Qualys Global AssetView: IT Asset Management App
You can’t secure what you can't see or don’t know.
It’s absolutely free! Unlimited assets.
No credit card needed.
Sign up below and you will receive an automated email with your login credentials.
Existing customer? Activate directly in your account.
By submitting this form, you consent to Qualys' privacy policy.
Knowing what’s on your global hybrid-IT environment is fundamental to security.
We made a promise to the world of security: make everything visible. Global AssetView is free of charge so that everyone around the world can benefit.
Fully cloud-based IT asset management easy to deploy, manage, and scales to millions of of assets


Highlights (01:20)
Demo presentation (07:12)
A new prescription for cyber security: Qualys Global AssetView (21:18)
Global AssetView Core features
Not your ordinary IT asset management tool.
Global AssetView Upgrades
Global AssetView Use cases
Just a few powerful things you can do

Global AssetView Use cases
Just a few powerful things you can do
-
Standardize on a single source of truth for all your teams
Qualys GAV automates the normalization and categorization of your inventory data – providing a single source of truth for your IT, security and compliance teams. Slice and dice this data with dynamic and customizable dashboards to fit all your visualization needs.
-
Identify assets ‘missed’ in your security and compliance program
Obtain in-depth visibility of these assets, including hardware and software details like firmware, OS, and applications and user information.
-
Detect unknown, unauthorized assets that connect to your network
Discover previously unknown assets – up to 60% – and obtain all their hardware and software details.
Trusted globally by companies large and small
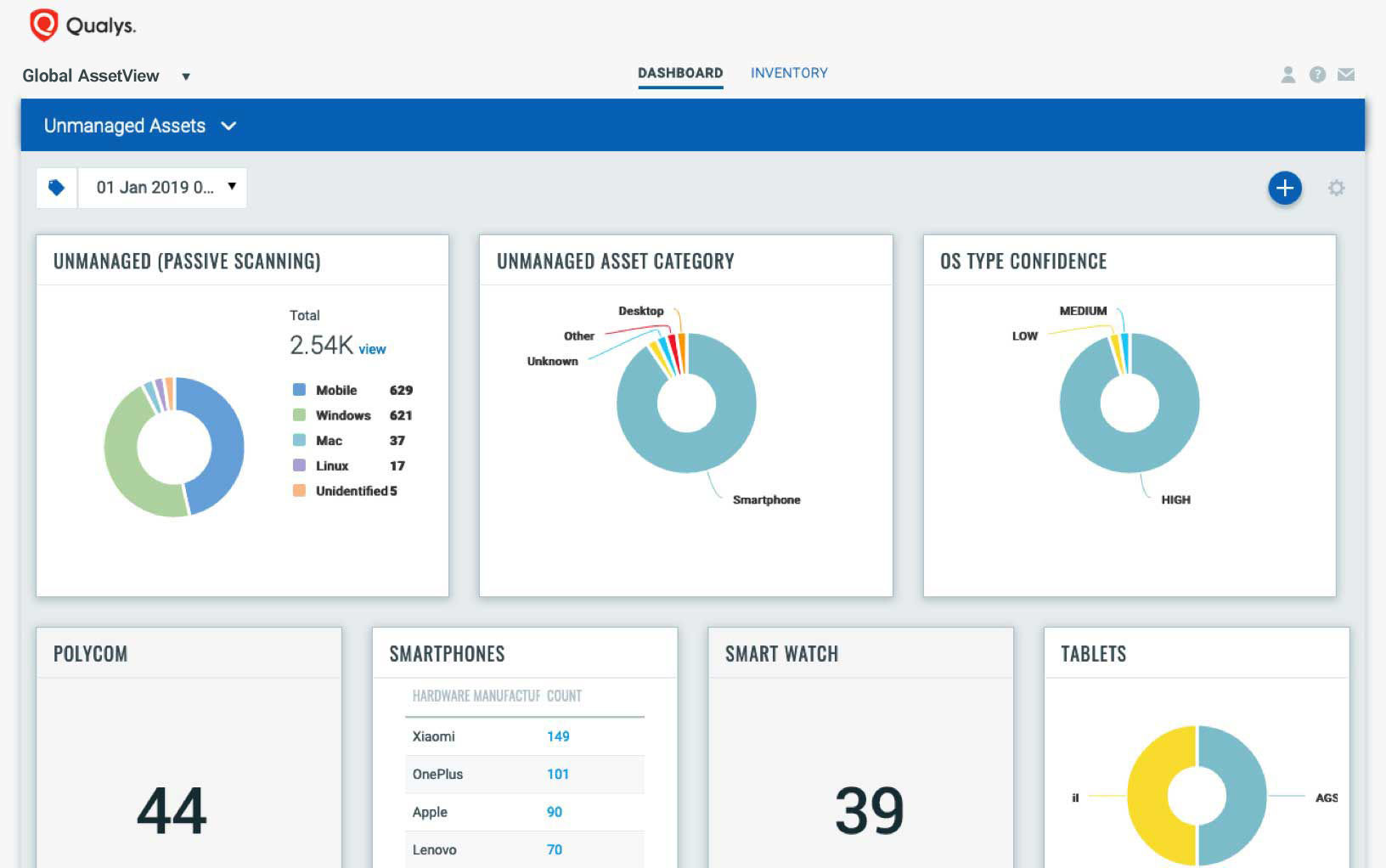
Continuous discovery of known and unknown IT assets
Global AssetView automatically discovers and classifies assets using both agent and agentless methods. It works in conjunction with the Enterprise TruRisk Platform and Qualys sensors (scanners, cloud connectors, container sensors, cloud agents, passive sensors and APIs) to continuously discover assets. Other characteristics of Qualys’ automated discovery include:
- Flexible: Known and unknown asset tracking that covers both managed and unmanaged devices
- Comprehensive collection methods: Covers all bases. Uses both agentless and agent-based collection for active and passive scanning of your assets
- Automated: Assets are discovered automatically. Quickly setup lightweight all-purpose Cloud Agents for a deep view of assets
- Non-intrusive: Runs in the background with no impact to the network and applications
- Continuous: Up-to-date and continuous inventory collection including changes and transient devices
- Indexed: All data collected is indexed for quick retrieval
- Integrated: Data collected is available for all Qualys Security and Compliance Cloud Apps
-
Discovered data includes:
- Physical and virtual appliances in on-premises environments
- Mobility assets
- Cloud IaaS and PaaS instances in cloud, including containers
- IoT and OT devices
- Hardware and software data discovery: collected information includes listing system and hardware details, running services, open ports, installed software and user accounts

Clean, reliable data
Automated normalization and classification of asset data maps raw asset data to Qualys product catalog to obtain clean and reliable data. The product catalog is continuously curated with a focus on completeness, relevance and data quality. This process transforms the global IT asset inventory into multidimensional and structured information, for better business decision-making.
-
Normalization includes standardizing of asset data in your environment for every manufacturer name, product name, model, software version and much more. The normalized data provides clean and reliable data for accurate decision making
-
Automatic classification of all software which separates applications from system software, such as OS patches and drivers. Every asset is classified in meaningful, functional categories based on hardware and software
-
Enrichment automatically populates your IT asset inventory with asset metadata that can’t be discovered otherwise, such as hardware and software product release dates, end-of-life dates, license categories, and more. These attributes provide IT organizations with multiple lenses that expand asset visibility in new, meaningful ways

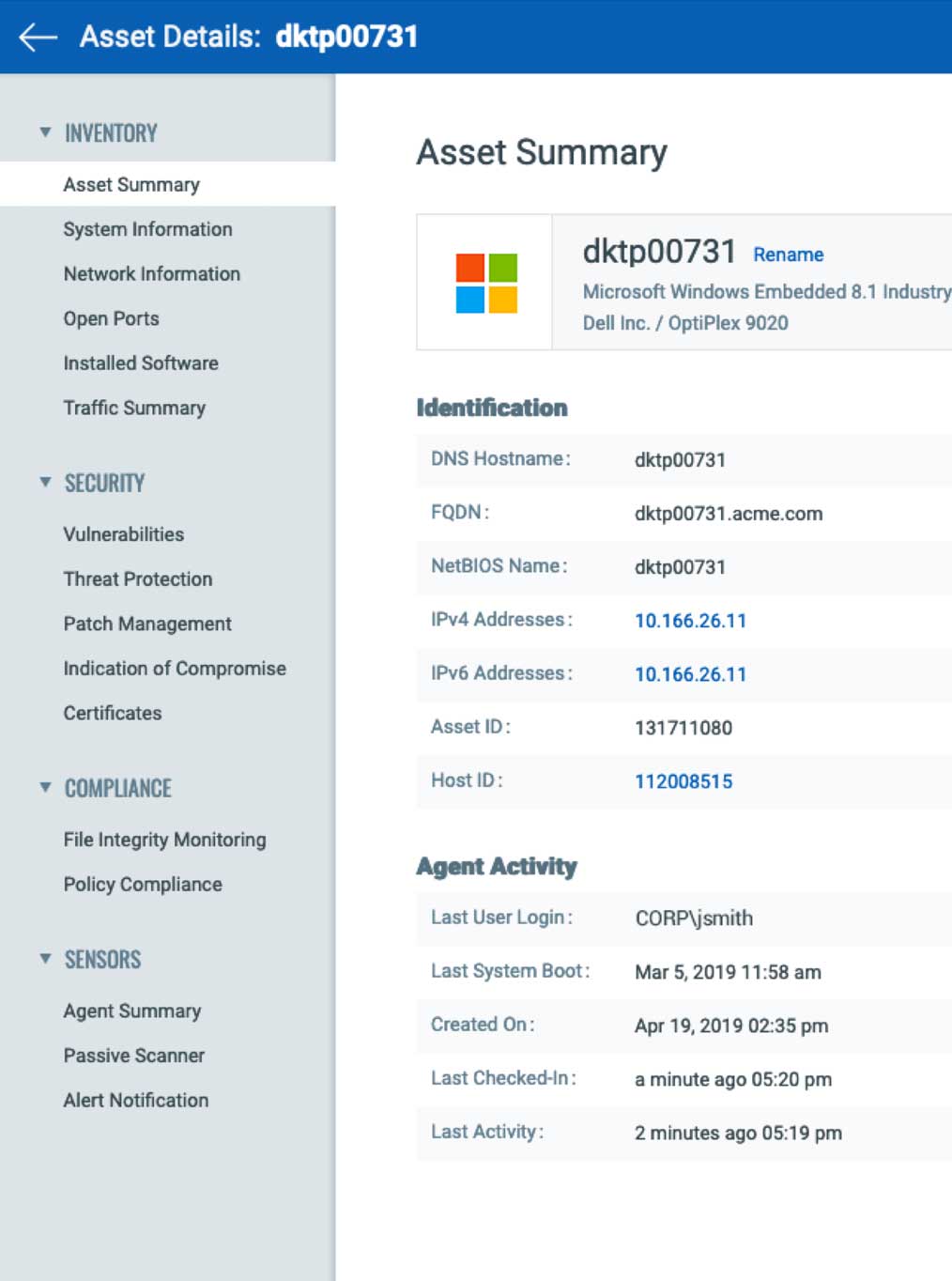
Detailed IT asset information
Qualys gives you deep visibility into the assets granting you a detailed, multidimensional view of each one that encompasses both its IT and security data. You can flag issues such as configuration problems, security risks, IT policy violations and regulatory non-compliance with an asset profile that includes a wealth of data such as:
-
Hardware specs
-
Installed software, including applications, OS, drivers, utilities and plug-ins
-
Network connections
-
User information and context
-
Services, file systems, running processes
-
Virtualized environment details, such as the constant proliferation of internal and external images
-
Geographic location and time zone


Search any IT asset in seconds!
Has a powerful search engine that lets you craft simple or advanced queries combining multiple asset criteria returning results instantly, so you can find out in 2 seconds:
-
How many unmanaged devices are in my environment?
-
How many IoT devices are in my environment?
-
How many servers are in my environment, and what servers are running an OS that its vendor recently stopped supporting?
-
How many databases are running in my data centers?
-
Which IT assets have a particular piece of software installed?
-
How many Lenovo laptops running the latest version of Windows 10 and located in my India office have a particular vulnerability?


Tag your IT assets
Not all assets carry the same weight within your organization. Tag your assets by putting relevant labels on them and organizing them in a multitude of ways. For example, you can specify which assets fall within the scope of PCI DSS (Payment Card Industry Data Security Standard) compliance.
-
Supports tagging of assets for easy labeling and identification, instantly adding business context to your inventory
-
Gives you the ability to apply tags manually or configure rules and parameters for automatic tagging
-
Supports creating any kind or number of hierarchies and giving assets as many tags as you want
-
Calculates criticality based on an asset’s aggregated and consolidated system, security, and compliance data, as well as established hierarchies and priorities
-
Global AssetView attribute tags are available for use in other Qualys cloud apps. This enables you to discover unmanaged assets that are vulnerable, or EoL devices that are non-compliant, etc.

Create your account today. It’s free! Unlimited assets.
Fully cloud-based, it’s easy to deploy and manage. Schedule a demo or request call back. Email us or call us at 1 (800) 745-4355.

Security & compliance that’s built in
Upgrade to run continuous security and compliance assessments of your cataloged inventory. Since Qualys Global AssetView is part of the Enterprise TruRisk Platform, enabling Qualys’ industry leading security and compliance capabilities is as easy as flipping a switch.
-
Vulnerability Management: identify and sort all known and potential vulnerabilities with Six Sigma (99.99966%) accuracy
-
Threat Protection: pinpoint evolving threats and identify what to remediate first
-
Patch Management: deploy patches wherever an agent has been installed
-
Endpoint Detection & Response: hunt, investigate, detect, and respond to threats before a breach or compromise can occur
-
Certificate Assessment: assess digital certificates and TLS configurations
-
File Integrity Monitoring: track file changes
-
Policy Compliance: assess compliance with internal and external policies

IT Asset Management Resources
GAV and CSAM features
Global AssetView (GAV) is free with any number of agents & passive scanners to give you baseline visibility of your asset inventory.
CyberSecurity Asset Management (CSAM) adds context for security-centric visibility with detection of security gaps and CMDB integration, plus alerting and response.
| FEATURE | GAV | CSAM | |
|---|---|---|---|
| Get complete visibility into your environment Discover and inventory all your assets Learn More |
|||
| View categorized and normalized hardware and software information Standardize your inventory Learn More |
|||
| Define criticality and find related assets Add business context through dynamic tagging Learn More |
|||
| Discover all known and previously unknown internet-facing assets Get 100% visibility and improved cyber risk management Learn More |
|
||
| Find and upgrade unsupported software and hardware Know product lifecycle and support information Learn More |
|||
| Eliminate unauthorized software from your environment Quickly identify assets requiring attention Learn More |
|||
| Be informed about assets requiring attention Receive notifications to review and define actions Learn More |
|||
| Inform stakeholders about health of your assets Create custom reports Learn More |
|||
| Easily keep your CMDB up to date Enable 2-way integration to sync with ServiceNow CMDB Learn More |
|
||
| Orchestrate automated remediation workflows with VMDR 2.0 Integrated endpoint detection & response, vulnerability & patch management, and policy compliance |
|
Create your account today. It’s free! Unlimited assets.
Fully cloud-based, it’s easy to deploy and manage. Schedule a demo or request call back. Email us or call us at 1 (800) 745-4355.










