800) 745-4355.
