What Is Vulnerability Management?
Finding focus in increasingly complex environments
While vulnerability management as a security solution has been around for some time, that doesn’t mean that organizations can afford not to keep on top of this critical, proactive risk management practice. There is a reason it is often seen as a cornerstone in any cybersecurity program. Today, with attack surfaces growing in size and complexity, too many “critical” vulnerabilities, increasing regulatory pressures, and faster weaponization by AI-enabled attackers are creating significant challenges for even the most advanced IT and security teams to address. As a result, having a robust vulnerability management program that can pinpoint the biggest business risks before they become true threats has become more important than ever before.
What is Vulnerability Management (VM)?
Vulnerability management is the process of continuously finding, assessing, and prioritizing vulnerabilities and misconfigurations, be they in cloud or on-premises, SaaS, or web applications, to fix those security weaknesses that present a risk to the business. This essential cybersecurity discipline involves a continuous process of scanning for vulnerabilities, analyzing their potential impact, prioritizing them based on risk, and implementing strategies to mitigate or resolve these issues. By continuously managing and fixing vulnerabilities, organizations can not only ensure compliance with industry regulations but also enhance their resilience against an increasingly hostile cyber environment.
Defining the Terms: Vulnerability, Misconfiguration, Threat, and Risk
Vulnerability: a vulnerability is a flaw or weakness in a software or system that could be exploited to violate the system’s security. A vulnerability is a potential risk, until there is exploit code written against it and it’s been exploited by attackers. That’s why VM is seen as a proactive, not a reactive cybersecurity discipline – it’s about preventing the potential harm that a vulnerability represents by fixing it before an attacker can exploit it.
Misconfiguration: A misconfiguration is an error in the setup of cloud services that leaves it vulnerable to malicious activity or causes it to operate incorrectly. Again, a misconfiguration is a benign error that represents unrealized risk until it’s found and exploited by attackers.
Threat: A threat then can exploit the vulnerability or misconfiguration to cause harm or unauthorized access to computer software, systems, and data.
Risk: Vulnerabilities, misconfigurations, and threats all create risk. Risk refers to the potential for loss or damage when a threat exploits any of the weaknesses listed above. The likelihood of the event and its potential impact are considered when measuring risk.
Business Benefits of VM
Vulnerability management offers many benefits to organizations and the security and IT teams that undertake the practice. A few such benefits:
- Exploit Prevention: Finding and fixing the vulnerabilities that offer the biggest risk to the business offers monetary rewards in its proactive prevention of breaches and data loss that could otherwise cost the business in customer trust, regulatory fines, and potential lawsuits.
- Enhanced Security & IT Operations: When a vulnerability management program is truly efficient in offering time savings by accurately identifying the highest-risk vulnerabilities that should be fixed first, saving IT and security teams cycles that would be spent chasing down lower-impact, low-risk vulnerabilities. VM can also help build the relationship between security and IT departments when they are both effectively using the same language of risk to protect the business.
- Improved Regulatory Compliance: Many industries are subject to strict regulatory requirements that mandate that vulnerabilities be addressed in a systematic fashion. Having an effective vulnerability program ensures compliance with such regulations, like the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and Payment Card Industry Data Security Standard (PCI DSS).
How Are Vulnerabilities Scored?
CVSS: The Common Vulnerability Scoring System (CVSS) was introduced in the early 2000s to address the need for a common method to rate the severity of vulnerabilities. It provides an open framework for communicating the characteristics and impacts of vulnerabilities.
CVSS scores are categorized into four categories: low, medium, high, and critical.
| CVSS Score | CVSS Severity |
|---|---|
| 0.1 – 3.9 | Low |
| 4.0 – 6.9 | Medium |
| 7.0 – 8.9 | High |
| 9.0 – 10.0 | Critical |
The original intent of CVSS was to identify the technical severity of vulnerabilities, not the level of risk that each vulnerability posed to an organization. So, while it makes sense to have CVSS as a contributing factor for vulnerability prioritization, it would be unwise to guide targeted and informed vulnerability management programs based on it.
EPSS: With the Exploit Prediction Scoring System (EPSS), defenders now have one more data insight for vulnerability prioritization. This scoring system estimated the likeliness of a vulnerability being exploited, with a probability score between 0 and 1 (0-100%). The higher the score, the greater the likelihood of exploitation of the vulnerability within the next 30 days.
Organizations considering the implementation of risk-based vulnerability management should incorporate EPSS as one of the criteria for prioritization. However, it would be imprudent to rely solely on EPSS for prioritization as it may overlook high-risk vulnerabilities or those being exploited in the wild.
TruRisk: Integrating risk-based vulnerability management, Qualys TruRisk offers organizations a sophisticated method to prioritize threats, which considers the severity of vulnerabilities as influenced by a variety of factors, including the assets’ business and operational criticality, its exposure level to potential attacks, and its importance to business-critical applications.
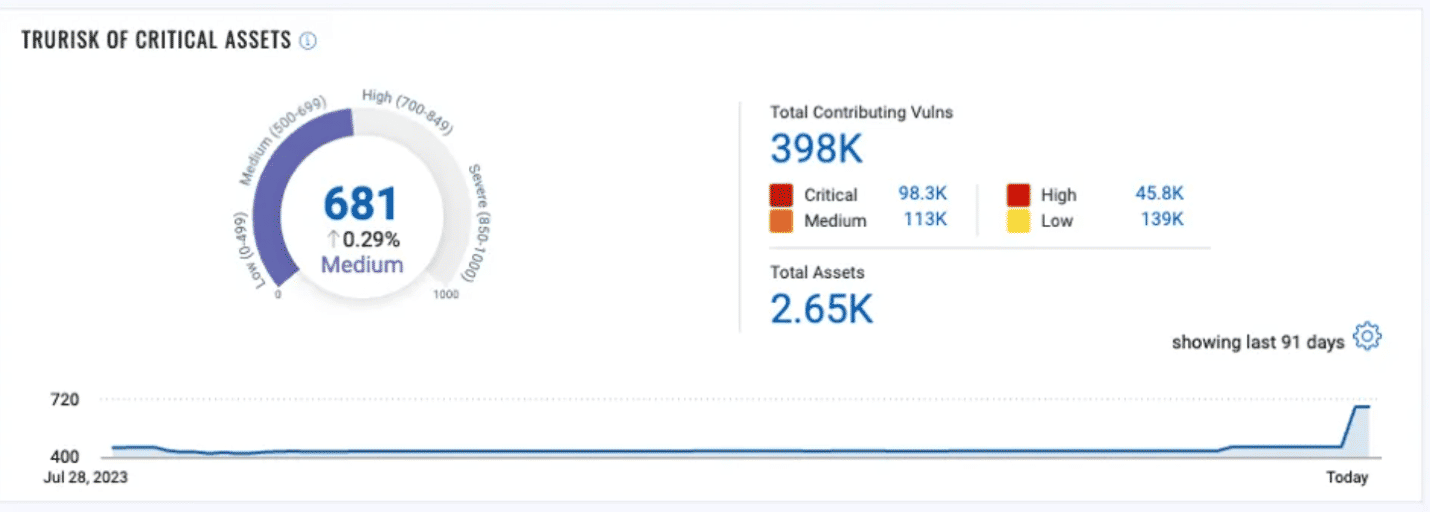
Qualys VMDR with TruRisk greatly simplifies prioritization criteria by translating the risk associated with vulnerabilities, assets, and asset groups into easy-to-understand TruRisk scores. Vulnerabilities are scored on a scale from 1-100, with 90-100 earmarked for critical vulnerabilities. This category includes vulnerabilities actively exploited in the wild, those with weaponized exploits available, and those exploited by ransomware groups or different types of malware.
What is the difference between vulnerability management and vulnerability assessment?
As previously mentioned, vulnerability management is the process of continuously finding, assessing, and prioritizing vulnerabilities and misconfigurations to fix those that present a risk to the business. This is an ongoing, continuous process that is strategic in nature, incorporating not only the monitoring and identification of vulnerabilities, but their prioritization based on many factors, as well as their remediation with the goal of de-risking the business.
Vulnerability assessment, on the other hand, is a subset of vulnerability management that focuses on the identification and quantification of vulnerabilities in an organization’s environment. This more technical process focuses on producing a list of vulnerabilities. The assessment does not extend to remediation or the continuous management of vulnerabilities.
7 Signs Your VM Program Might Be Failing
Setting up an effective and efficient vulnerability management program for your organization’s particular needs isn’t as simple as one might think. When evaluating your VM program, there are seven signs that it might be in need of a reset:
Too many tools, few solutions: Legacy VM programs lack natively integrated options, such as the ability to expand asset visibility coverage with attack surface management or automated remediation of identified vulnerabilities with patch management. For many, the result is poor visibility due to brokered tools, disjointed workflows between teams, and ultimately slower MTTR and friction between security, IT Ops, and compliance that contribute to higher risk.
Poor Visibility of Internal and External-facing Assets: “You can’t protect what you can’t see.” This security maxim applies to all assets on the enterprise network. And especially external-facing assets, which, if unprotected, are easy prey for attackers. Almost 40% of a typical enterprise’s assets are unknown to security teams, according to the Qualys Threat Research Unit (TRU). Many are vulnerable to attack if unpatched. TRU found that 4% of cloud assets within more than 50 million scanned are external facing, of which 50.84% were unpatched. Talk about being blind to severe risk! Risk-based vulnerability management (RVBM) requires total visibility of all your assets, for without total visibility, your organization lacks comprehensive protection from cyber risks.
Remediation Slower than Average Time to Weaponization: Security and IT teams need to prioritize fixing the most critical vulnerabilities that will reduce the greatest business risk.
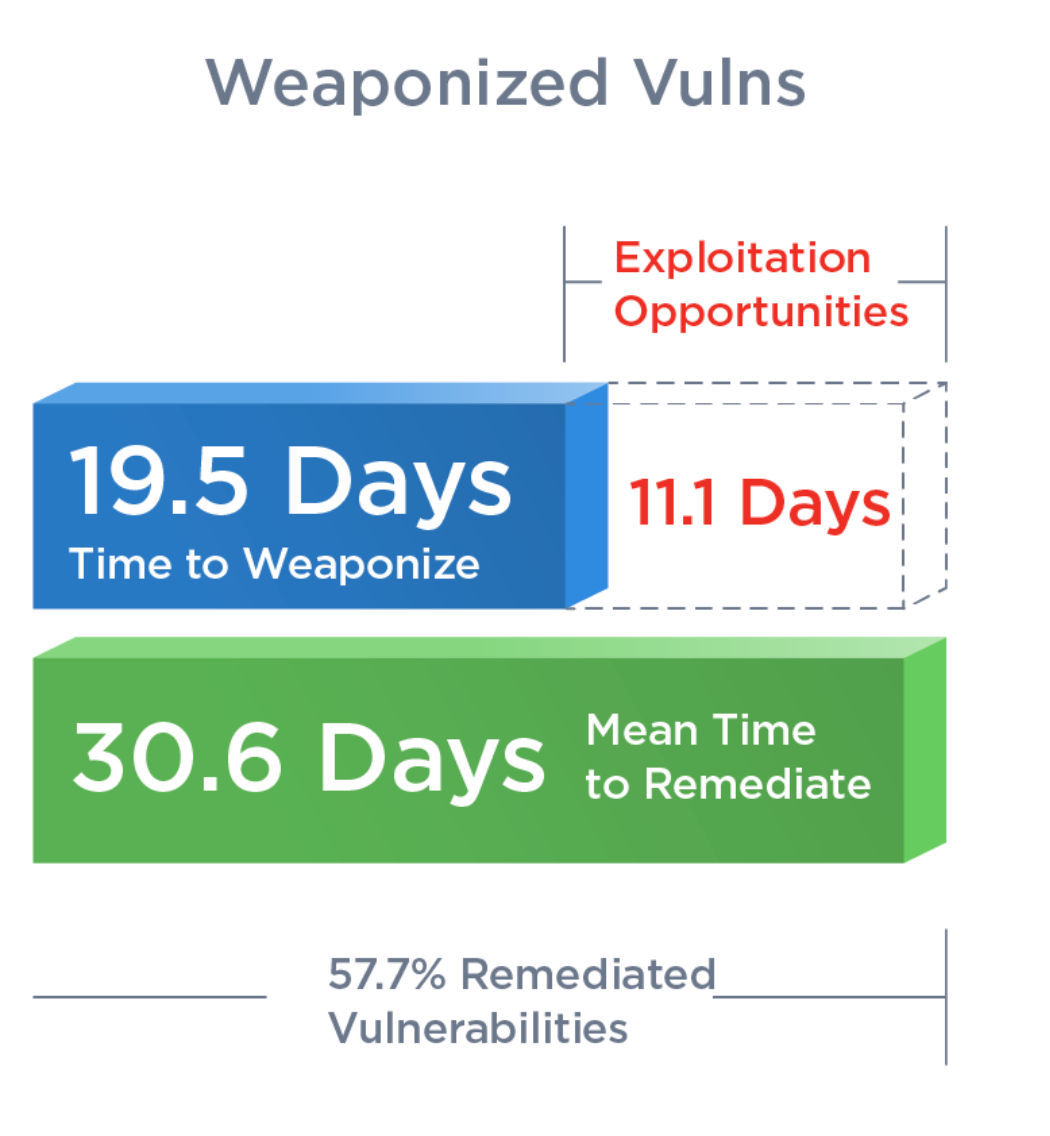
According to TRU, during 2022:
- Patching — On average, weaponized vulnerabilities are patched within 30.6 days while only being patched an average of 57.7% of the time.
- Weaponization — These same vulnerabilities are weaponized by attackers in 19.5 days on average.
- Exploitation — Attackers have 11.1 days of exploitation opportunities before organizations begin patching.
Speed is the key to out-maneuvering adversaries and reducing risk. VM solutions without natively integrated patch management and alternative remediation capabilities, such as virtual patching or scripting, are not a complete solution.
Vulnerabilities Lack Risk-based Prioritization: Identifying vulnerabilities is half the battle. Without risk-based scoring and prioritization, identifying and then addressing the most critical vulnerabilities first is a time-consuming task. Teams are often busy with non-essential tasks and leave urgent remediation actions unaddressed. Less than 5% of all vulnerabilities are truly critical, according to TRU. VM without transparent risk and business context risk scoring is not effective VM. It may be a waste of time and money — and expose the organization to tremendous risk.
Custom Applications a Growing Blind Spot: Up to 60% of organizations today run their business using custom or “first-party” software. From manufacturing to banking, businesses of all types and sizes rely on first-party software to support their unique operational needs. The flexibility, however, also opens the door to unmanaged and unseen vulnerabilities that go unnoticed in source code, leaving businesses exposed. In fact, first-party software includes more than 96% of open-source components, of which 48%+ of these are highly exploitable.
Compliance Still a Time-consuming Headache: Compliance is a mandatory requirement for any organization that operates in highly regulated industries. Siloed compliance efforts and solutions are expensive, time-consuming, and often disjointed from their organization’s legacy VM solution. When an organization operates globally maintaining and reporting on compliance are even more challenging. For example, a VM solution that does not offer PCI compliance with a natively integrated compliance solution is a disadvantage for any VM solution.
Unable to communicate and measure risk in business terms: CISOs are under pressure to reduce their exposure to cyber risk while finding ways to better measure and communicate cyber risk in business terms to executive stakeholders. While CISOs have traditionally reported to the CTO or CIO, now it is common for CISOs to report directly to the CEO, expanding the responsibilities of the CISO beyond security-only tasks. Cyber risk is now business risk; the CISO must prove success or identify failures, fast.
The Vulnerability Management Process
Vulnerability management is a continuous process that allows teams to do the following:
- Measure: Effective vulnerability management should measure risk across vulnerabilities, assets, and groups of assets to help organizations proactively reduce risk exposure and track risk reduction over time. It also needs to offer complete asset context and visibility to add business context, tags, identify crown jewels, enhance visibility by seamlessly integrating with CMDB’s as well as third-party & ITSM solutions, and prioritize based on risk of exploitation, likelihood of exploitation or evidence of exploitation and business impact.
- Communicate: VM should also empower an organization to effectively communicate risk across different teams, business units, and geographic locations by leveraging dashboards, reports, and ITSM tools. It should also offer the ability to assign remediation and mitigation tasks to rightful owners and close them out upon completion. Then, it should offer reports to share the state of VM’s proactive security efforts with executives to understand the latest trends and landscape of risk for your organization.
- Eliminate: Once you have identified the risks that pose the greatest risk to the business and then communicated them to IT, the final step is to eliminate that risk. A truly complete VM program encompasses the ability to leverage multiple avenues from remediation to mitigation and block attack paths to eliminate risk. It should precisely identify patches to remediate vulnerabilities and automatically remediate low-impact, high risk vulnerabilities with zero-touch automated patching.
How to assess VM solutions:
- Risk-based Vulnerability Management: In VM, more alerts do not equal more security. Cybersecurity solutions, in general, and vulnerability management specifically, need to do more to accurately detect and prioritize vulnerabilities based on cyber risk. Enterprises should demand automated and risk-based alert prioritization that allows security practitioners to focus on the vulnerabilities most critical to their specific and unique business environment.
- Vulnerability Detection: Vulnerability management solutions are only as robust as the data they can obtain and leverage for vulnerability identification and intelligent management. Regretfully, not all VM solutions are equal in their detection ability. Security practitioners should look for VM solutions that continuously monitor your perimeter, cloud, and internal systems and can identify rogue or unknown devices in your network. Be sure to test any VM solution’s ability to prioritize vulnerabilities based on threat intelligence feeds and business-critical assets to make sure that the scan results you receive are beneficial for informed and efficient response.
- VM Beyond Detection: Traditional VM products merely scan your networks and report on the data they discover. This conventional scanner-based approach typically runs vulnerability scans once every few days, resulting in outdated information and elevated risk exposure. Comprehensive VM solutions track the state of your systems to provide an ongoing, always up-to-date view of your security posture. Integration and orchestration with endpoint security offerings such as EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) should also be considered, as VM solutions are inevitably deployed alongside endpoint security solutions. When building your VM strategy, make sure your solution leverages a robust agent-based approach and works well with your current or planned EDR or XDR solutions, assuring that you can leverage VM for the detection, identification, prioritization, and response to vulnerabilities, wherever they are.
- Deployment and Perimeter Coverage: Traditional VM solutions installed within your networks require users to acquire, configure, and manage vulnerability management servers, perform backups on them, and handle patch updates on a continuous basis. In contrast, a more comprehensive vulnerability management solution should not require ongoing updates or database backups. Your VM solution should be able to automatically cover your evolving network perimeter, diverse endpoints, and the adoption of cloud services to cover multiple site locations. When assessing your vulnerability management strategy, make sure the solutions you rely on provide your organization with the scalability required to handle new devices, users, and locations to anticipate the inevitable changes that will happen to your network perimeter over time.
- Capex and Hidden Costs: Some VM software solutions lock you in with up-front investments in equipment and require ongoing updates, database backups, etc. This can couple high upfront capital expenditures (CapEx) with potential hidden costs along the way. When selecting a vulnerability management solution, be sure to evaluate the solution’s capabilities against its cost of implementation and cost of ongoing management to accurately assess the TCO over time. Modern vulnerability management solutions should be accessible directly via a browser and scale easily to handle new devices, users, and locations.
Why VM Should be Part of a Unified Solution
In the ongoing effort to identify and remediate the biggest business risks, even the most advanced VM solution can’t win the battle alone. That’s why it’s important to find a platform that combines as many different cybersecurity areas as possible under one roof for truly universal risk management, including:
Attack Surface Management (ASM): ASM is a comprehensive approach to identifying, analyzing, and mitigating potential security risks within an organization's attack surface. It goes beyond reactive security measures and adopts a proactive stance, continually monitoring and assessing the evolving threat landscape, with a focus on inventory and risk assessment of every cyber asset within the organization. The key element is “risk assessment.” It’s one thing to build a static inventory of assets, but true attack surface management includes the risk context that drives stronger vulnerability management and remediation.
Find out more about Attack Surface Management.
Vulnerability Management, Detection, and Response (VMDR): Vulnerability Management, Detection, and Response (VMDR) is a continuous, seamlessly orchestrated workflow of automated asset discovery, vulnerability management, threat prioritization, and remediation. By adopting the VMDR lifecycle, organizations decrease their risk of compromise by effectively preventing breaches and quickly responding to threats. In this way, organizations can safely pursue and extend their digital transformation, which has become essential for boosting competitiveness.
Find out more about Vulnerability Management, Detection, and Response.
Web Application Security: Modern web application security involves a set of practices, methodologies, and tools designed to protect web applications and online services from threats and vulnerabilities. These practices are essential for ensuring the confidentiality, integrity, and availability of web-based applications and the data they process.
Find out more about Web Application Security.
Patch Management: Patch management is a critical aspect of cybersecurity, involving managing updates for software applications and technologies. It includes identifying, acquiring, installing, and verifying software applications and systems' patches (updates or fixes). Effective patch management is vital for correcting security vulnerabilities, enhancing functionality, and ensuring the operational integrity of software. Find out more about Patch Management.