By submitting this form, you consent to Qualys' privacy policy
Email or call us at 1 (800) 745-4355
Forrester Wave CNAPP Leader, KuppingerCole 2025 CNAPP Leader and GigaOm Radar Leader and Outperformer. PeerSpot highest rated CNAPP vendor.
Services to unify cloud visibility and eliminate blind spots from compute to AI
Noise reduction with TruRisk™ for real, exploitable risk visibility versus alert fatigue
Assessment coverage for IP addresses; faster remediation through automation
Automatically discover cloud, container, and SaaS assets across AWS, Azure, GCP, and hybrid environments. Eliminate shadow IT and maintain continuous visibility across your entire attack surface.
Meet and prove compliance with frameworks across deployed cloud resources and IaC templates such as PCI DSS 4.0, HIPAA 2023, NIST 800-53/171, and GDPR through real-time monitoring, automated policy mapping, and audit-ready dashboards.
Learn MoreSecure The Full Container Lifecycle across Code, Build (CI/CD), Container Registries, and Production Kubernetes Clusters, Hosts and Serverless Workloads In Your Hybrid Cloud. Continuously map and assess image scans to running container posture, attack path, and drift context. Secure Your Kubernetes Control Plane with KSPM to prevent attackers and exploitation with runtime and AI-powered defense. Empower developers to fix left, using runtime-driven context to guide remediation at the source — before risk propagates across the pipeline
Learn MoreCut through the noise with risk scores based on exploitability, criticality, attack path analysis, and exposure. Focus remediation on exploitable vulnerabilities, not every CVE, and report meaningful risk reduction to the board and stakeholders.
Learn MoreVisualize and enforce least-privilege access across cloud identities, detect toxic permission chains, and automate revocation of risky roles to align with Zero Trust principles. Deepen CIEM + DSPM to correlate identity, permission, and sensitive-data exposure across hybrid infrastructure.
Learn MoreDetect zero-days, fileless malware, and anomalous process behavior with eBPF-based runtime monitoring and machine learning. Instantly contain threats via policy-based QFlow™ response playbooks.
Learn MoreDrag, drop, and deploy custom workflows that remediate vulnerabilities, fix misconfigurations, and trigger ITSM tickets in seconds, no scripts required.
Learn MoreContinuously evaluate 2,000 + resource types across SaaS apps for compliance with 40 + standards, including CIS and ISO 27001, and automate remediation via QFlow™.
Learn MoreBridge development and security with IaC scanning, API and web app assessment, and attack-path correlation from code to runtime. TotalCloud and TotalAppSec can work together to align Dev and Sec teams and catch vulnerabilities before release.
Learn MoreGain complete risk visibility into all AI being used in your environment with instant LLM Discovery and Scanning with Total AI across AWS Bedrock, GCP Vertex, Azure Open AI and more.
See your cloud risk the way attackers do.
TotalCloud's TruRisk™ engine correlates vulnerabilities, misconfigurations, entitlements, and threat intelligence into a single, business-contextual risk score. Attack path analysis and blast radius mapping show how a single issue could cascade through your environment, helping CloudSecOps and CISOs quantify and communicate risk with clarity.
Instead of hundreds of alerts, you see the few that matter most, and can remediate them instantly via QFlow™ workflows integrated with ServiceNow or Jira. It's how TotalCloud transforms raw data into actionable insight and risk reduction.

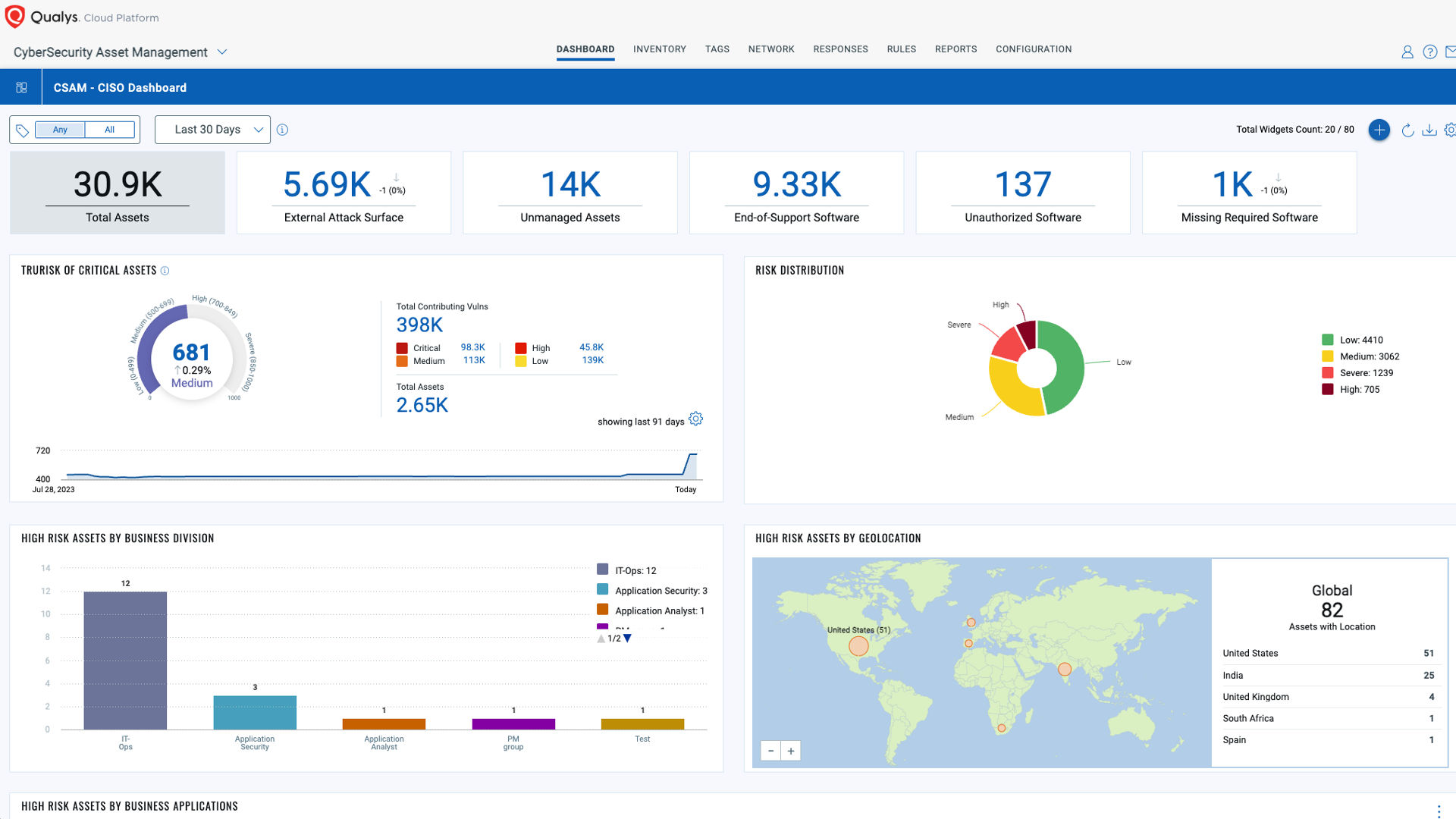
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.