Purpose-Built Solutions by Business Segment
- Small Business
- Mid-Sized Business
- Enterprise
- Federal
- Consultant/MSP
Consolidate solutions to a single platform
Measure, communicate, and eliminate cyber risk across the extended enterprise with a single platform and single agent to solve unique challenges for your business.
Threat Detection & Response
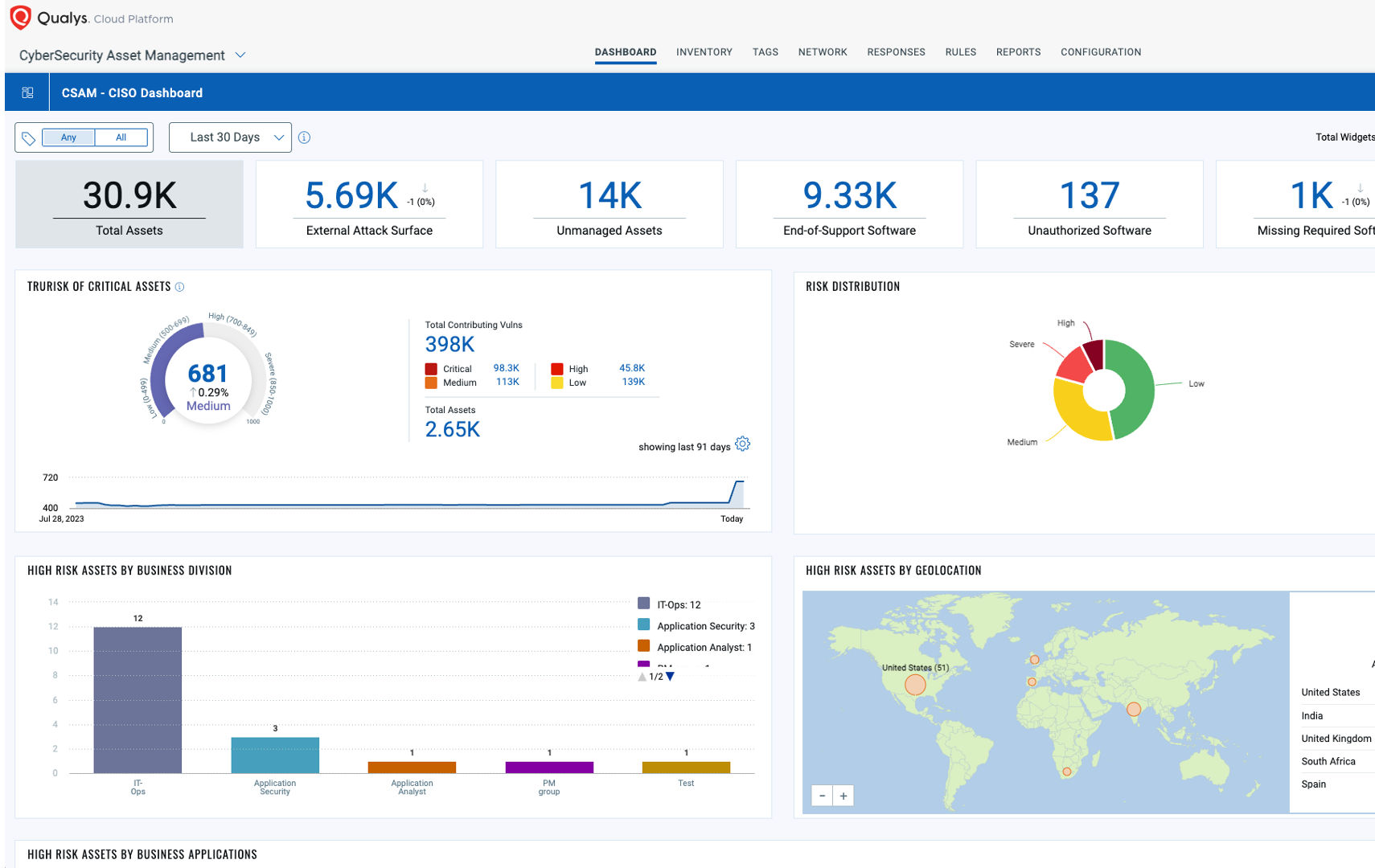
Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.