Cloud Workload Protection (CWP)
Your Cloud. De-risked.
Comprehensive and flexible vulnerability scanning with Six Sigma accuracy and context-based risk prioritization.
Scan for vulnerabilities in your cloud environment, virtual machines, containers, and serverless workloads
Detect vulnerabilities across all cloud resources with Six Sigma level accuracy from over 180K vulnerabilities from 25+ threat sources.
De-risk your cloud with CWP – an integral part of Qualys TotalCloud™ – an AI-powered CNAPP solution
Detect vulnerabilities in less than 10 minutes
Rapidly assess all your cloud resources for vulnerabilities (including open-source software (OSS) transient and ephemeral resources) with a risk-based view in under 10 minutes.

Scan with flexibility and precision
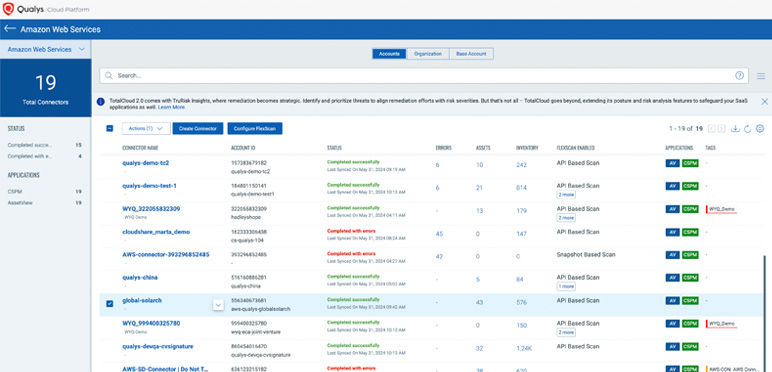
Get a unified and comprehensive view of vulnerabilities across your cloud environment with Qualys FlexScan™—including no-touch, agentless, API- and snapshot-based scanning, plus agent- and network-based scanning.

One prioritized view or risk, based on context
Reduce critical vulnerabilities by up to 85% with business context and cyber risk assessment. Get a holistic view of risk by correlating unique indicators from diverse Qualys sources such as Six-Sigma vulnerability detection, AI-powered threat detection, externally exposed assets, asset criticality, and more.

Supply chain software security
Advanced scanning capabilities for detecting vulnerabilities in OSS components at both build and runtime stages.
Run time scanning of vulnerabilities
Enhanced scanning at build time enables developers to identify and mitigate vulnerabilities early in the development cycle, significantly reducing the risk of deploying vulnerable code.
Understand and manage cybersecurity risk
Quantify risk across vulnerabilities, assets, and groups of assets to proactively mitigate risk exposure and track risk reduction over time.
Automate remediation with no-code workflows
Save time by automating and orchestrating operational tasks for vulnerability management and patching with Qualys Flow.
Explore TotalCloud CWP Product Tours
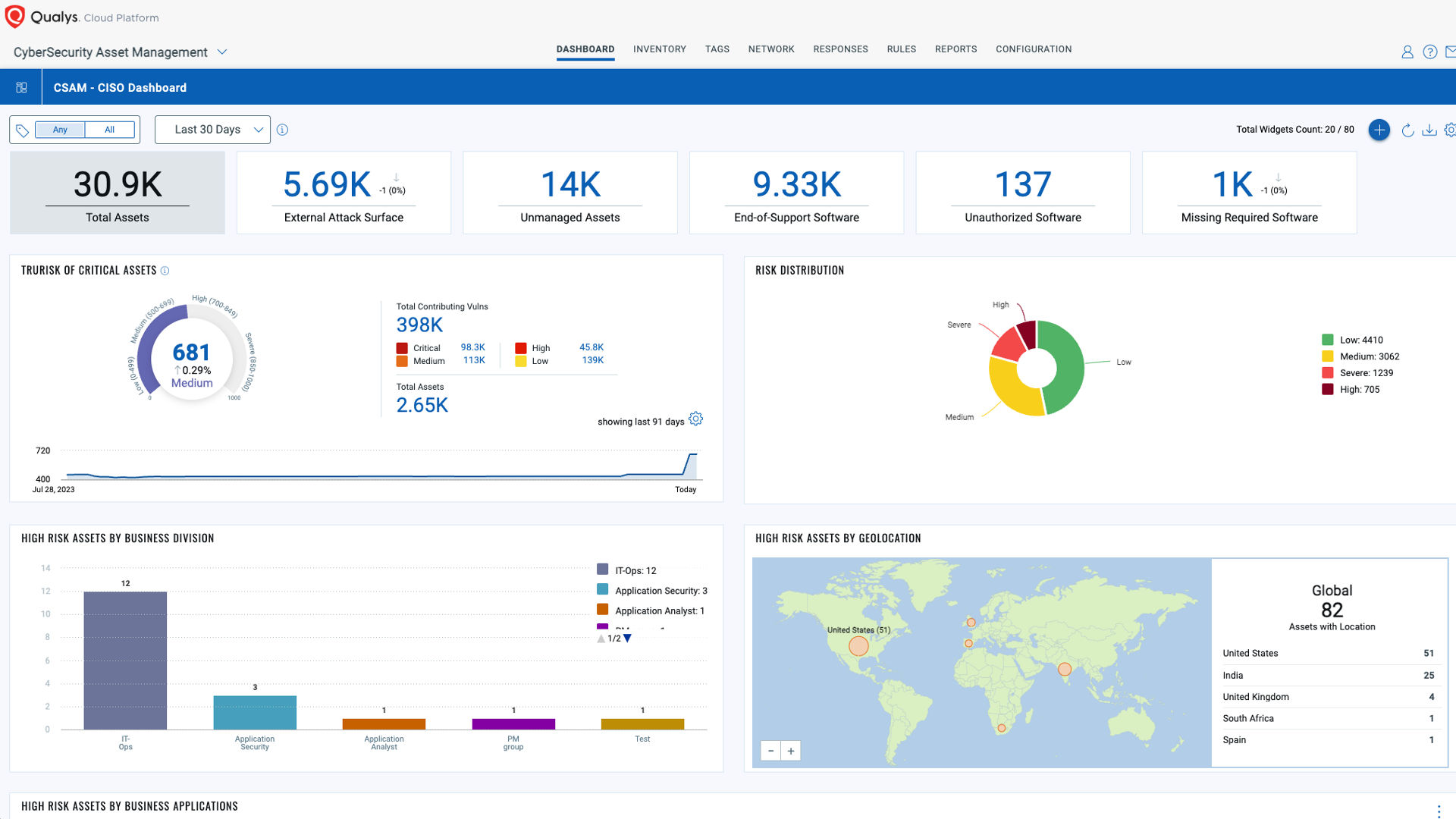
Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.