Network Security Solutions: Vulnerability Management | Continuous Monitoring
Cyber security threats can come from anywhere at any time, so network security needs to be continuous, scalable, extensible and comprehensive.
You must constantly monitor and discover your assets, be alerted about atypical network changes and quickly identify and remediate critical vulnerabilities and compliance problems. Otherwise, you won’t be able to respond to suspicious incidents and your network will be at an elevated risk of breaches.
Automate your network auditing and vulnerability management lifecycle with Qualys
Qualys gives you full visibility of IT assets across your network — on premises, in cloud instances and mobile endpoints — shows you how they might be vulnerable and lets you protect them.
Qualys Vulnerability Management (VM) continuously identifies exposures so you can defend your organization against attacks wherever and whenever they appear.
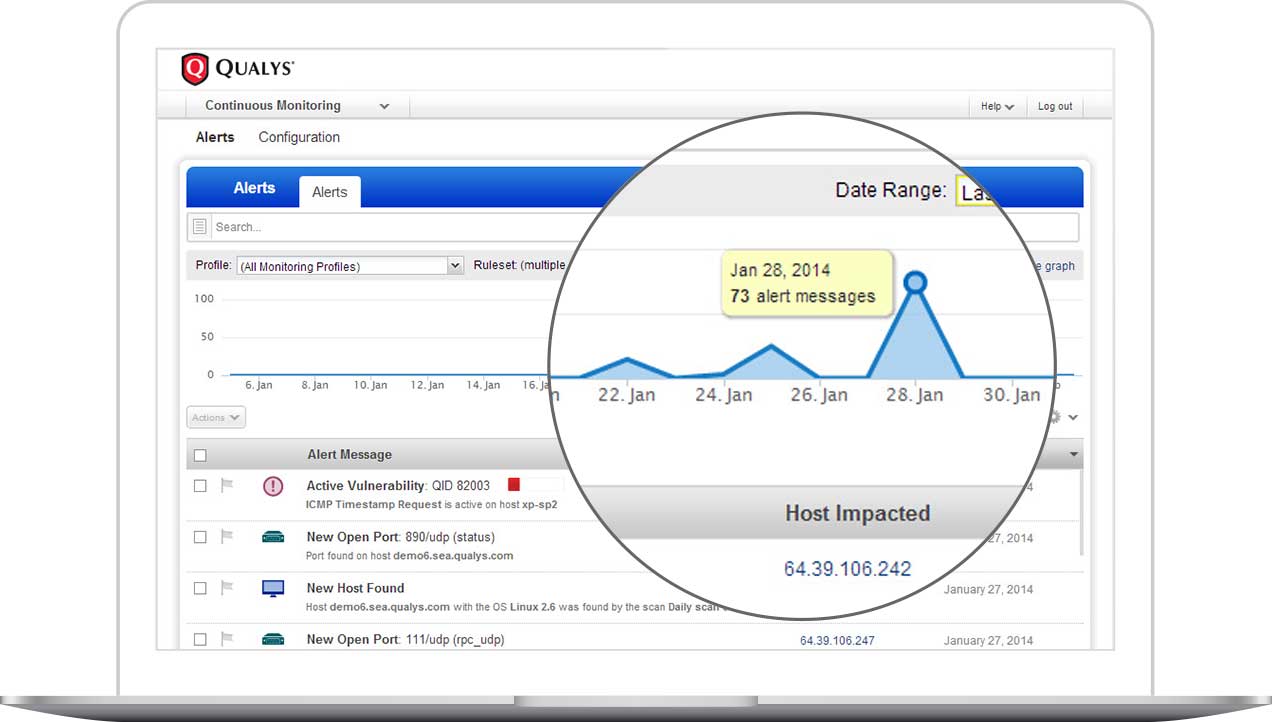
Qualys Continuous Monitoring (CM) alerts you in real time about network irregularities, such as new hosts/OSes, expiring certificates, unexpected open ports and unauthorized software.
As part of the integrated security and compliance Enterprise TruRisk Platform, these apps are hosted and maintained by Qualys, can be immediately deployed, operate continuously, scale globally and offer users centralized management.
VM Features
Discover and Assess
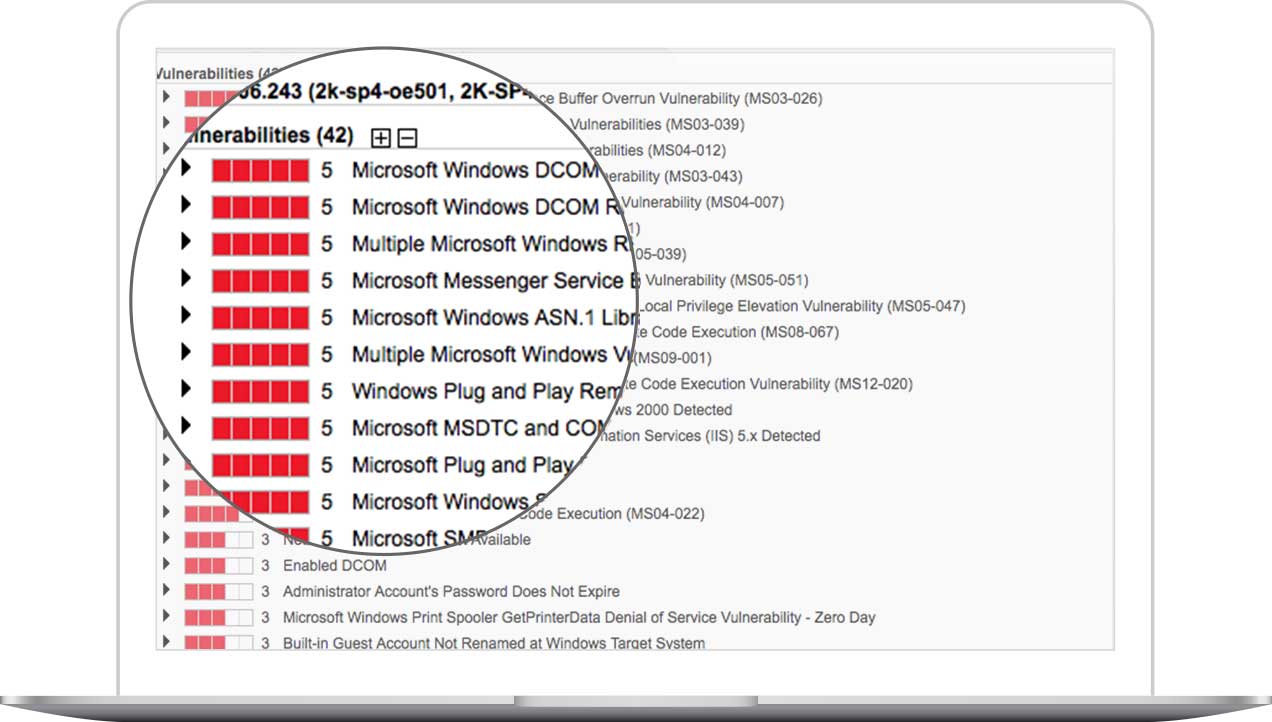
VM maps all assets on the network, detailing their OS, ports, services and certificates, and scans them for vulnerabilities with Six Sigma 99.99966 percent accuracy.
Remediate
VM assigns remediation tickets, manages exceptions, lists patches for each host and integrates with existing IT ticketing systems.
Inform
VM generates comprehensive reports customized for different recipients — like IT pros, business executives or auditors — and incorporates context and insight, including progress against goals. Via VM’s APIs, the reporting data can be integrated with other security and compliance systems.
CM Features
Integrated
CM works in tandem with VM so that, from a single console, you can discover hosts and digital certificates, organize assets by business or technology function and set up alerts.
Comprehensive
CM watches your global network from the cloud, like potential attackers do, and is thus able to oversee your on premises systems, mobile devices and public cloud instances.
Targeted
Alerts can be tailored for a wide variety of conditions impacting systems, certificates, ports, services and software. Each rule can be configured to detect common, general changes or tuned to very specific circumstances. You can assign different recipients for each alert, so that the appropriate person is notified.
Sign up today for a free trial. There's nothing to install!
Free Trial

