Infrastructure security solutions.
Guard your networks and datacenters.
![Visma]()
With the Enterprise TruRisk Platform, we’re succeeding in making the business aware of what they need to do to keep their systems safe—it’s a valuable layer of protection against potential threats.
Hans Petter Holen CISO
Protecting your company’s data center systems is a high-stakes challenge. Qualys can help.
You’ve got a lot to juggle. Defending against constantly changing threats, supporting new technologies, and ensuring IT compliance. Legacy security products are siloed, expensive, and ineffective. That’s where the Enterprise TruRisk Platform comes in.

Qualys has everything you need to secure your datacenters.
Inventory your entire global IT infrastructure
For strong security, you need a complete, continuously updated, and detailed IT asset inventory. Qualys automatically discovers, normalizes and catalogs all your data center components: servers, databases, networking wares, storage units and more. It captures detailed information, such as running services, installed software, traffic, hardware/software lifecycles, software licenses, vulnerabilities, and surfaces the information via custom dashboards, automated reports and search queries.
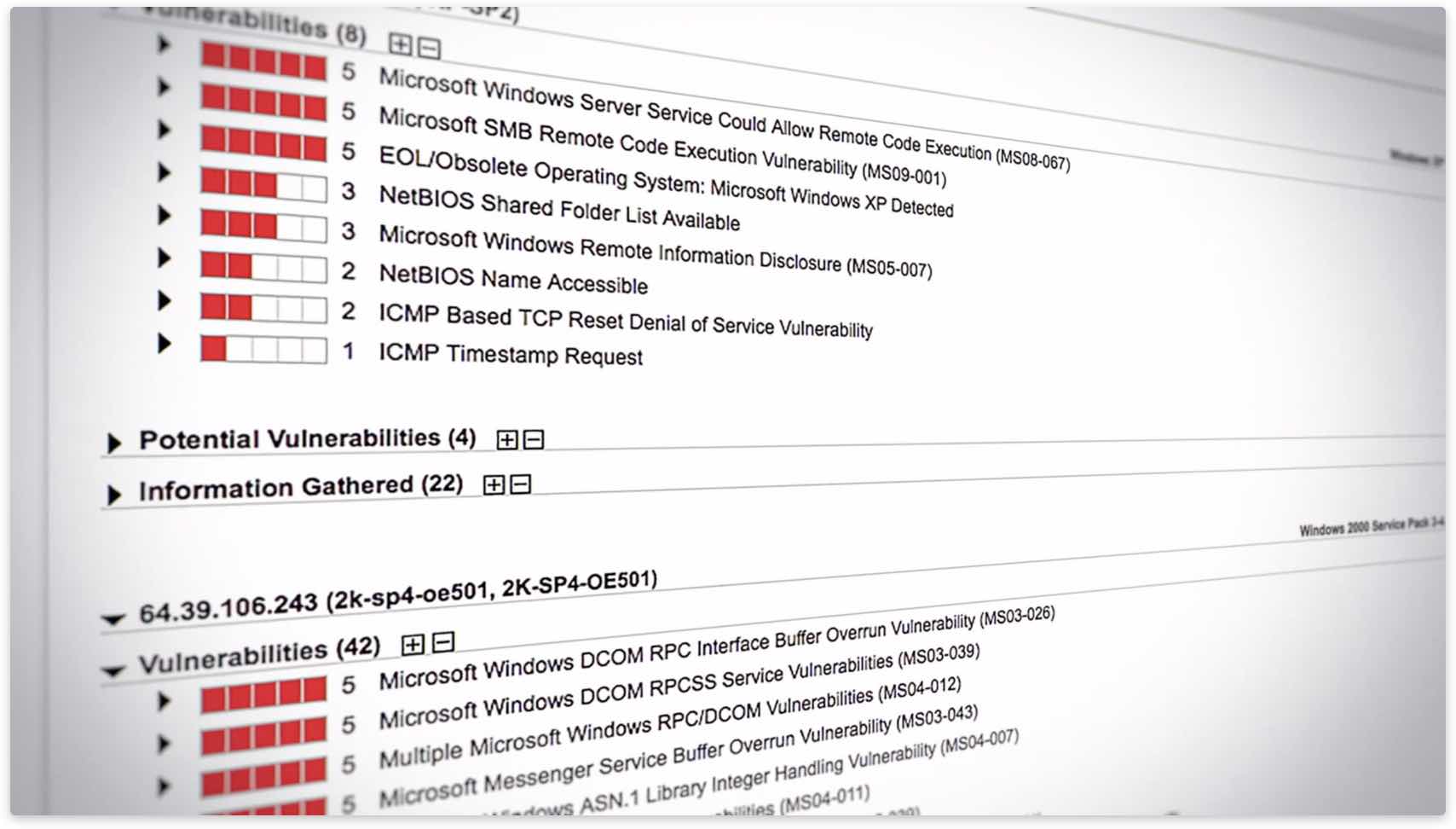
Find and address vulnerabilities
Most breaches exploit known bugs. Removing this low-hanging fruit keeps hackers out. With Six Sigma (99.99966%) scanning accuracy, Qualys maps your network’s data center systems and flags their vulnerabilities. You can easily assign remediation tickets, manage exceptions, list patches for each host, and generate reports for different recipients—like executives, IT managers or auditors. With Qualys, you can also address security-related configuration issues, a major source of recent breaches. Qualys automates configuration assessment of data center environments through out-of-the-box certified policies from the Center for Internet Security (CIS), and simplified workflows for scanning and reporting.
Monitor your network around the clock
Your data center’s security and compliance posture can change instantly. Dangerous vulnerabilities are disclosed. Existing ones become weaponized. New technology alters your environment. Qualys continually monitors your network and alerts you in real time about new threats and system changes, so you can respond and prevent breaches and policy violations.
Prioritize remediation
With thousands of vulnerabilities disclosed annually, you can’t patch all present in your data center. You must pinpoint critical ones requiring immediate attention. Qualys automates this intensive data analysis process. By continuously correlating real-time threat information against your vulnerabilities and IT asset inventory, Qualys gives you a full view of your threat landscape.
Validate file integrity
You must monitor files to enforce change controls, fulfill compliance requirements and detect compromises. Leveraging its Cloud Agents, Qualys’ file integrity validation solution monitors OSes in real time, and is easy and inexpensive to install, configure and manage. With a real-time detection engine, it centrally logs and manages events, and correlates and tracks change incidents.
Monitor systems
You must flag indicators of compromise pointing to malware attacks your antivirus products may miss. Using its Cloud Agents, Qualys gathers IoC data from your assets and stores, processes, indexes and analyzes it. Qualys’ EDR capabilities help you hunt threats, verify network alerts, detect suspicious activity and flag malware.
Inventory and monitor your public cloud workloads and infrastructure

See for yourself. Try Qualys for free.
Start your free trial today. No software to download or install. Email us or call us at 1 (800) 745-4355.

