Infrastructure as Code (IaC) Security
Your Cloud. De-risked.
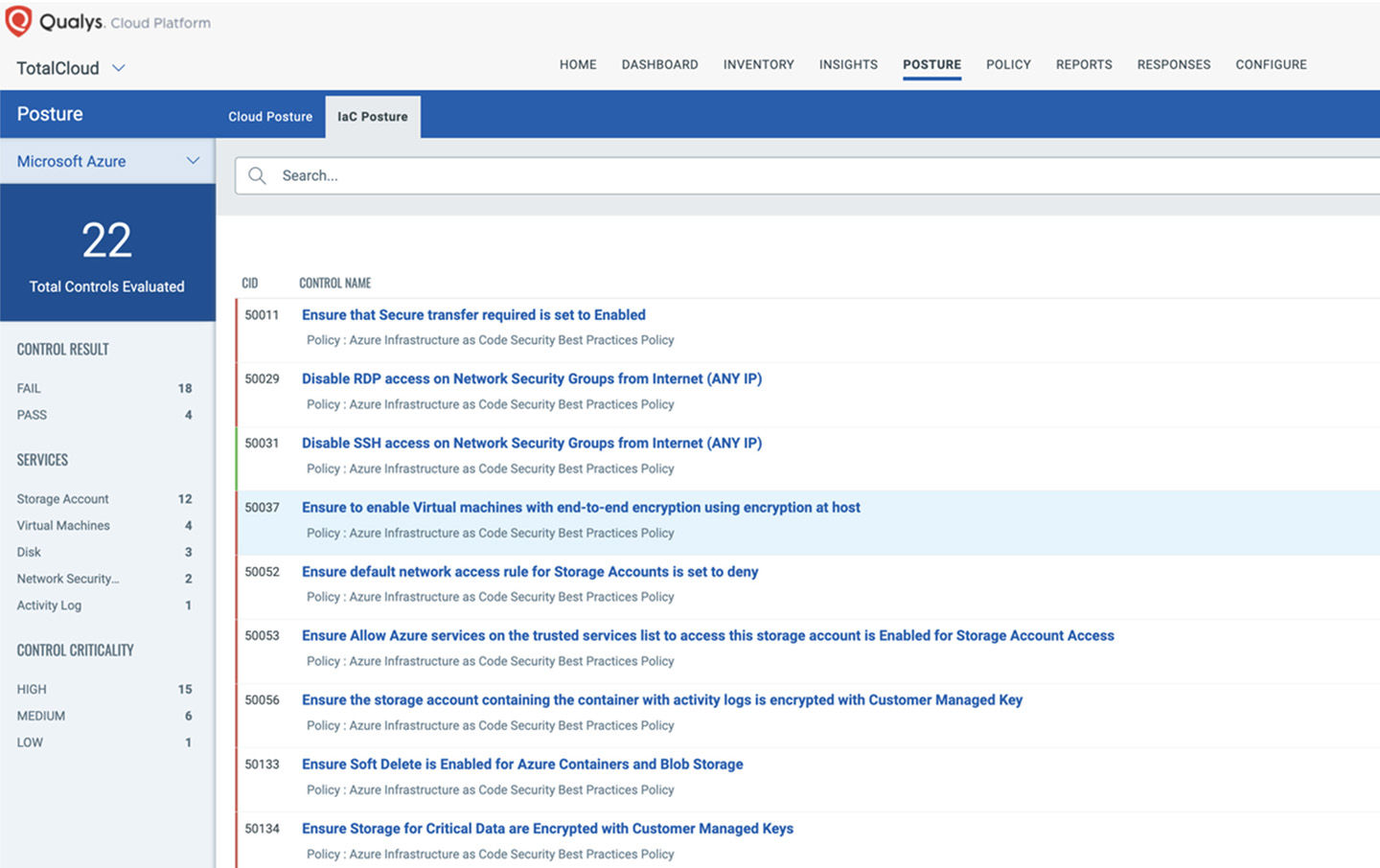
Our IaC tool helps you address potential security threats to your cloud infrastructure by detecting and remediating security problems within IaC templates.
De-risk your cloud with IaC – an integral part of Qualys TotalCloud™ – an AI-powered CNAPP solution
Prevent cloud misconfigurations
Scan your IaC templates for early visibility into misconfigurations across your cloud deployments. Integrate seamlessly with the CI/CD toolchain.
- Supports Terraform, AWS CloudFormation, and Azure ARM
- Provide real-time assessments of cloud misconfigurations to DevOps teams through integration with GitHub, Bitbucket, GitLab, and Azure Repo
- Integration with CI/CD such as Azure DevOps, Jenkins
- Integration with IDE such as Visual Studio Code

Drift detection
Ensure security policies established during the development and testing stages are consistently enforced during runtime operations via parity with runtime controls. Minimize risks due to misconfigurations or changes made after deployment.

Always be secure and audit-ready
Ensure cloud infrastructure compliance with mapping to over 40 global compliance mandates, including PCI DSS, HIPAA, and GDPR.
Minimize human error and increase efficiency with an extensive library of over 1,000 out-of-the-box security controls for major public cloud providers such as AWS, Azure, and Google Cloud Platform.

Stop misconfiguration at runtime
Visibility into misconfigurations and non-standard deployments at the pre-deployment stage.
Shift left through integration with Dev and DevOps tools
Integrates with the code editors, Git repository, and CI/CD tools to provide early visibility.
Out-of-box support for cloud IaC languages
Supports Terraform, AWS CloudFormation, and Azure ARM.

Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.