What is Attack Surface Management?
Exploring Step 0 in Your Cybersecurity Program
The modern attack surface is in constant evolution. Security teams must account for ever-changing attack vectors associated with IT, OT, and IoT assets, SaaS apps and cloud apps, databases and servers, digital certificates, software components, and unknown internet-facing assets. Organizations must have a strategic approach to discovery and risk assessment for all of the above. Attack Surface Management (ASM) is a proactive methodology that has become a cornerstone in modern cybersecurity. Let's delve into the world of Attack Surface Management, understand its significance, and explore how it contributes to safeguarding digital assets.
What is the Attack Surface?
In essence, the attack surface represents all the points where an attacker could attempt to enter or extract data from a system, network, or application. It's the sum total of vulnerabilities, both digital and physical, that could potentially be exploited by cyber adversaries. Even with strong Vulnerability Management and Remediation programs, organizations often struggle with continuous visibility of all assets that make up their attack surface.

What is Attack Surface Management?
Attack Surface Management is a comprehensive approach to identify, analyze, and mitigate potential security risks within an organization's attack surface. It goes beyond reactive security measures and adopts a proactive stance, continually monitoring and assessing the evolving threat landscape, with a focus on inventory and risk assessment of every cyber asset within the organization. The key element is “risk assessment.” It’s one thing to build a static inventory of assets, but true attack surface management includes the risk context that drives stronger vulnerability management and remediation. For this reason, attack surface management is often considered the foundational element (or “Step 0”) of enterprise cybersecurity programs.
The Key Components of Attack Surface Management:
Asset Discovery and Inventory
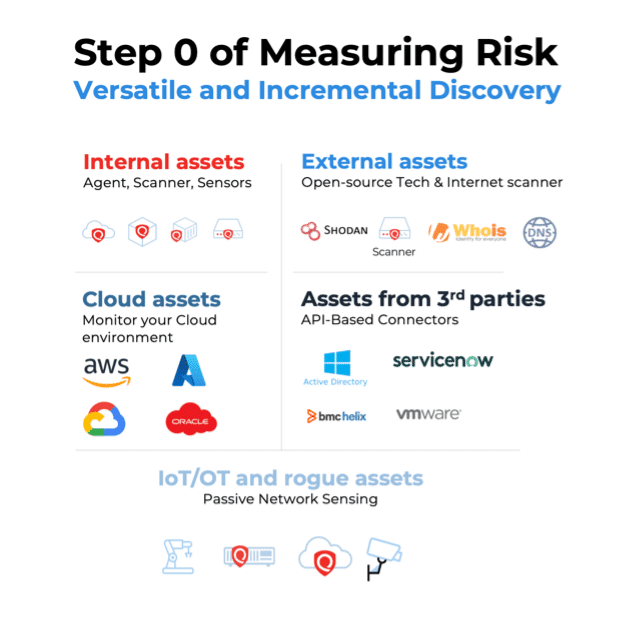
ASM begins with maintaining a continuous inventory of an organization's assets, including IT/OT/IoT devices, custom (first-party) apps, third-party apps, internet-facing assets, cloud assets, etc. The goal is to bring all of these cyber assets under management within the security program. This provides a foundation for understanding the scope and complexity of the attack surface.
For most organizations, these types of assets fall into the following categories: known, unknown, rogue, and vendor assets.
- Known assets have been discovered and inventoried and are under management within the security program. Organizations can monitor, scan for vulnerabilities, and assess these assets for compliance.
- Unknown assets are devices, systems, and applications that security teams have not accounted for. It might include Shadow IT, legacy systems from subsidiaries, unauthorized IoT devices, or unmanaged applications. These assets introduce unnecessary risk to the organization because they must first be discovered before the organization can apply security controls
- Rogue assets connect to the organization’s network without authorization. In Zero Trust Architecture, these assets are untrusted—and might be exploited to gain access to the network.
- Vendor assets or software must be managed within a security program, and organizations need to work with software vendors, cloud service providers, etc., to reduce associated risks. These assets can introduce vulnerabilities that rely on vendors to release patches and remediation steps.
Organizations must implement a variety of discovery methods to discover and inventory all categories of assets. Discovery methods include scanning, agent-based discovery, passive sensing, and API-based integrations with third-party data sources (such as Active Directory).
Risk Assessment and Mitigation
A complete inventory of assets is only the start. The list, on its own, is of no use to the cyber security program. Attack Surface Management requires an assessment of the risks associated with cyber assets. Traditional risk assessment focuses almost exclusively on vulnerabilities. Still, ideally, the ASM program will account for other multiplying risk factors, such as EoL/EoS software, risky open ports, unauthorized software, and missing security controls (such as an EDR agent).
Streamlining risk assessment and remediation closes the loop on your ASM program, driving the results that de-risk the business. Your ASM tool should include a streamlined workflow with vulnerability management, Web Application Scanning, patch management, CMDB, SIEM tools, and more. To truly maximize the security and value of your ASM program, inventory risk assessment must be actionable across all other areas of the cyber security stack.
Watch On DemandContinuous Monitoring
The modern technology environment is both complex and dynamic. Devices and cyber assets are constantly connecting and disconnecting from the network. Security teams are chasing the visibility of assets associated with subsidiaries and hybrid work. Teams all over the organization introduce BYOD, open-source software, and vendor-owned assets daily. Rather than a one-time assessment, ASM embraces continuous monitoring to defend an ever-changing attack surface. This real-time approach allows organizations to detect and respond to potential threats promptly.
“Each asset discovery method can detect different types of devices, add business context to an asset record, and shine a light on an area where the organization was previously blind.”
There are a number of ways to promote continuous (or even real-time) visibility. Your ASM program should include versatile discovery methods. Relying solely on API-based integrations places too much trust in third-party sources and relies on snapshots captured by other sources. IP scans, External Attack Surface Management, passive sensing, and third-party connectors should all be part of your ASM program. Each asset discovery method can detect different types of devices, add business context to an asset record, and shine a light on an area where the organization was previously blind. Passive sensing, for example, can detect rogue/untrusted devices that connect to the network. In real time, it can detect IoT devices missed by scans and third-party connectors.
Without continuous visibility, these assets might contain vulnerabilities, misconfigurations, or other risks that expose the organization to attackers.
Common Challenges of Attack Surface Management
According to Qualys research, only 9% of organizations believe they actively monitor 100% of their attack surface. There are a variety of reasons why most organizations lack coverage. Here are the most common:
- Rapid Digital Transformation: The digital transformation wave has led to an exponential increase in the number and diversity of digital assets within organizations. Cloud services, IoT devices, and interconnected systems contribute to a sprawling attack surface, making it challenging to maintain an accurate inventory and assess vulnerabilities comprehensively.
- Shadow IT and Unmonitored Assets: The rise of shadow IT, where employees independently adopt and use unauthorized applications or services, poses a significant challenge in attack surface management. Unmonitored and unaccounted-for assets can become potential entry points for cyber threats, bypassing traditional security measures.
- Limited Discovery Methods: Many organizations still rely on a single method for asset inventory. ASM solutions might promise to build a comprehensive inventory out of API-based integrations, but they lack structured data and risk assessment. Even worse, they are often blind to unknown external assets or untrusted IoT assets that connect to the network.
- Lack of Risk Assessment: It’s one thing to know your assets; it’s another to understand the associated risks. A sound Attack Surface Management program includes vulnerabilities (and the risk according to business context), misconfigurations, EoL/EoS software, and operating systems, as well as missing security controls. Many organizations have invested in asset discovery tools that do not provide this data.
- Third-Party Risks: With organizations relying on external vendors and partners for various services, third-party risks become a significant challenge in attack surface management. Assessing and managing the security posture of external entities adds complexity to an already intricate landscape.
- Emerging Threat Vectors: As threat actors become more sophisticated, new attack vectors continually emerge. Attack Surface Management needs to adapt to these evolving threats and incorporate mechanisms to identify and mitigate risks associated with the latest attack techniques.
So, how are organizations solving these challenges to defend the attack surface? They need a solution built to address the risks
Try it nowRequirements for Your Attack Surface Management Solution
Defending your attack surface requires a solution that addresses the challenges above. It must eliminate blind spots that attackers can exploit, illuminate the cyber risk associated with all assets, and integrate with the security and IT tech stack that eliminates business risk. Organizations should choose a solution that offers all of the following capabilities:
Comprehensive Asset Discovery: A powerful ASM solution should find EVERYTHING. It must scan and identify all devices, applications, and services across your entire infrastructure, ensuring that no element of your attack surface remains hidden. If the solution relies on a single discovery method, consider it a red flag.
Vulnerability Assessment and Risk Prioritization: Ultimately, the list of assets on its own doesn’t secure anything. Security teams need to conduct vulnerability and risk assessments natively, using asset data and business context along with risk factors to prioritize business risk. However your organization discovers cyber assets and associated risks, the data must integrate with VM scanning, compliance dashboards/reporting, and remediation tools. This leads to our next requirement.
Learn moreIntegrations with IT and Security Tools: Cyber risk is business risk, which means the business must be aligned on asset visibility and cyber risk context. Your ASM tool should integrate with SIEM (Security Information and Event Management) solutions, threat intelligence feeds, CMDB tools, and other systems that contribute to remediation.
User-Friendly Interface: When a zero-day vulnerability is discovered, security teams need the ability to query for the impacted components and identify all associated assets. The faster a security team can quantify and communicate the risk across the organization, the faster the teams can align on the remediation steps. An intuitive and user-friendly interface is essential for effectively using the ASM solution. Security teams need to navigate through vast amounts of data effortlessly, make informed decisions, and act promptly to secure their attack surface.
Automated Remediation and Response: To minimize the time between identifying a vulnerability and implementing a fix, the ASM solution should support automated remediation and response. This not only enhances efficiency but also reduces the window of opportunity for potential attackers.
Scalability:As your organization grows, so does your attack surface. The chosen ASM solution should be scalable to accommodate the increasing complexity and volume of assets, ensuring it remains effective as your digital footprint expands. The versatility of discovery methods and ease of deployment are key factors in scalability.
Compliance and Reporting: Meeting regulatory requirements is non-negotiable in today's cybersecurity landscape. The ASM solution should offer robust reporting capabilities, making it easier for organizations to demonstrate compliance and track improvements over time.
In today’s rapidly evolving digital landscape, attackers are constantly looking for weaknesses and blind spots in the attack surface. If your cyber security program is missing complete visibility and cyber risk context, start by investing in your Attack Surface Management program to build a strong foundation for de-risking the business.