Free Report
How do you continuously discover your unknown, internet-facing assets and assess your risk posture?
Get the Qualys External Attack Surface Management Report - FREE!
With increased adoption of cloud, Internet of Things (IoT), and a continually growing remote workforce, it's harder than ever for security teams to correlate their externally visible and internally managed assets and govern compromises that occur because of undiscovered, unmanaged, or poorly managed IT assets.
From on-premises devices and applications across every endpoint, cloud, and container — cybercriminals are working around the clock to breach your ever-expanding attack surface.
Get this FREE report now and tap into effective strategies that will help your organization:
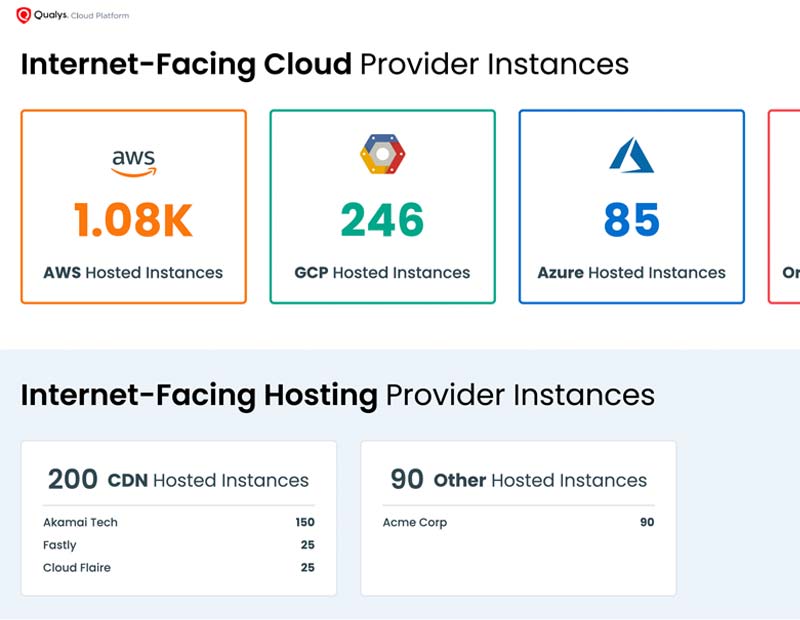
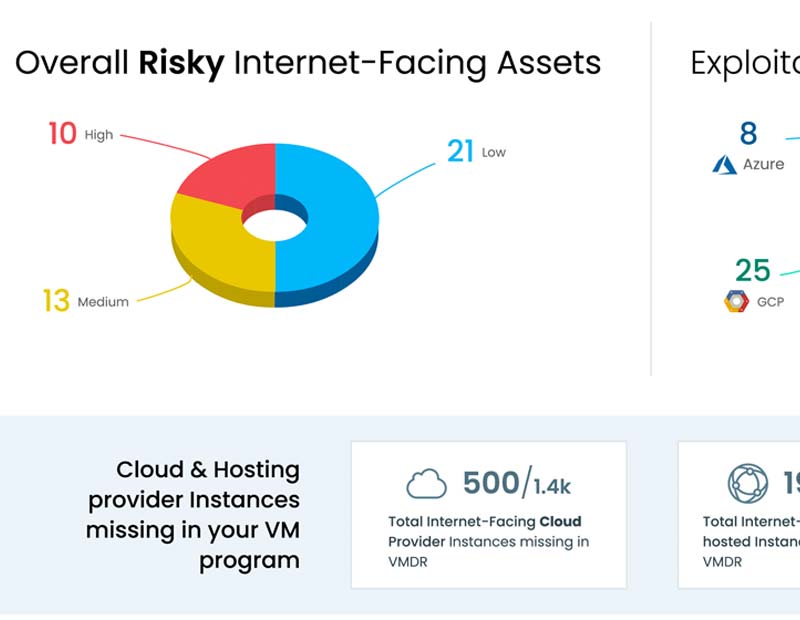
- Understand your risk across every internet-facing asset
- See your entire attack surface from every angle
- Prioritize risks through a single pane of glass
- Learn about Qualys External Attack Surface Discovery (EASM)
- Just complete this brief form to receive your FREE report now!
Download report
By submitting this form, you consent to Qualys' privacy policy.