Kubernetes and Container Security (KCS)
Your Containers. De-risked.
Discover, track, and continuously secure Kubernetes and containers from build to runtime.
Prioritize and Manage risk of the full Container Lifecycle from Image Build To Runtime
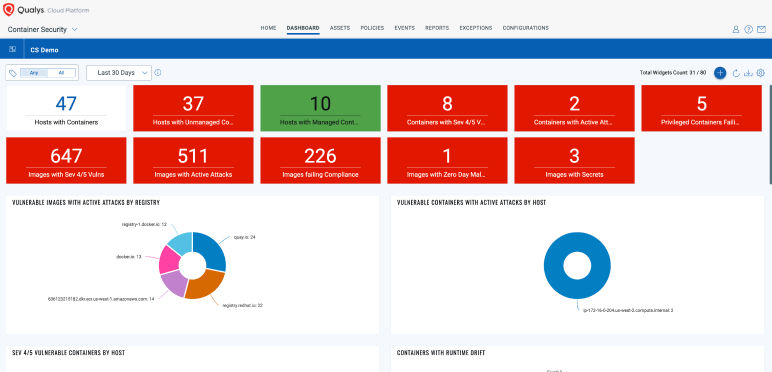
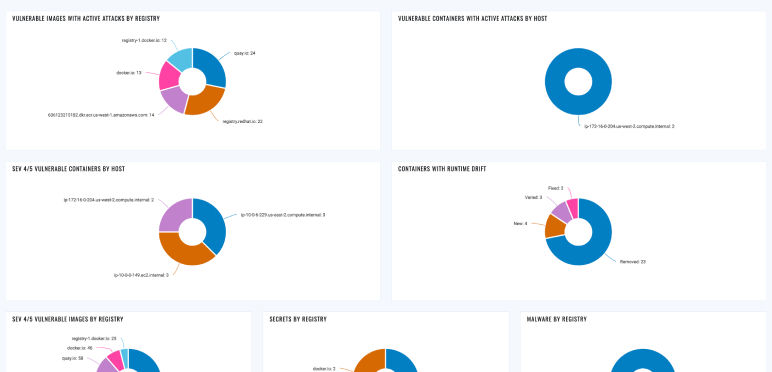
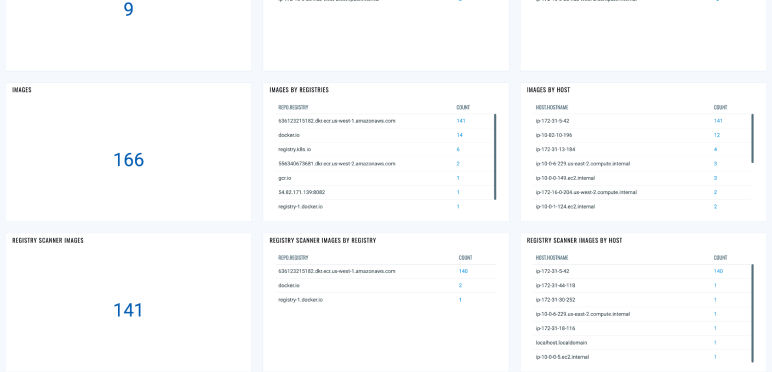
Continuous Vulnerability and Risk Assessment
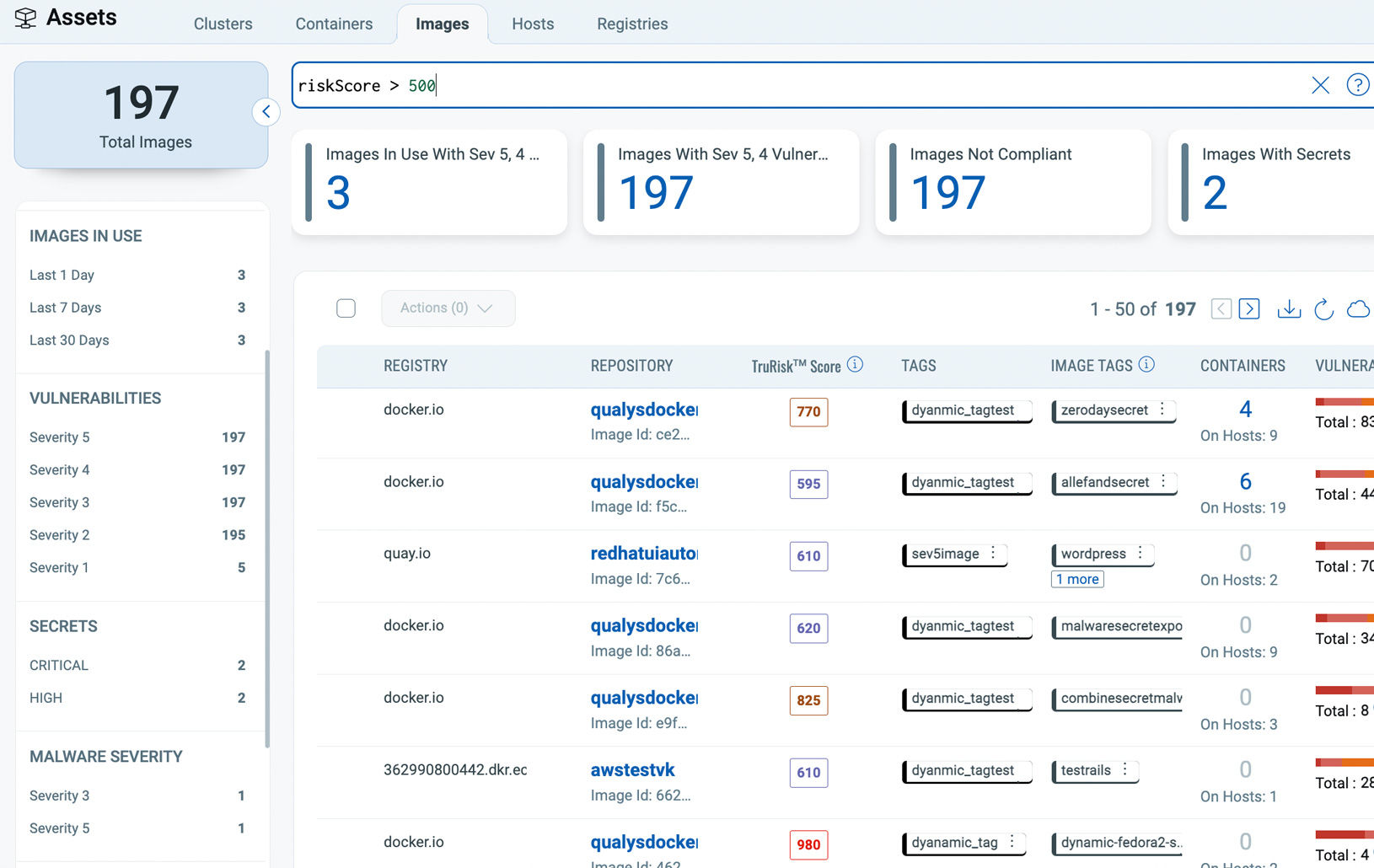
Continuously discover and assess images and containers across Kubernetes, Docker Hosts, Registries, and CI/CD Pipelines for vulnerabilities, malware, secrets, and SBOM. Prioritize real risk based on what's running.

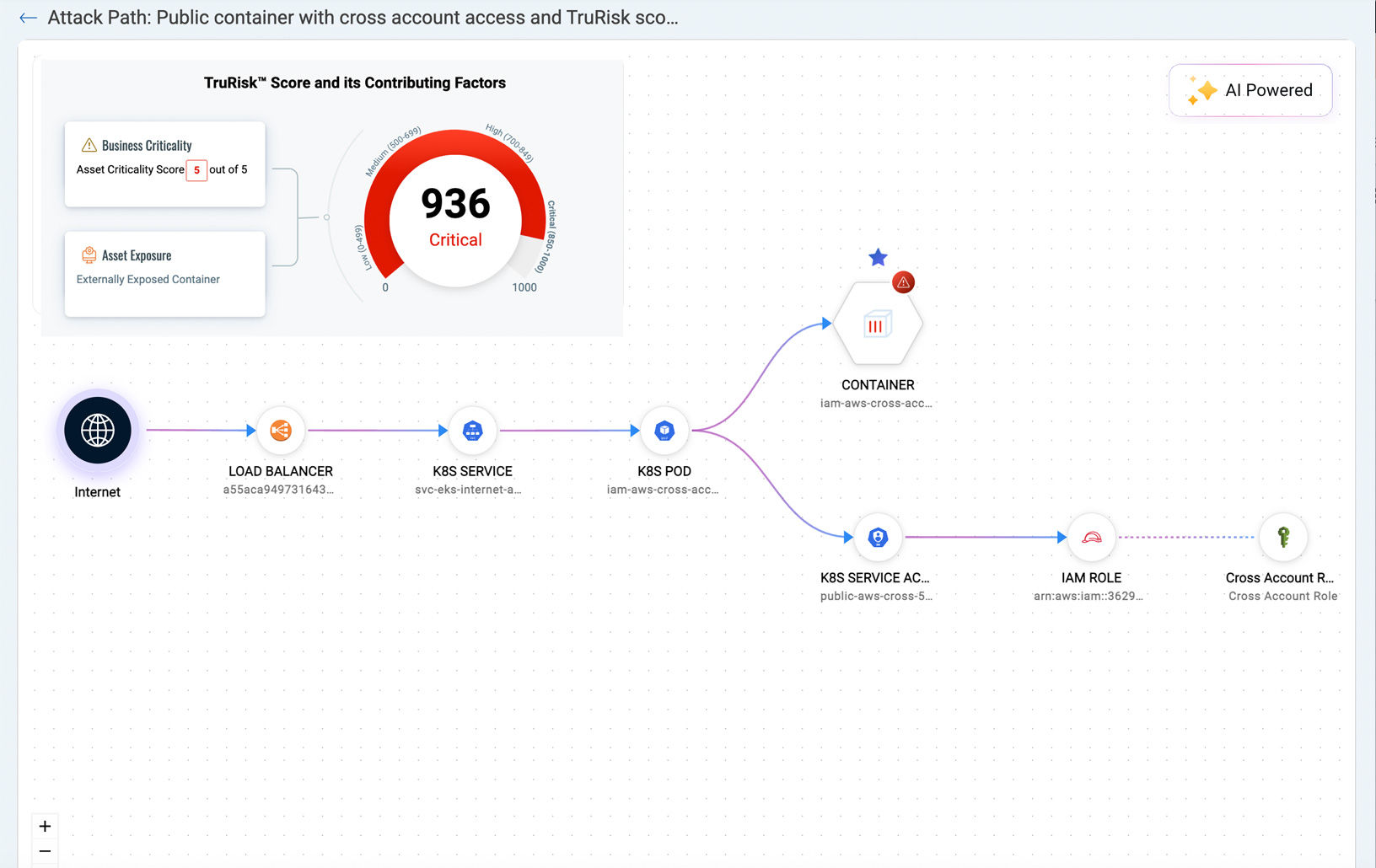
Proactive Risk Prioritization with Attack Path Analysis
Combine Attack Path Exposure with Business-Informed Scoring (TruRisk) to prioritize the most toxic combinations of risk. Ensure resiliency at scale through dynamic container tagging.

Image Layer Vulnerabilities and Remediation
Map vulnerabilities-whether in the OS, base image, or open-source packages to application layers owned by developers or the base layer owned by SecOps. Integrate with ServiceNow for automated ticketing and remediation tracking.

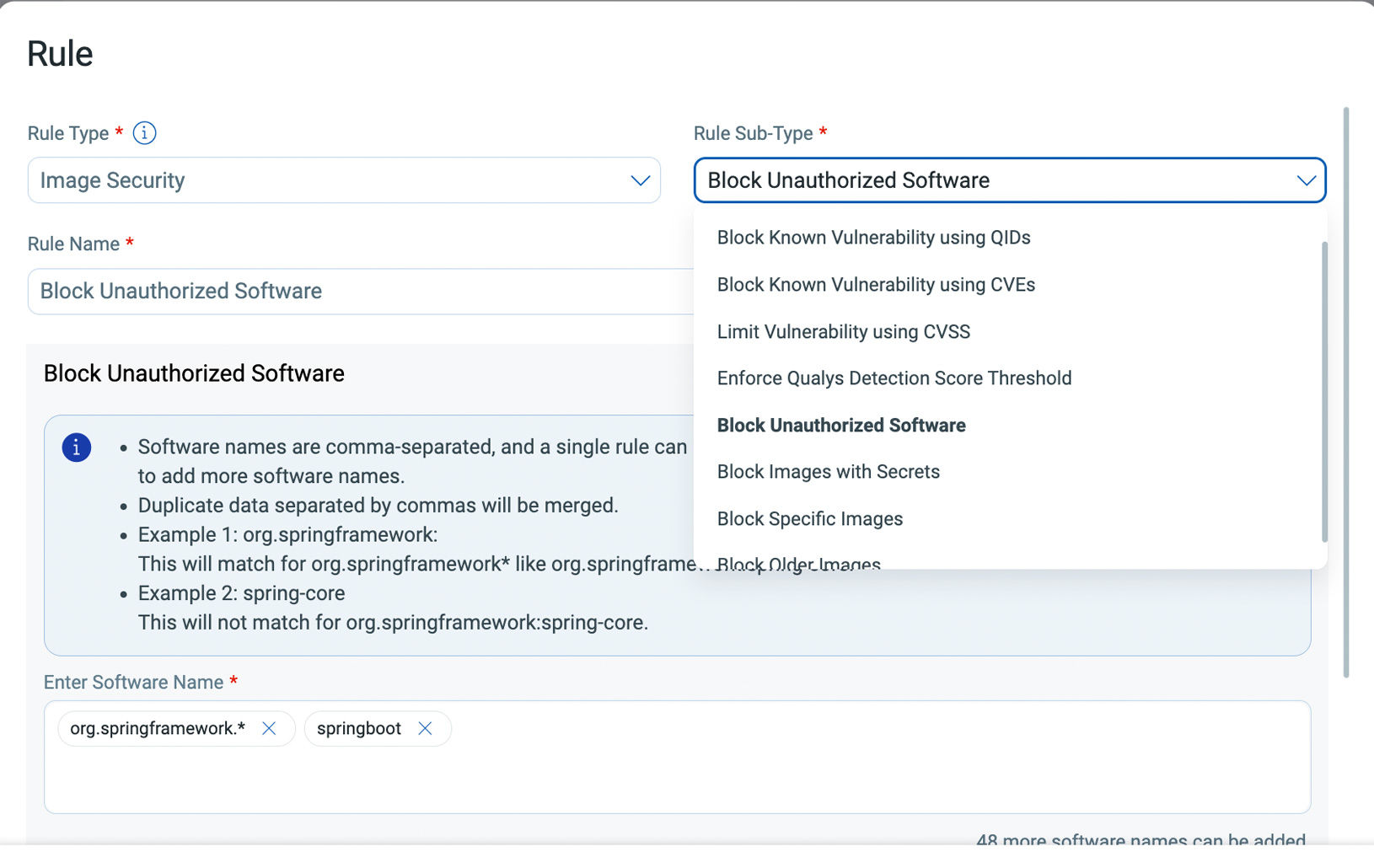
Admission Controls and Shift-Left Guardrails
Shift security left with Admission Controller and CI/CD policies that block unsafe configurations and images. Catch misconfigurations, insecure images, and policy drift before they reach production.

Continuous Kubernetes Security Posture Management (KSPM)
KSPM for EKS, AKS, GKE, and OpenShift helps uncover blind spots in API configurations, RBAC, and network segmentation. Continuously map findings including sensitive file access with Integrated FIM for PCI 4.0.

Build - Scan Your Development Builds
Bring rich vulnerability and risk prioritization context to your developers with QScanner - a self-serve CLI tool that can be integrated into any development build including GitHub Actions, Jenkins, and more. Block or audit insecure image builds with rich exception management.
Store - Secure Your Image Artifacts
Scan any Docker V2 Compliant registry including JFrog Artifactory, AWS ECR, Harbor.io, and more for vulnerabilities, software composition analysis, zero-day malware, and secrets. Apply Admission Controls to ensure only trusted registry images are deployed to production.
Deploy - Protect Your Production Environments
Continuously assess your containers in Kubernetes clusters and Docker hosts for key risks including vulnerabilities and misconfigurations. Prioritize with attack path context and business informed scoring. Detect malicious threats in real-time with eBPF Detections.
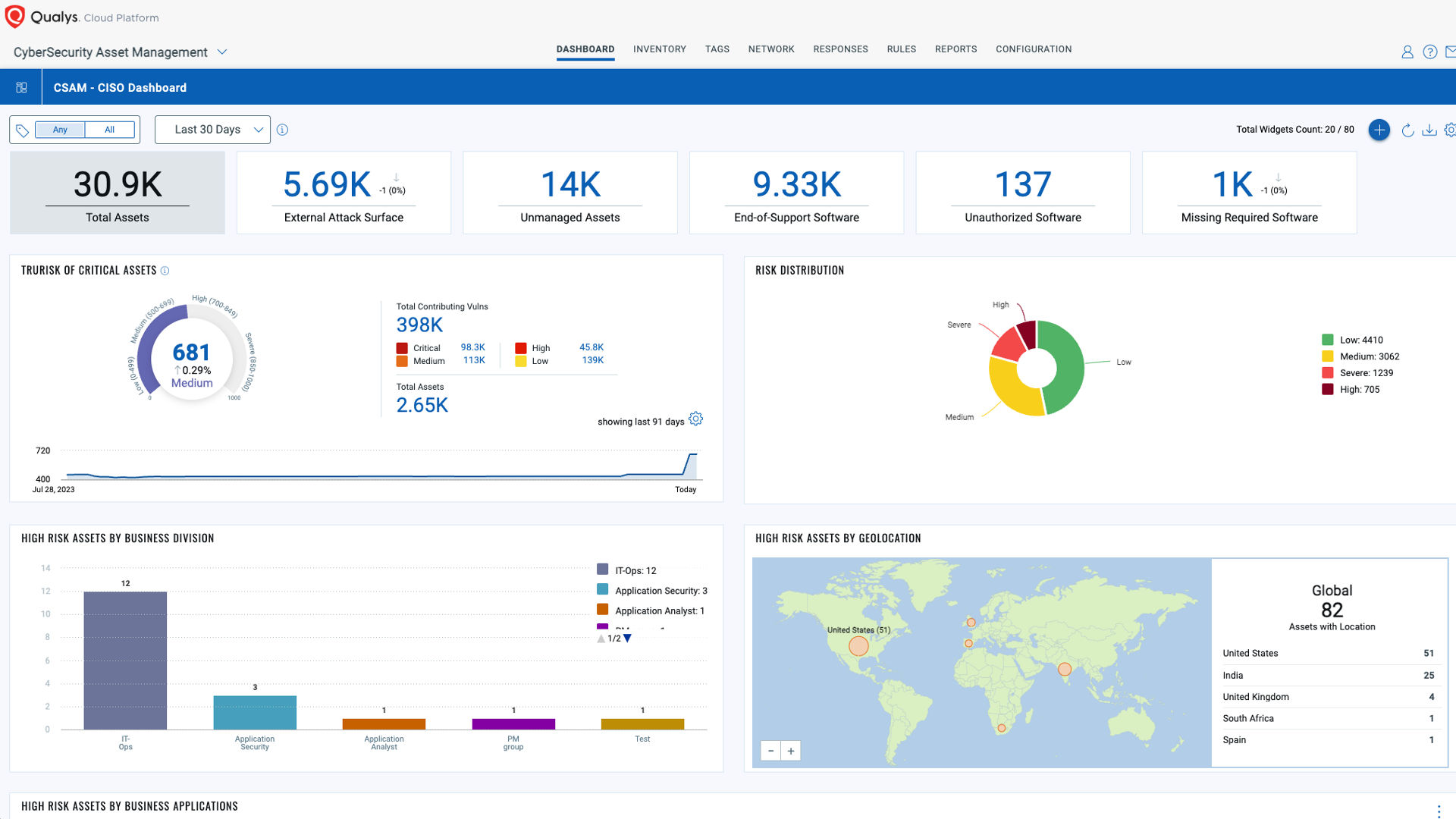
Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.