TruRiskTM Platform
Interactive Guided Tours Showcasing Essential Features of the Qualys Enterprise TruRisk Platform
Explore VMDR Product Tours
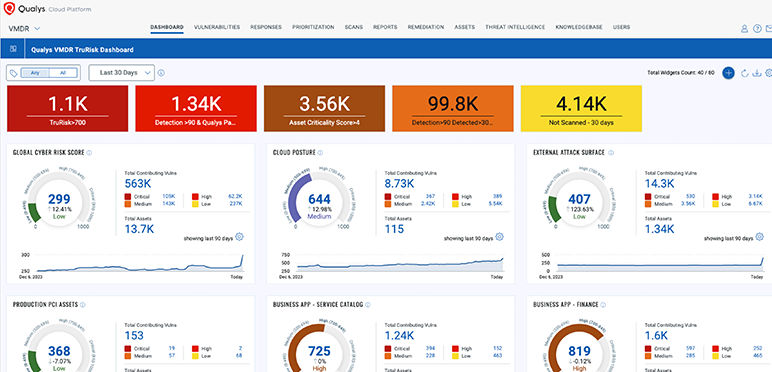
Vulnerability outbreak case
Understand the potential impact of any zero-day vulnerability to prioritize and take action quickly.
DID YOU KNOW?
VMDR detects vulnerabilities up to 6x faster than competitive solutions.
What does it contain?
- Identify a high-risk vulnerability from the Threat Detection Feed
- Quickly query for assets impacted by the vulnerability
- Identify missing patches to initiate remediation steps
- Quickly deploy a patch job to reduce risk to critical assets
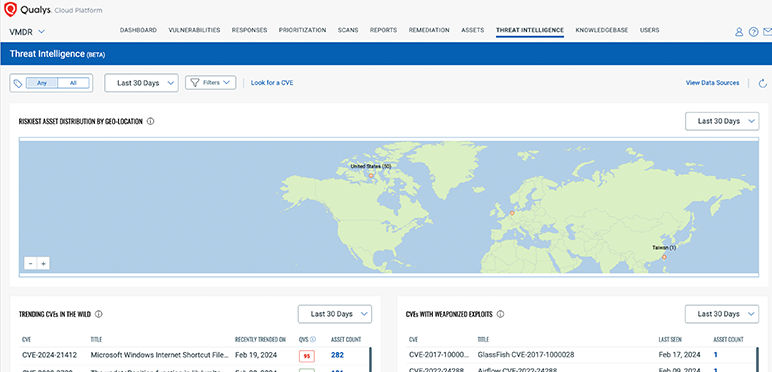
Prioritize the risk and not just vulnerabilities
Pinpoint the cyber risk by accounting for multiplying factors beyond CVSS scores.
DID YOU KNOW?
692 million vulnerabilities are prioritized incorrectly by using CVSS and EPSS alone.
What does it contain?
- Understand the difference between CVSS score and business risk
- Filter by Qualys Detection Score (QDS) to focus on what matters most
- See the risk factors contributing to critical QDS scores
- Query for missing patches and deploy quickly
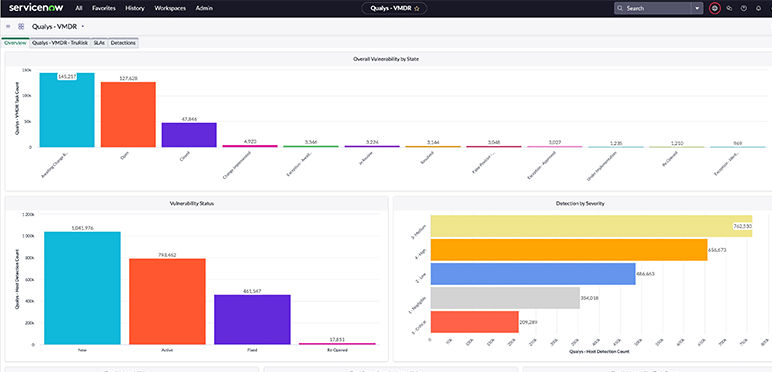
Close the remediation loop with itsm integrations
Meet your targeted SLAs for vulnerabilities with auto-assignment.
DID YOU KNOW?
You can auto-assign ITSM tickets with 96% accuracy based on mapping to Qualys tags.
What does it contain?
- An overview of Qualys ITSM integrations and use cases
- How to close the remediation loop by integrating Patch Management
- Grouping vulnerabilities for automated ticket routing and SLA assignments
- Deploying automated patch jobs to reduce MTTR
Explore CSAM Product Tours

De-risk your external attack surface
Continuously discover and monitor internet-facing enterprise systems and associated exposure.
DID YOU KNOW?
40% of the external attack surface is unknown to organizations.
What does it contain?
- Find and Assess internet-facing assets across your global subsidiaries.
- Prioritize discovered vulnerabilities and related threats.
- Alert your SecOps teams of misconfigurations such as risky ports.
- Executive-level risk reports for potential M&A.
- Automatically enrich your CMDB for single source of truth.
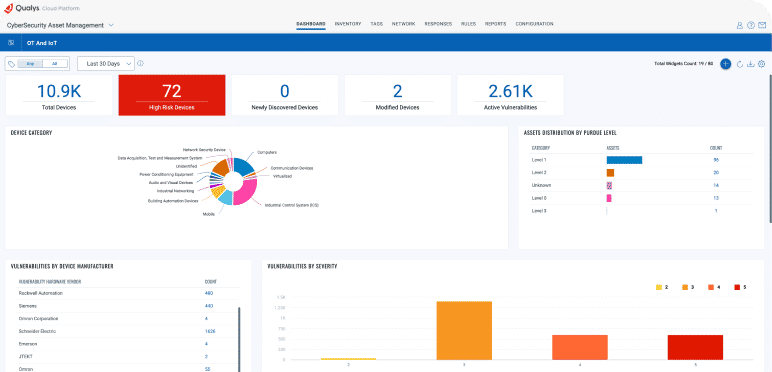
Discover 30% more unmanaged IoT/OT assets
Organizations are increasingly reliant on connected devices, which security teams are often blind to.
DID YOU KNOW?
69% of organizations said they experienced a cyber attack resulting from an exploit of an unknown or unmanaged asset.
What does it contain?
- Discover IoT/unmanaged assets and rogue devices in real time.
- Discover Operational Technology (OT/ICS) in real-time.
- Analyse connections & network traffic to understand asset behaviour and communication.
- Correlate, normalise & deduplicate assets across multiple sensors and 3rd-party sources.
- One-click and automated workflows to tag and organise assets for safe vulnerability scans.
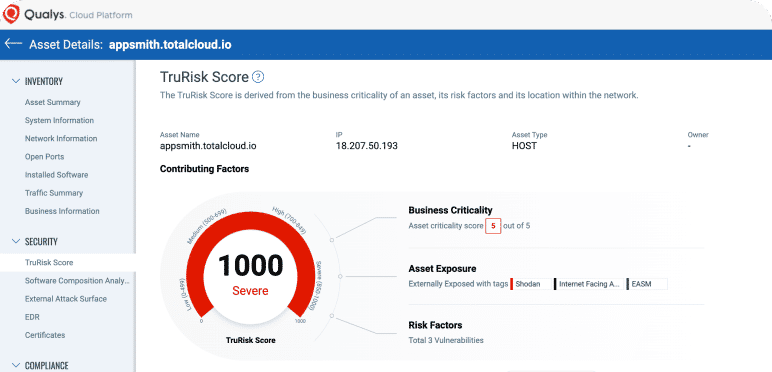
Prioritize with complete inventory risk assessment
Prioritize risk with business context across your attack surface, beyond just detecting vulnerabilities.
DID YOU KNOW?
CSAM offers business context and calculates TruRisk based on unique factors like risky ports and absent security agents.
What does it contain?
- Assess the TruRisk of assets using risk factors discovered by CSAM.
- Sync with CMDB and other third-party sources to add business context to assets.
- Define and extract custom attributes to drive more accurate TruRisk Scoring.
- Automatically tag assets and groups of assets for effective reporting and dashboards.
Explore PM Product Tours
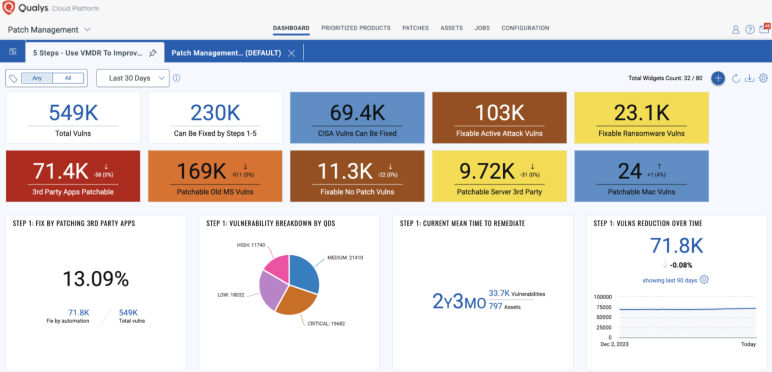
Automate updates for continuous risk remediation
Implement a proactive policy for the timely patch of applications that pose ongoing risks to your environment.
DID YOU KNOW?
CISA advises continuous patching of software that processes internet data, including web browsers, browser plugins, and document readers.
What does it contain?
- Assess software that have introduced maximum vulnerabilities in last 2 years for your environment
- Create zero touch patch job for browsers, document reader software
- Schedule it for daily execution
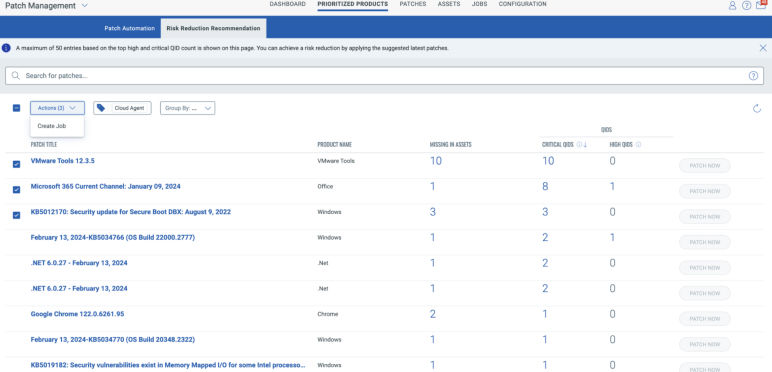
Optimize patch deployment for risk remediation
Identify, test and deploy top patches that will reduce the most TruRisk.
DID YOU KNOW?
SecOps and ITOps invest significant time in identification and patching, yet it frequently does not effectively reduce risk.
What does it contain?
- Assess patches that can help to reduce most risk in the environment
- Create patch job against the patch that will be targeted to multiple assets to remediate the critical vulnerabilities
- Notify Security Analyst and IT team members about the Job start and completion
Explore PM Product Tours

Automate updates for continuous risk remediation
Implement a proactive policy for the timely patch of applications that pose ongoing risks to your environment.
DID YOU KNOW?
CISA advises continuous patching of software that processes internet data, including web browsers, browser plugins, and document readers.
What does it contain?
- Assess software that have introduced maximum vulnerabilities in last 2 years for your environment
- Create zero touch patch job for browsers, document reader software
- Schedule it for daily execution

Optimise patch deployment for risk remediation
Identify, test and deploy top patches that will reduce the most TruRisk.
DID YOU KNOW?
SecOps and ITOps invest significant time in identification and patching, yet it frequently does not effectively reduce risk.
What does it contain?
- Assess patches that can help to reduce most risk in the environment
- Create patch job against the patch that will be targeted to multiple assets to remediate the critical vulnerabilities
- Notify Security Analyst and IT team members about the Job start and completion
Explore WAS Product Tours
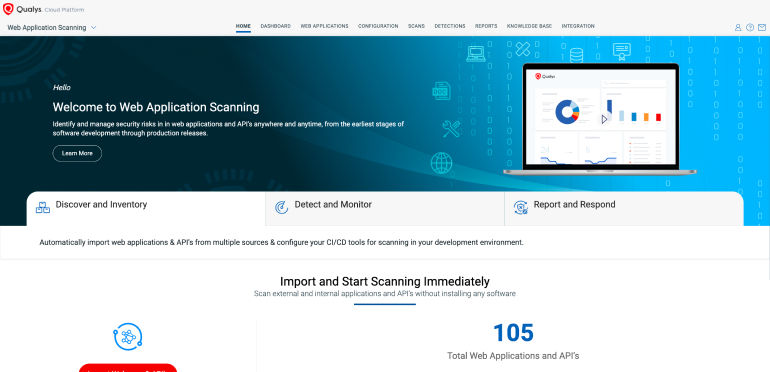
Discover web apps & APIs across your attack surface
Get continuous, automated scanning to discover and secure web apps & APIs across cloud & on-prem.
DID YOU KNOW?
60% of organisations struggle to identify all web applications, leaving them vulnerable to security risks.
What does it contain?
- Identify forgotten, orphaned, or unknown web apps across internal and external networks.
- Uncover all web applications, including those on open HTTP ports, for enhanced security coverage.
- Organize and tag apps for better access control and reporting.
- Seamless integration with CSAM/EASM for external attack surface management.
- Access a central command centre for real-time insights.
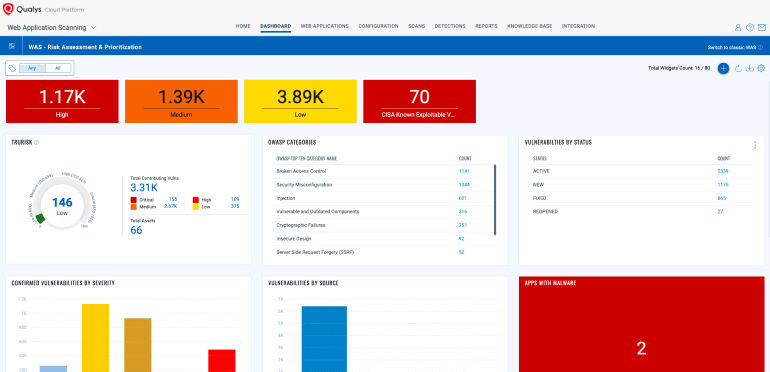
De-risk your attack surface with continuous monitoring
Detect vulnerabilities, misconfigurations, PII exposures & OWASP risks across web apps & APIs.
DID YOU KNOW?
The average cost of a PII data breach globally is $4.35M USD, and it rises to $9.44M USD on average in the US.
What does it contain?
- Run deep scans to identify vulnerabilities, misconfigurations, OWASP Top 10, CISA Known Exploited Vulnerabilities, SQLi, XSS, runtime risks in APIs & more.
- Get risk prioritization based on Qualys TruRisk™ score.
- PII exposure and web malware detection ensures compliance with GDPR, HIPAA, PCI DSS.
- Get a unified view with consolidated scan results from third-party manual PEN test tools.
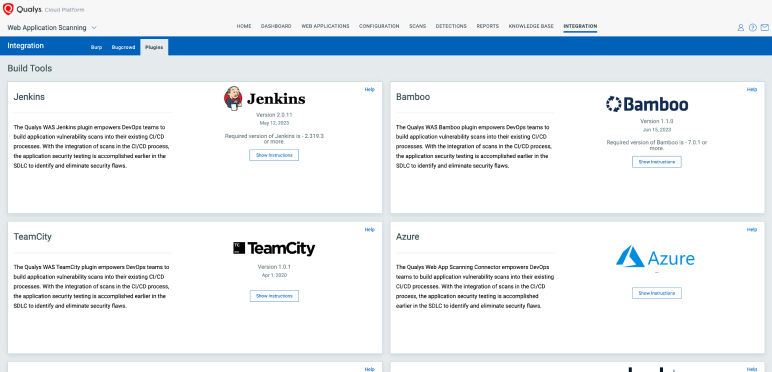
Streamline AppSec for faster vulnerability remediation
Integrate web app scans in SDLC, using ITSM for quick remediation and fostering DevSecOps collaboration.
DID YOU KNOW?
Integrating security practices early in the SDLC can reduce MTTR by 70%, ensuring faster threat mitigation.
What does it contain?
- Detect code issues early with CI/CD integration in Azure, Jenkins, Bamboo, Team City, GitHub.
- Customize build pass/fail criteria based on severity.
- Auto-create tickets for tasks in ServiceNow AVR & Jira.
- Gain insights with a single dashboard for monitoring scans, vulnerabilities, and malware trends.
- Track Time to Remediate (TTR) to measure security program effectiveness.
Explore EDR Product Tours
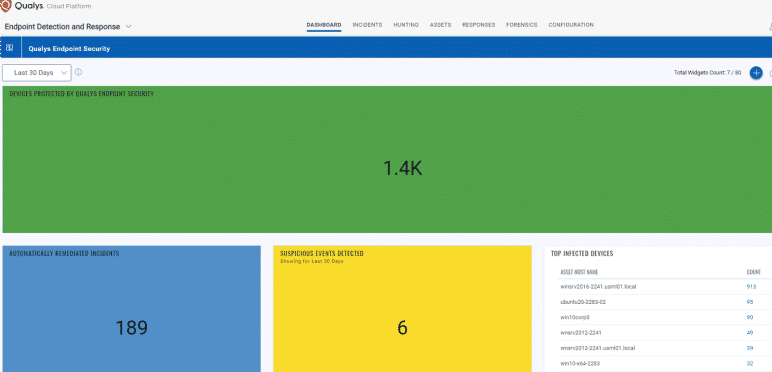
Stop Known and unknown attacks
Automatically protect Endpoints from malware such as ransomware, phishing and other forms of attacks.
DID YOU KNOW?
Qualys uses machine learning, memory protection, and network intrusion detection to automatically halt advanced attacks.
What does it contain?
- Prevent access to malicious websites
- Automatically prevent download of malicious files
- Blocking of ransomware based on behavior
- Policy configurations
- Reporting
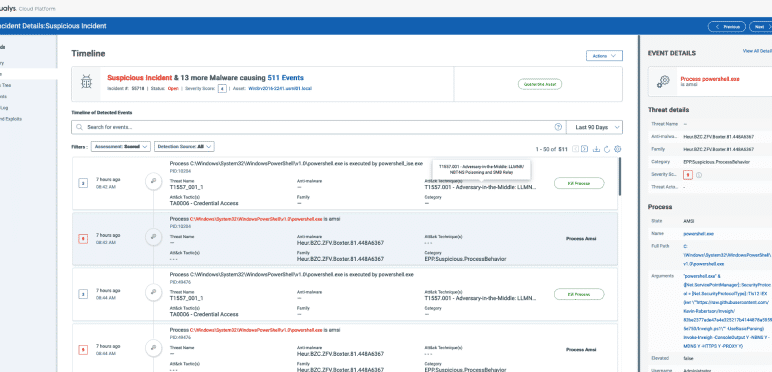
Investigate and respond to suspicious activities
Qualys EDR detects potential threats while also automating investigation and response.
DID YOU KNOW?
30% of Alerts get unnoticed due to lack of proper prioritization and context.
What does it contain?
- Identify suspicious activities
- Automatic assignment of severity score
- Deep visibility and context of the incident- MITRE techniques, process tree, malware family, CVEs, Patching Status, Asset Business Context
- Ability to respond - Isolate host, remote shell, forensics data
- Ability to set auto-response
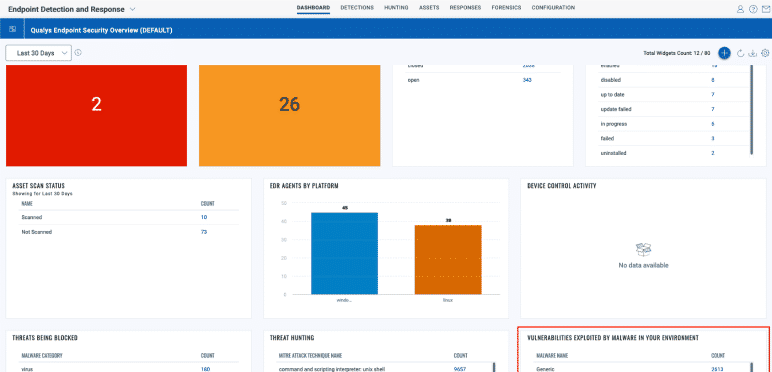
Address the root cause to prevent future compromise
Qualys Detection & Response is the only solution in the industry that unifies multiple context vectors around asset criticality, vulnerabilities, and system misconfigurations associated with detected threats.
DID YOU KNOW?
Up to 95% of ransomware related vulnerabilities are patchable by Qualys for preventing future attacks.
What does it contain?
- Reducing risk of current and future attacks
- Map CVE's and Misconfigurations to active threats
- Unified root cause analysis and incident response
- Minimize attack surface and harden assets in real time
Explore FIM Product Tours
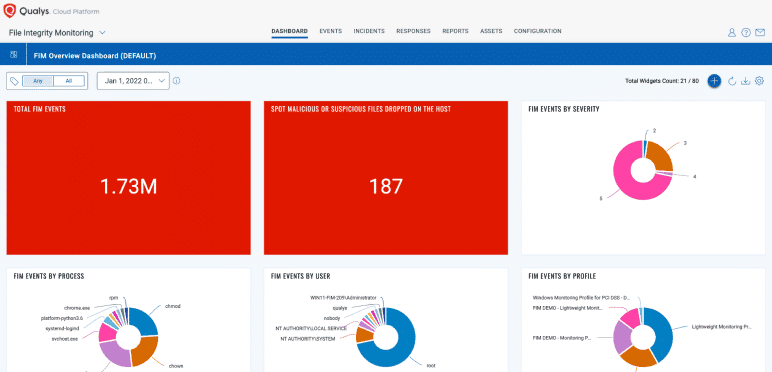
Readiness for PCI DSS 4.0 FIM requirements
Organizations handling credit cards must comply with PCI DSS 4.0 by implementing FIM.
DID YOU KNOW?
Verizon's Payment Security Report reveals that 9.8% of organizations fail audits due to lacking File Integrity Monitoring (FIM).
What does it contain?
- Pre-defined Library of FIM Profiles
- Thorough and detailed record of auditable events
- Compliance Reporting
- Automated Incident Management
- Data retention with immediately accessible data
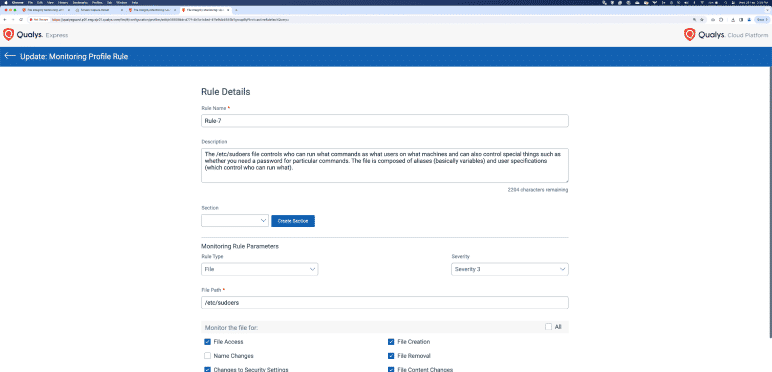
Start real-time File Access Monitoring (FAM)
Security practice that involves tracking and logging access to sensitive files.
DID YOU KNOW?
Compliance regulations such as GDPR, CCPA, SOX, HIPAA mandate monitoring of sensitive data access by organisations.
What does it contain?
- Enable FAM for critical files
- Search for file access activities by non-privileged users
- Analyse file access events
- Create automated incidents for file access activities by non-privileged users
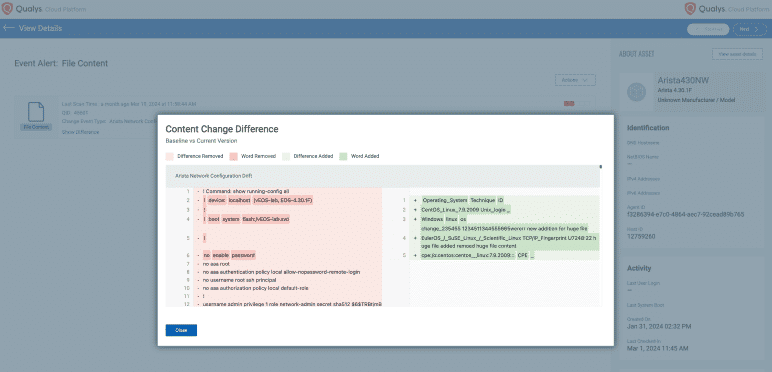
Agentless FIM - Enable FIM on network devices
When a network device's configuration changes, logging the modification and timestamp is crucial.
DID YOU KNOW?
Lacking measures to detect changes in network configurations can result in compliance failures with regulatory standards.
What does it contain?
- To enable FIM on network devices, add them under scan-based assets
- View baseline event on first scan
- Receive alerts on network configuration changes and precisely pinpoint differences during routine scans
Explore CS Product Tours
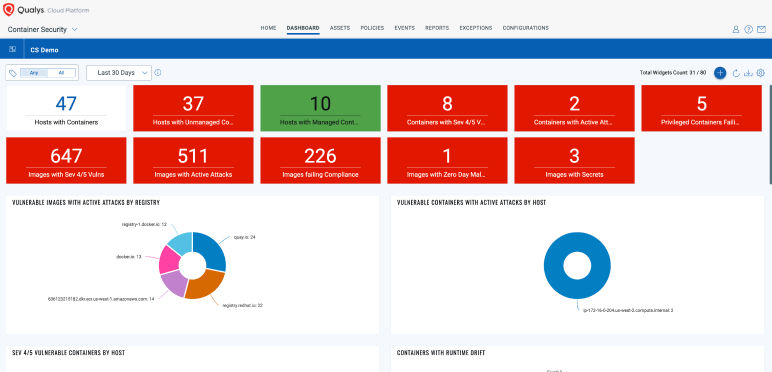
Discovering shadow containerized workloads
Finding unknown container workloads that are popping up and not in your risk management radar.
DID YOU KNOW?
According to Deloitte, about 20-30% of security incidents occur due to bind spots in network and application visibility
What does it contain?
- Setting up a tracking dashboard
- Discovering blind spots
- Download General Sensor
- Filing a JIRA ticket with SLA to ensure Qualys General Sensor is installed
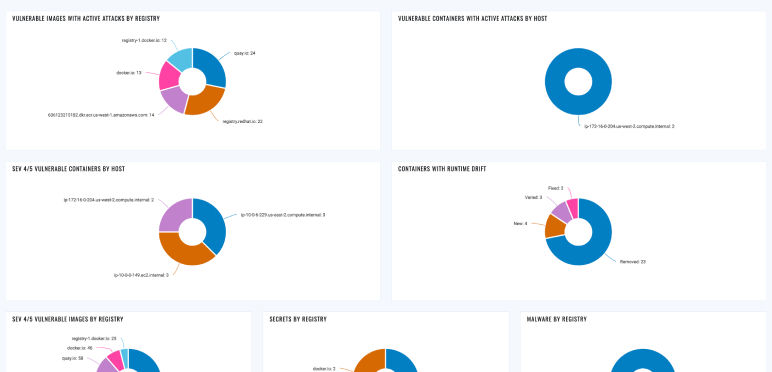
Patching vulnerable containerized workloads
Assessing the risk from your containerized workloads and patching the riskiest ones.
DID YOU KNOW?
The exploitation of vulnerabilities as an initial point of entry almost tripled from the previous year, accounting for 14% of all breaches, according to Verizon’s 2024 Data Breach Investigations Report
What does it contain?
- Setting up a tracking dashboard
- Assessing the riskiest containers
- Collecting patch relevant information
- Filing a JIRA ticket with SLA
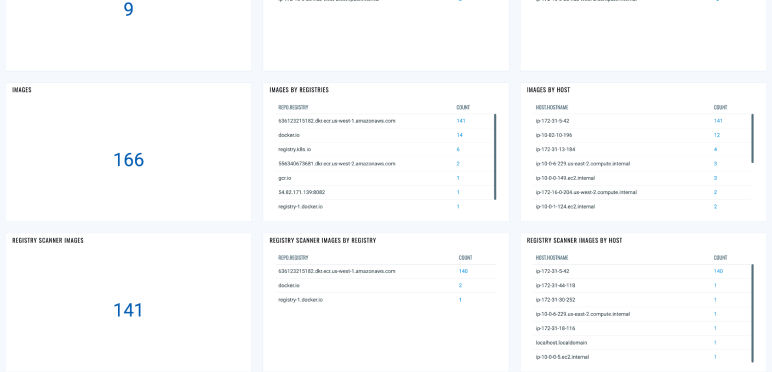
Fixing insecurely configured containers
Ensuring container workloads meet industry standard benchmarks for secure configuration (CIS for Docker).
DID YOU KNOW?
The Verizon Data Breach Investigations Report (DBIR) states that 13% of all data breaches analyzed were caused by misconfiguration errors
What does it contain?
- Setting up a tracking dashboard
- Assessing the riskiest containers
- Filing a JIRA ticket with SLA
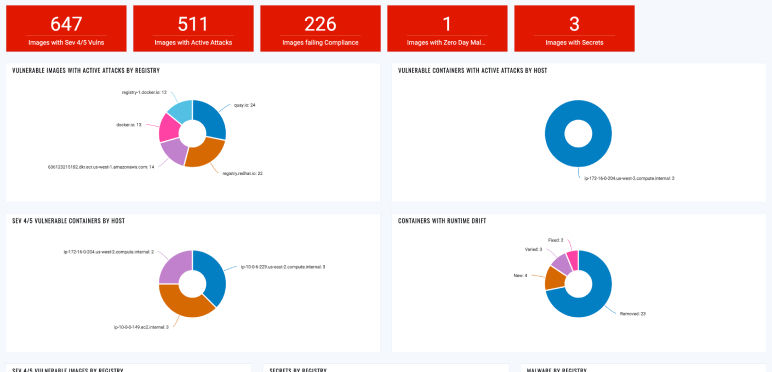
Patching vulnerable images
Assessing the risk from images in your container image registry and patching the riskiest ones.
DID YOU KNOW?
The exploitation of vulnerabilities as an initial point of entry almost tripled from the previous year, accounting for 14% of all breaches, according to Verizon’s 2024 Data Breach Investigations Report
What does it contain?
- Setting up connector for registry
- Setting up a tracking dashboard
- Assessing the riskiest images
- Documenting the patch steps
- Filing a JIRA ticket with SLA
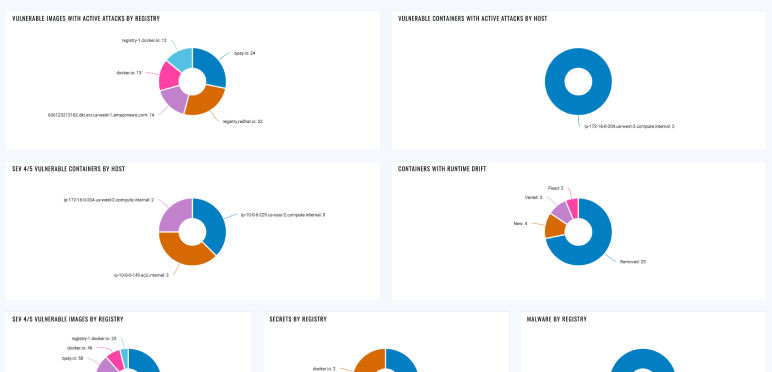
Fixing insecurely configured images
Ensuring container images in registry meet industry standard benchmarks for secure configuration (CIS for Docker).
DID YOU KNOW?
The Verizon Data Breach Investigations Report (DBIR) states that 13% of all data breaches analyzed were caused by misconfiguration errors
What does it contain?
- Setting up a connector for registry scanning
- Setting up a tracking dashboard
- Assessing the riskiest images
- Documenting the remediation steps.
- Filing a JIRA ticket with SLA
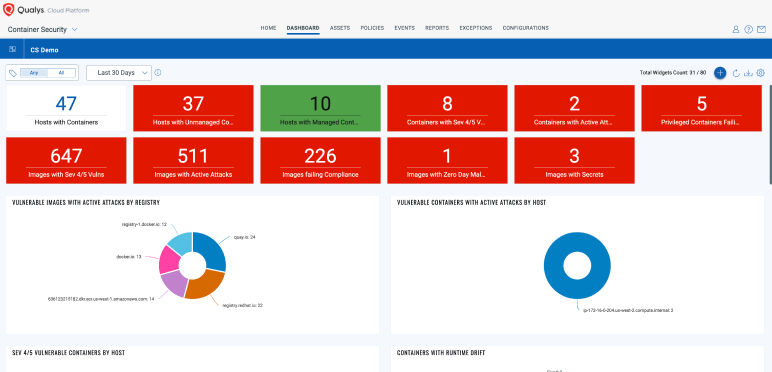
Eliminating zero day malware in images
Eliminating (even zero day) malware from images in registry.
DID YOU KNOW?
For the first time, the DBIR has included supply chain as a separate metric, at 15% of all attacks in 2023, a notable rise from last year when it stood at roughly 9%, for a 68% year-over-year growth
What does it contain?
- Setting up a connector for registry scanning
- Setting up a tracking dashboard
- Assessing the infected images
- Documenting the file path of malware detected
- Filing a JIRA ticket with SLA
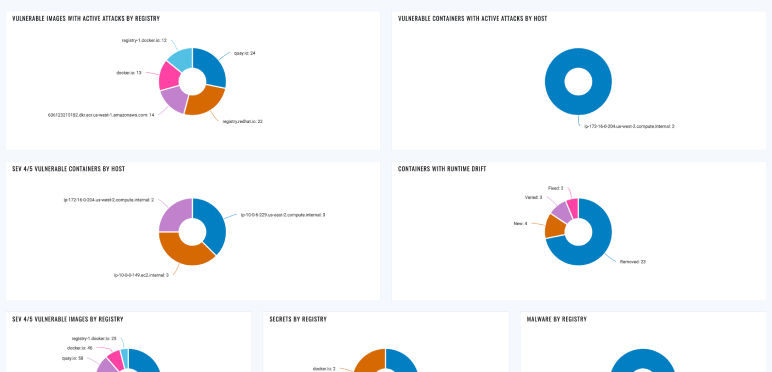
Eliminating secrets in Images
Eliminating secrets from images in registry.
DID YOU KNOW?
The Google Cloud's 2023 Threat Horizons Report found that 86% of breaches involve stolen credentials
What does it contain?
- Setting up a connector for registry scanning
- Setting up a tracking dashboard
- Assessing the infected images
- Documenting the file path and line number from where secrets can be harvested
- Filing a JIRA ticket with SLA
Explore PC Product Tours
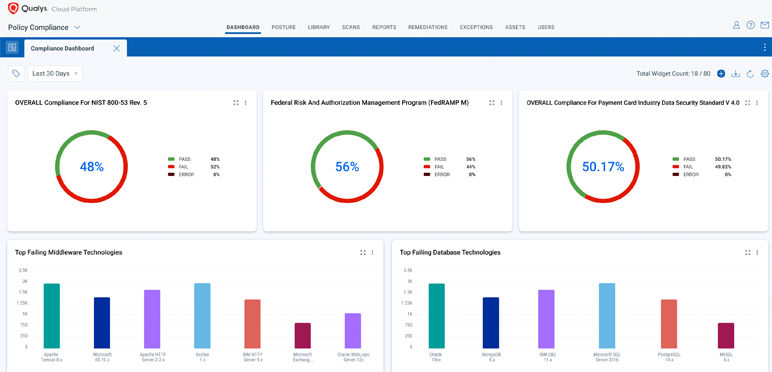
Identify and classify your assets
Auto-discover webservers, middleware and classify mission-critical assets for compliance.
DID YOU KNOW?
Policy compliance can automatically detect and assess databases and middleware instances across your hybrid environment to ensure you meet all NIST CSF 2.0 and CIS18 requirements.
What does it contain?
- Automatically detect and assess database
- Automatically detect and assess middleware instances across
- Hybrid environment support
- Ensure you meet all NIST CSF 2.0, CIS18, and other standard and framework requirements.
Automatically respond and recover from compliance failures
Automatically remediate misconfigurations with out-of-the-box scripts and customization to comply with NIST CSF 2.0 Respond and Recover Functions.
DID YOU KNOW?
There has been a 424% increase in breaches caused by misconfigurations and Gartner and IBM say 95% of breaches are caused by mistakes that lead to misconfigurations.
What does it contain?
- Pre-defined library of out of the box scripts
- Golden policies for auto remediation through CI/CD pipelines
- Remediate misconfigurations at scale
- Prevent exploits and improve overall compliance posture
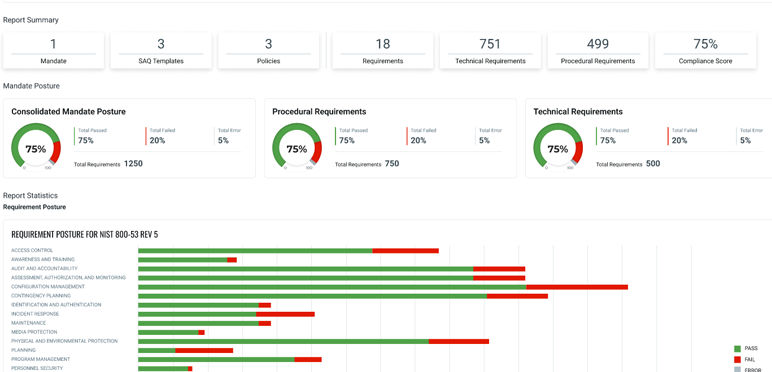
Communicate compliance for regulations, frameworks, standards and more
Demonstrate compliance during audits or regulatory inspections
DID YOU KNOW?
70% of firms need to comply with 5+ frameworks and regulatory standards.
What does it contain?
- Visibility into Asset based risks and applying appropriate controls
- Easily understand both technical and procedural requirements to comply
- Unified assessment and tracking of Technical and Procedural controls
- Gain visibility into controls and evidence for Audit
Explore CAR Product Tours
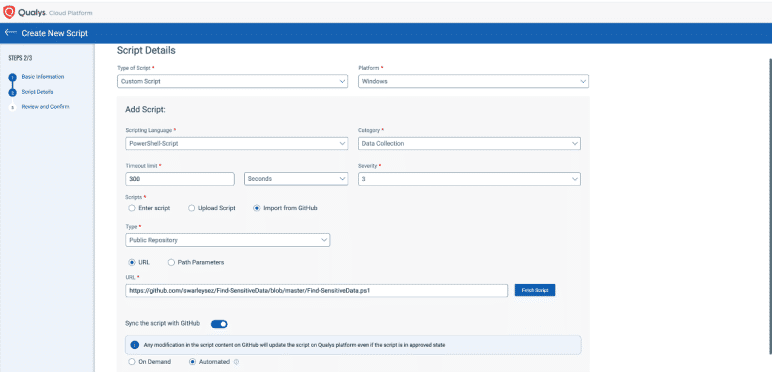
Create and execute scripts for custom detection and response measures
DID YOU KNOW?
Qualys CAR lets you create custom logic for unique security needs. With the right script, any use case can be solved.
What does it contain?
- Custom Script creation
- Support for multiple scripting languages
- Implementing Safeguards around Script Creation and Execution
- Script execution options
- Maintaining Activity logs
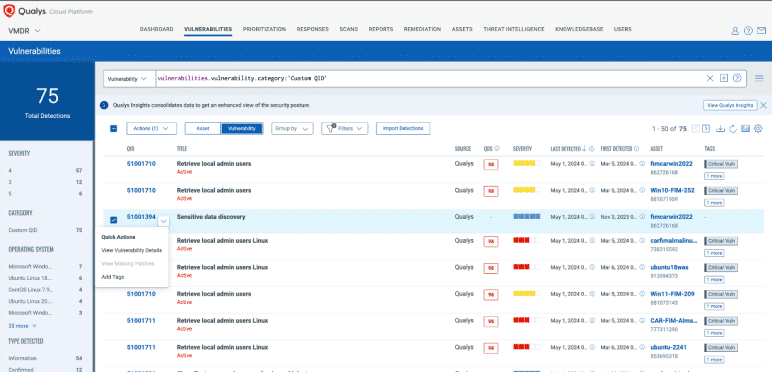
Integration with VMDR - Bring your own QID!
Enhance VMDR with vulnerabilities unique to your environment with Custom QIDs.
DID YOU KNOW?
Qualys CAR lets you create custom QID under VMDR.
What does it contain?
- Custom QID as a script type
- Vulnerability detection for Custom QID
- Viewing Vulnerability Results for Custom QID
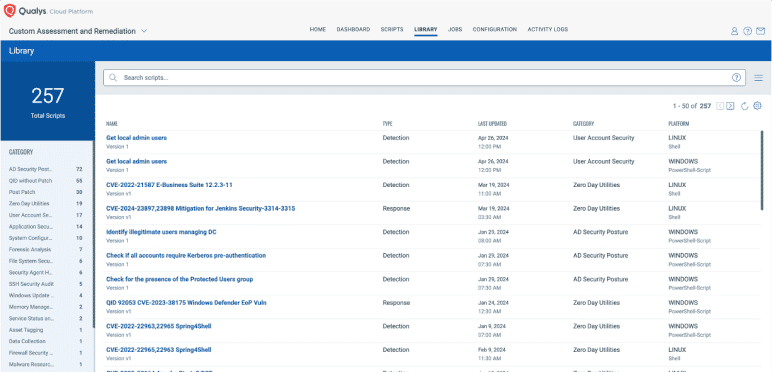
Leverage script library
Utilize our script repository to boost security and ensure compliance with industry standards.
DID YOU KNOW?
Qualys CAR features a centralized repository of pre-defined scripts by research analysts for various use cases.
What does it contain?
- Script Library overview
- Category based search for required scripts
- Importing scripts from CAR Script Library
Explore TotalCloud Product Tours
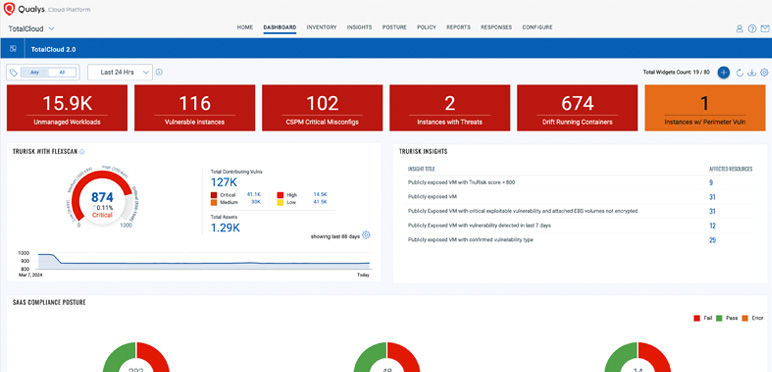
Prioritize Risk reduction for your cloud Infrastructure with TruRisk Insights
Drive data-driven decisions with actionable insights and customizable security dashboards.
DID YOU KNOW?
Cloud environments challenge IT security teams in prioritizing risk remediation. With evolving attack techniques, organizations need efficient tools and strategies to preemptively mitigate risks.
What does it contain?
- Inspect TotalCloud default dashboard to check TruRisk insights
- Walk thru TotalCloud TruRisk insights details
- Review each impacted inventory with TruRisk insights
- Remediation workflow to immediately remove the risk to cloud
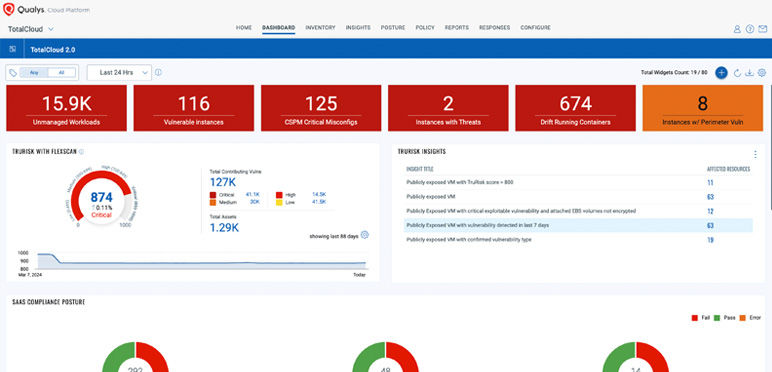
Discover risky assets with TotalCloud TruRisk Insights
Discover risky assets and factors with actionable insights and customizable dashboards.
DID YOU KNOW?
As attack techniques evolve, cloud environments face constant risk. Organizations need comprehensive solutions to learn trends and mitigate threats preemptively.
What does it contain?
- Inspect TotalCloud default dashboard to check TruRisk insights
- Walk thru TotalCloud TruRisk insights and contributing factors
- Review list of impacted assets
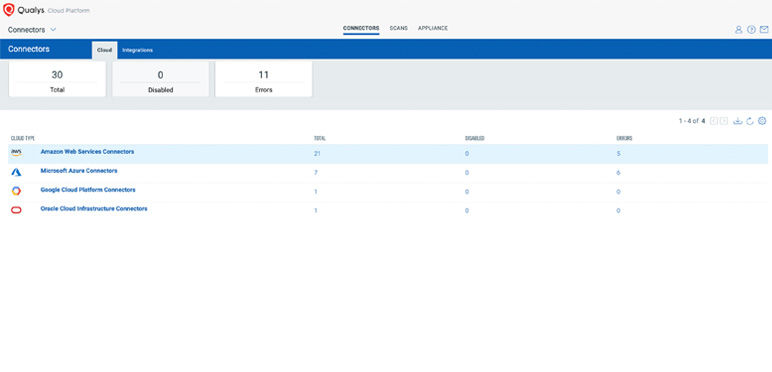
Organize and understand your cloud inventory and identify associated risks
Discover, identify, and remediate cloud risks in a single view.
DID YOU KNOW?
Growing organizations often manage multiple clouds. IT and security teams need a unified platform to monitor inventories, reduce misconfigurations, and mitigate attack risks.
What does it contain?
- Deploy TotalCloud connector
- Walk thru TotalCloud inventory and posture
- Organize cloud inventory with tags in TotalCloud
- Create Dashboard
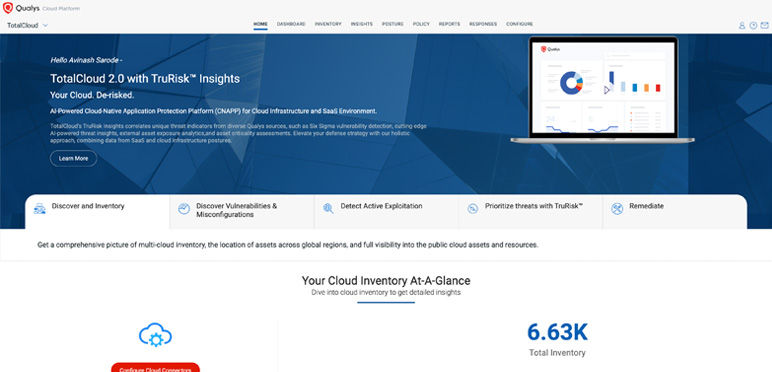
Improve Cloud Infrastructure CIS benchmark compliance
Improve CIS compliance by identifying and auto-remediating failed cloud controls.
DID YOU KNOW?
On average, 50% of CIS benchmark controls across major CSPs fail. These benchmarks are vital for improving cyber-defense and managing sensitive data under regulatory requirements.
What does it contain?
- Create Dashboard for CIS controls for cloud
- Review status and details of benchmark controls
- Collaborate teams to improve the benchmark compliance
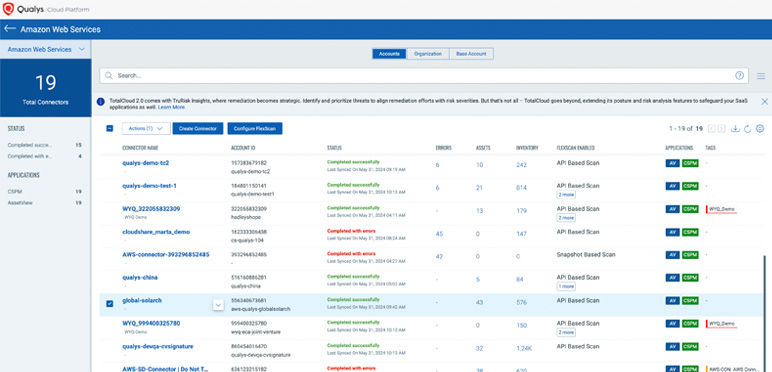
Discover and remediate workloads with critical exploitable vulnerabilities
Identifying workloads with vulnerabilities, assessing risk to critical workloads and prioritizing remediation.
DID YOU KNOW?
The 2024 Verizon Data Breach Investigation Report shows a 180% increase in attacks exploiting vulnerabilities as the initial entry point, accounting for 14% of all breaches.
What does it contain?
- Configure TotalCloud connectors to run FlexScan
- Create dashboard for critical workloads with exploitable vulnerabilities
- Create auto remediation for critical vulnerabilities
- Generate reports review and audit
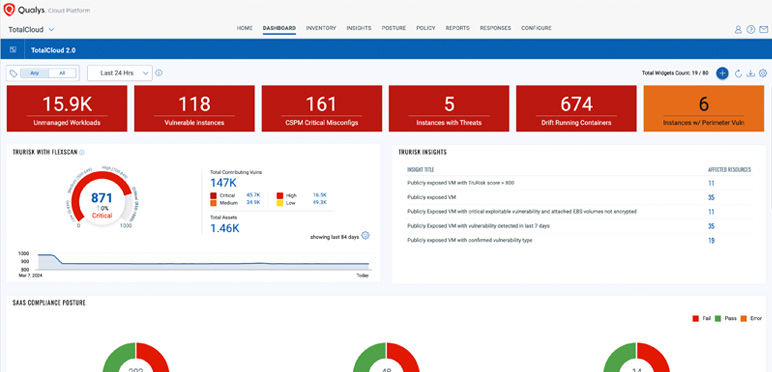
Real-time protection against Zero-day malware, ransomware and crypto-miners and their mutant with AI/ML platform
Detect malware, ransomware, crypto-miners, and mutations in real-time using AI/ML.
DID YOU KNOW?
Traditional IDS relies on known signatures, delaying detection of new malware. Modern malware evolves quickly, rendering traditional methods ineffective against zero-day exploits.
What does it contain?
- Create dashboard to check CDR findings for malware detection
- Identify cloud workloads for malware detection
- Collecting and Validating Qualys AI/ML analyzed malware information