The Qualys Enterprise TruRiskTM Platform
Measure, communicate, and eliminate cyber risk across the extended enterprise.
Learn More Download the Enterprise TruRisk Platform Brochure
Measure
Calculate the known and unknown cyber risk across your internal and external attack surface and quantify it in a way that meets the unique demands of your business.
Communicate
Go beyond just enumerating your cyber risk with the ability to clearly define it and articulate your complete cyber risk posture throughout your organization.
Eliminate
Proactively eliminate the most critical vulnerabilities within your environment with easy-to-use workflows that unify your Security and IT teams.
- Measure
- Communicate
- Eliminate
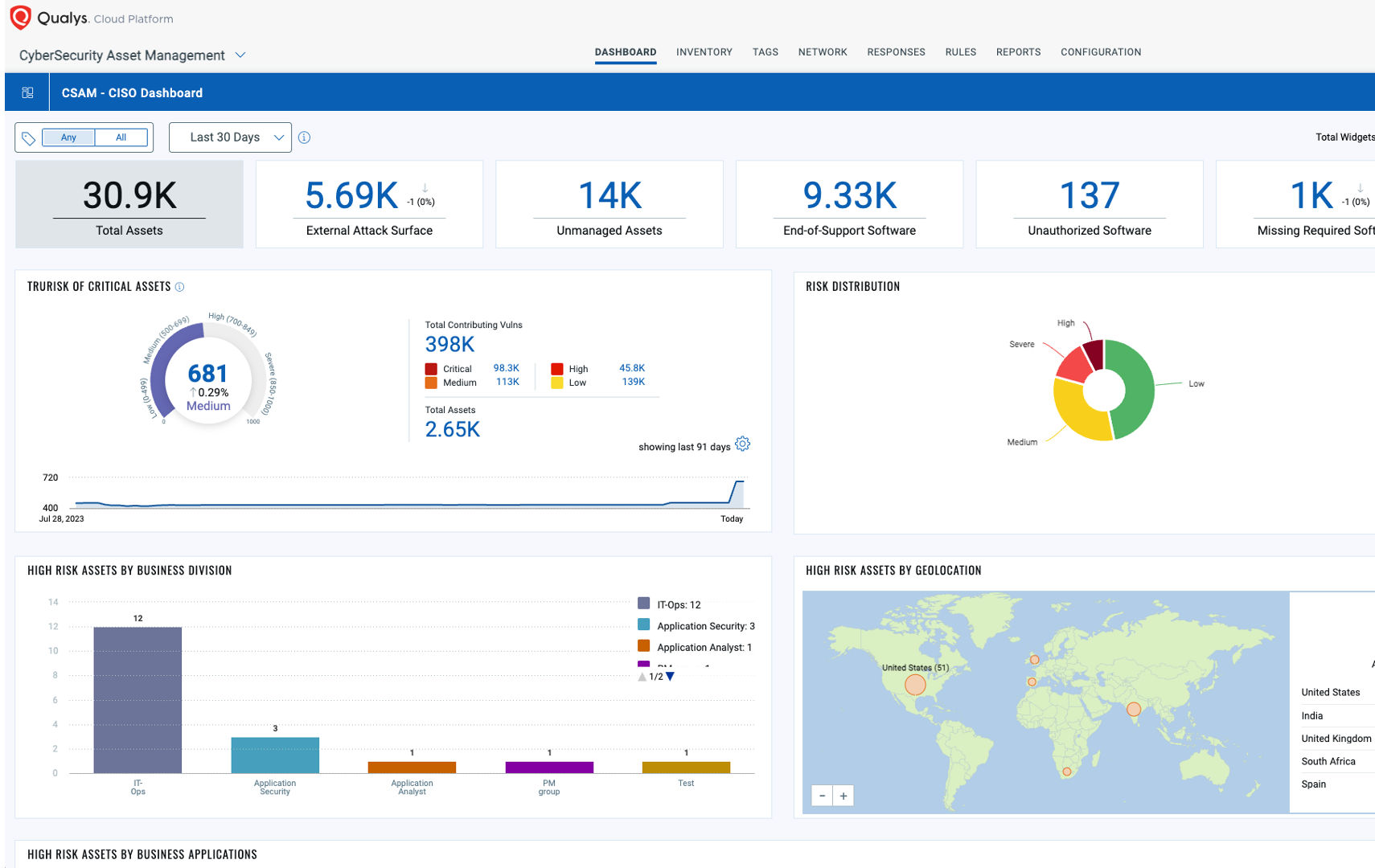
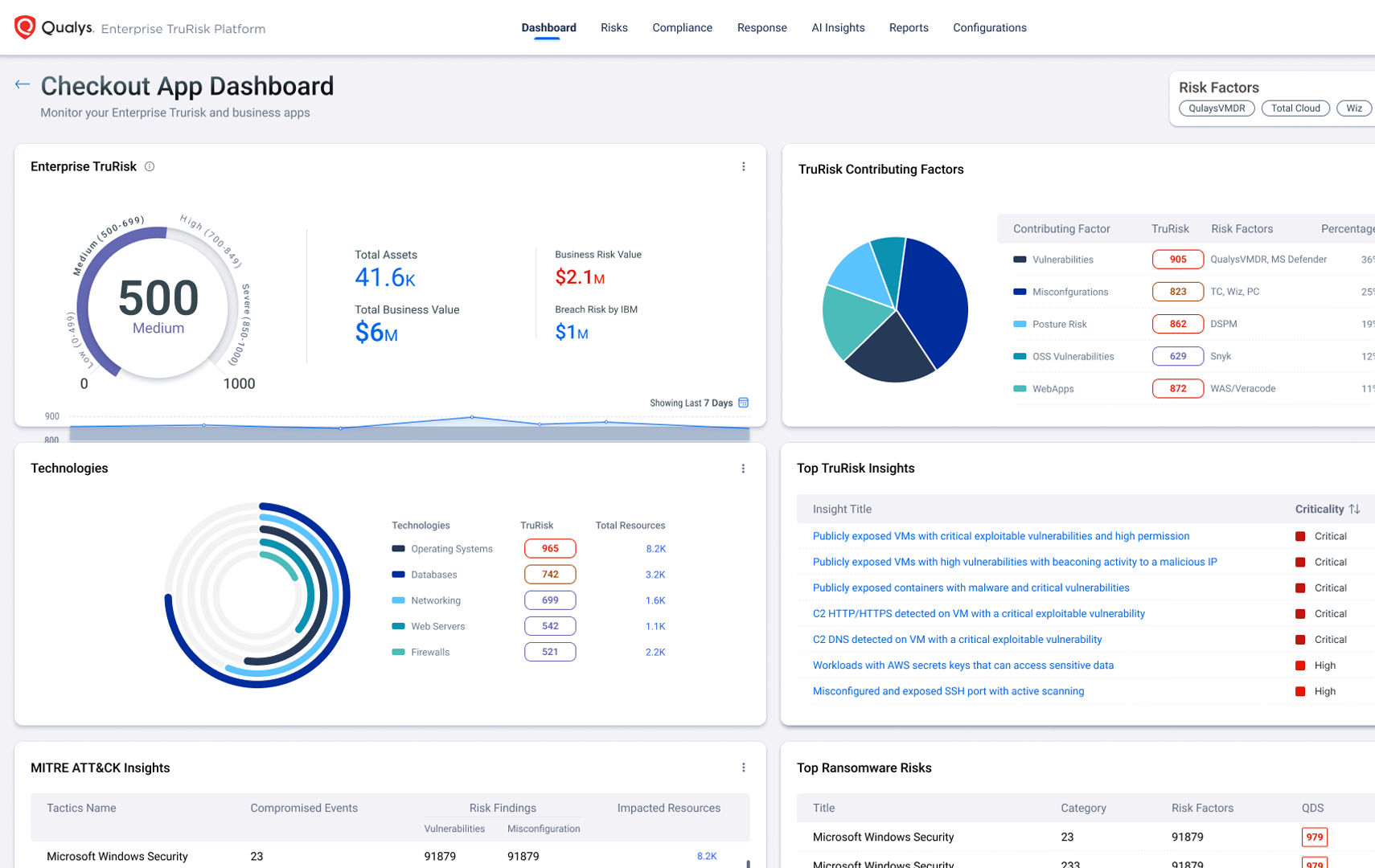
What is TruRisk?
TruRisk is the industry standard on how to apply risk-based prioritization to your cyber security program. While EPSS and CVSS are foundational metrics for severity, they can miss real threats and fail to filter out non-critical risk without complete business context of the environment. TruRisk aggregates ALL risk-factors from 73 thousand vulnerability signatures, 25+ sources of threat intel, and integrations with non-Qualys products to achieve:
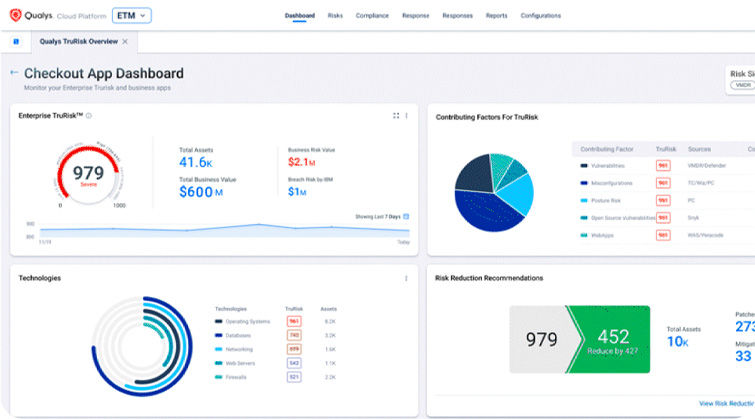

De-risk your business with the Enterprise TruRisk Platform.
One agent. Multiple use cases. A unified view of risk.
Quickly deploy lightweight Cloud Agents to reduce TCO and consolidate IT, Security, and Compliance solutions.
Secure your entire attack surface
Discover everything with business context and lay the foundation for risk-based vulnerability management.
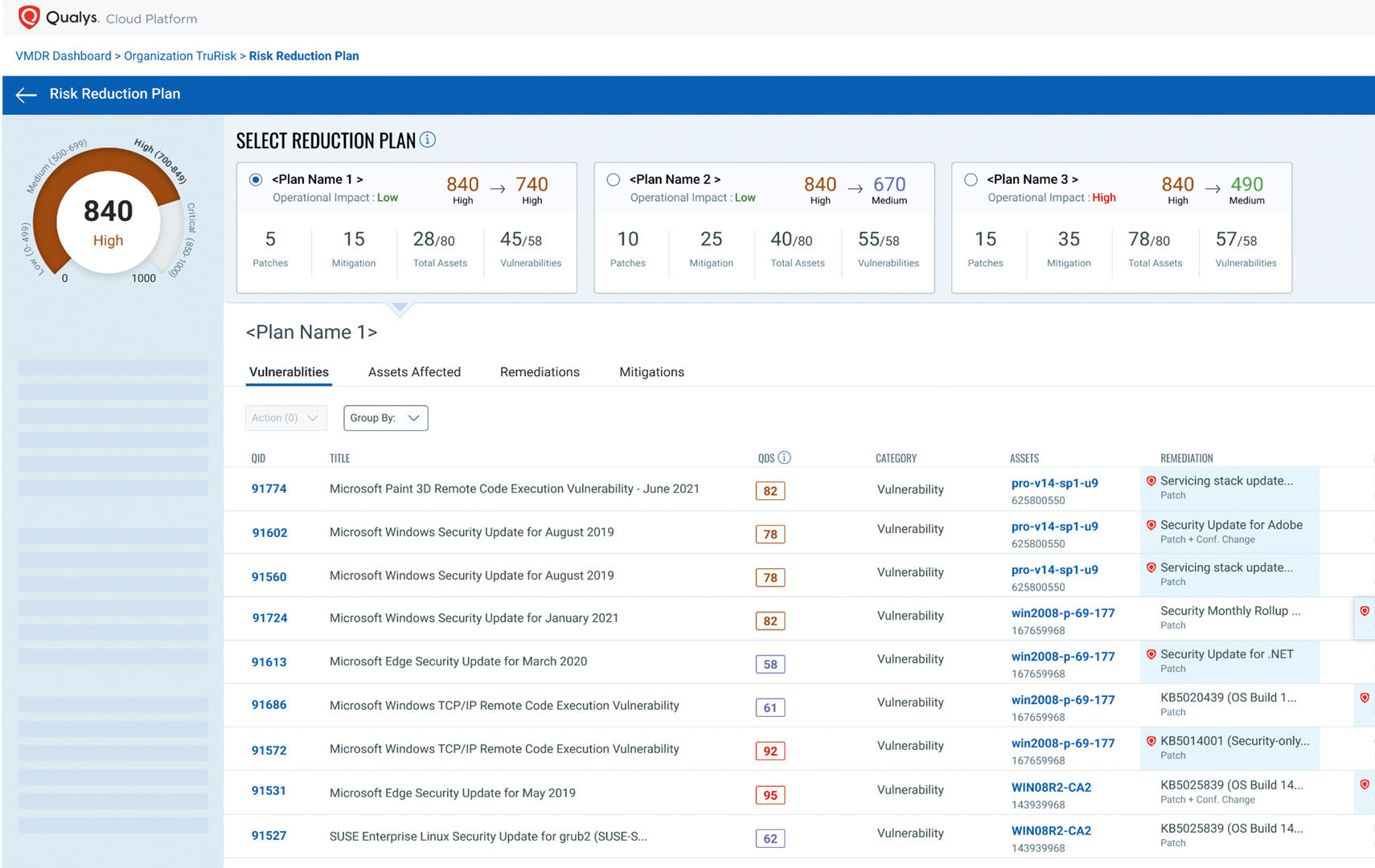
Prioritize vulnerabilities according to risk
Reduce critical vulnerabilities by 85% by focusing on what matters most with Qualys TruRisk transparent risk scoring.
Remediate 60% faster with a unified platform
Reduce MTTR by correlating vulnerabilities to available patches and leveraging remediation actions in a unified dashboard.
Optimize and operationalize IT security workflows
Pinpoint your most critical IT security threats, prioritize patching, and align IT and Security teams.
Always be audit-ready
Stay compliant while reducing risk with 850 out-of-the-box policies, 19,000 controls, 350 technologies, and 100 regulations and frameworks.