Qualys Threat Protection.
Pinpoint your most critical IT security threats and prioritize patching.
Industry-leading cloud service for taking full control of evolving threats and identifying what to remediate first
![Sodexo]()
Qualys not only highlights and ranks the vulnerabilities, but also makes precise recommendations for how best to remediate them – a critical advantage for teams in smaller business units that may have limited IT security resources.
John Bruylant Group CTO at Sodexo
Prioritize vulnerability remediation with automated and streamlined analysis

An introduction (01:36)
Demo: Search for a critical exploit (02:49)
Demo: Responding to a suspicious device (03:26)
Qualys Threat Protection Highlights

Mesh your IT asset inventory data with threat information
Threat Protection continuously correlates external threat data with vulnerability gaps in your IT environment, so your remediation prioritization decisions are rooted in concrete, up-to-date, applicable data, not in guesswork or arbitrary schedules. That way, you’ll stay a step ahead of hackers, patching bugs before bad guys exploit them.
-
Leverages the comprehensive IT asset cataloging of Qualys Global AssetView and the Six Sigma vulnerability detection accuracy of Qualys VMDR.
-
Lets you prioritize remediation with precision and nimbleness in a continual, contextual and automated manner, so the constant stream of bug disclosures don’t overwhelm you
-
Connects the dots and flags at-risk IT assets wherever they reside – on premises, in cloud environments or at mobile endpoints
-
Helps improve the efficiency of DevOps teams by bringing threat prioritization clarity into the application development and deployment lifecycle
-
Gives you a dynamic snapshot of all the vulnerabilities that exist in your IT environment at any given moment
-
Using actionable intelligence, allows you to assess how critical certain threat scenarios are in your organization’s specific context, since every IT environment is different


Look for specific assets and vulnerabilities
Threat Protection’s search engine gives you a powerful tool to look for specific assets and vulnerabilities. You can quickly and proactively identify systems across your entire environment exposed to specific threats, and take remediation steps right away. The search syntax is intuitive and the product has a query auto-complete feature. Threat Protection’s search engine lets you:
-
Craft ad hoc queries with multiple variables and criteria – such as asset class, vulnerability type, RTI, tag and operating system – so you can, for example, look for all vulnerabilities that have a severity rating of “5”, are easy to exploit and were disclosed within the last five days
-
Sort, filter and refine search results
-
Save any search, download results and share them
-
Turn queries you run regularly into permanent dashboard widgets whose information is dynamically updated in real time


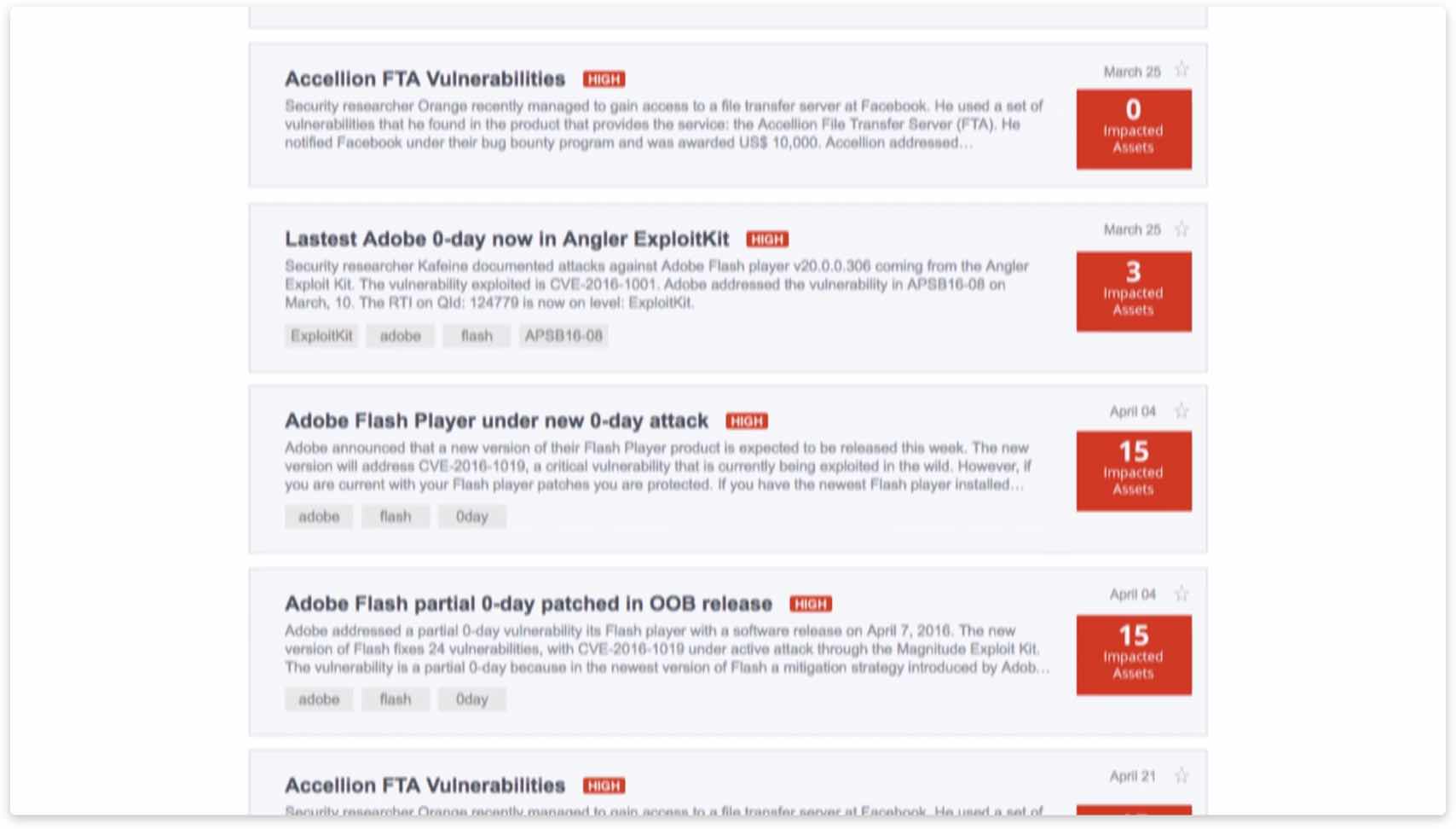
See a live feed of vulnerability disclosures
Threat Protection’s Live Threat Intelligence Feed keeps organizations up to date on the latest vulnerabilities and news, so you’re informed about new disclosures and about existing bugs whose risk severity has increased.
-
Plugs into the fire hose of external vulnerability disclosures, so you’re aware of the latest threats out in the wild
-
Displays how many of your IT assets are impacted by each disclosure, thanks to the product’s powerful data correlation capabilities.
-
Segments its content into different columns, including one for “high rated” items Qualys flags and another one for your handpicked “favorites” that you can pin to the feed UI
-
Lets you click on feed entries and drill down into details and more granular information of a particular vulnerability and of the affected IT assets
-
Allows you to fine-tune and narrow down the feed list by filtering and sorting items according to a variety of criteria, and download that set for remediation teams

Identify and weigh characteristics that intensify a vulnerability’s danger
Threat Protection appends real-time threat indicators (RTIs) to vulnerabilities, tapping findings from Qualys and external sources. Combining this threat data with internal criteria, such as an asset’s role, helps you prioritize remediation. For example, you can see all RTIs for vulnerabilities on a host, and drill down to specific vulnerabilities behind an RTI. Threat Protection RTIs include:
-
ZERO DAY – Vulnerabilities for which there is no vendor patch available and for which an active attack has been observed in the wild
-
PUBLIC EXPLOIT – Vulnerabilities whose exploit knowledge is well known and for which exploit code exists and is publicly available
-
ACTIVELY ATTACKED – Vulnerabilities that are being actively attacked in the wild
-
HIGH LATERAL MOVEMENT – Vulnerabilities that, if compromised, let the attacker propagate the attack broadly throughout the breached network
-
EASY EXPLOIT – Vulnerabilities that can be exploited easily, requiring few skills and little knowledge
-
HIGH DATA LOSS – Vulnerabilities whose exploit will yield massive data loss
-
DENIAL OF SERVICE – Vulnerabilities whose payload could overload or crash the compromised systems so that they become permanently or temporarily unavailable
-
NO PATCH – Vulnerabilities for which there isn’t a fix from the vendor
-
MALWARE – Vulnerabilities associated with malware infection
-
EXPLOIT KIT – Vulnerabilities for which an exploit kit is available


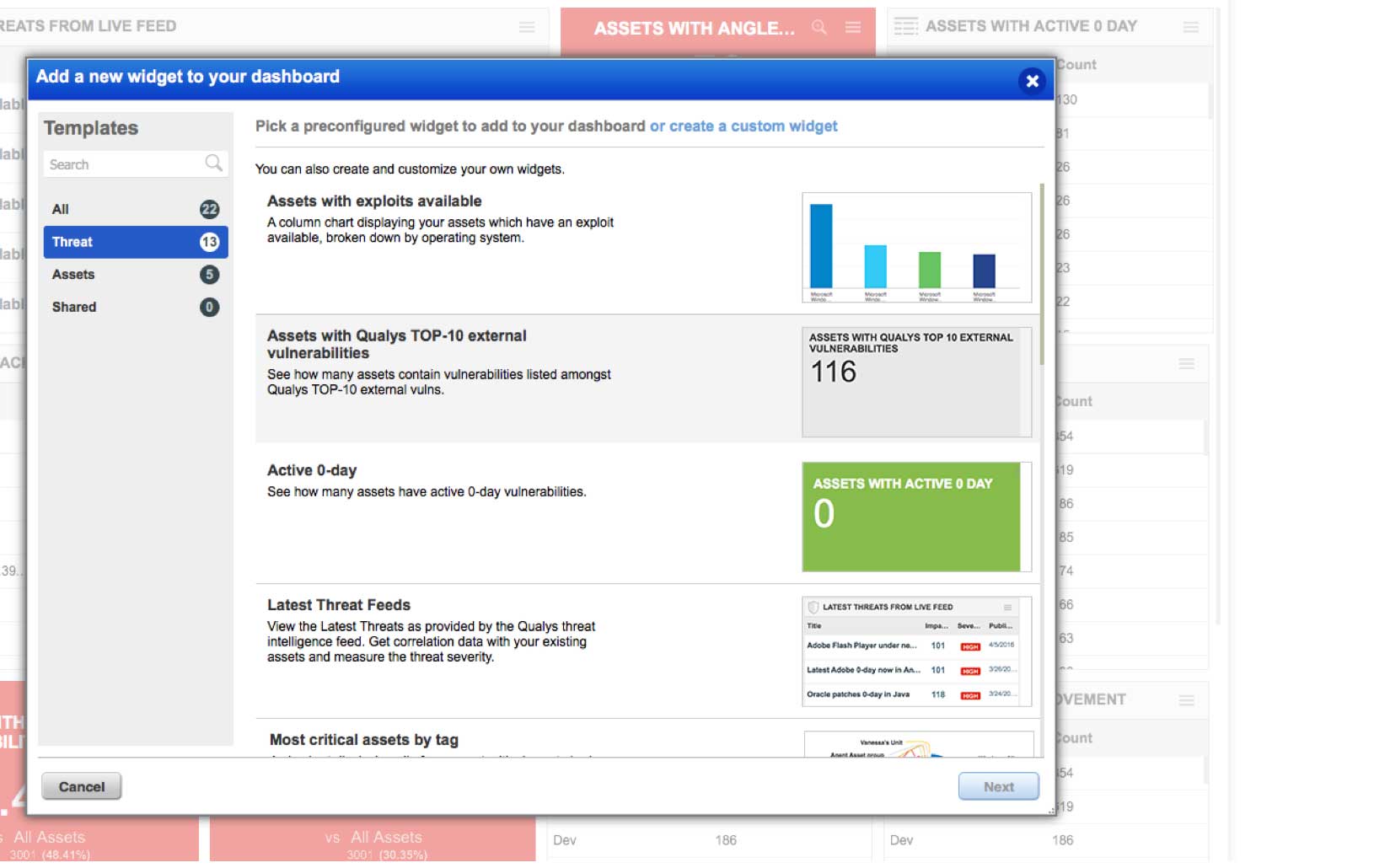
Centrally control and visualize the IT threat prioritization process
Customizable dashboards with dynamic widgets help you see your threat landscape in a holistic, consolidated way. You can drill down on the data, mine it for patterns, slice and dice it, aggregate it in custom reports and represent it graphically. This visualization and analysis yields deep insights for patch prioritization.
-
Includes a view for the live feed, as well as a variety of widgets based on RTIs, in the default dashboard setup
-
Allows you to create customized dashboards tailored for different IT and business roles
-
Lets you click through and access more information about the assets flagged as vulnerable
-
Allows you to create dashboard widgets manually or from any search query
-
Lets you set specific thresholds for widget data, and trigger certain actions in response, such as the widget’s background color changing from green to red
-
Sends you notifications when used in conjunction with Qualys Continuous Monitoring
-
Generates reports that you can quickly and easily share across the IT department with those responsible for patching the affected systems
-
Displays trend indicators in widgets, showing data fluctuations over time

See for yourself. Try Qualys for free.
Start your free trial today. No software to download or install. Email us or call us at 1 (800) 745-4355.

