Complimentary Survey Report
Reducing Attack Surface: SANS Second 2016 Survey on Continuous Monitoring Programs
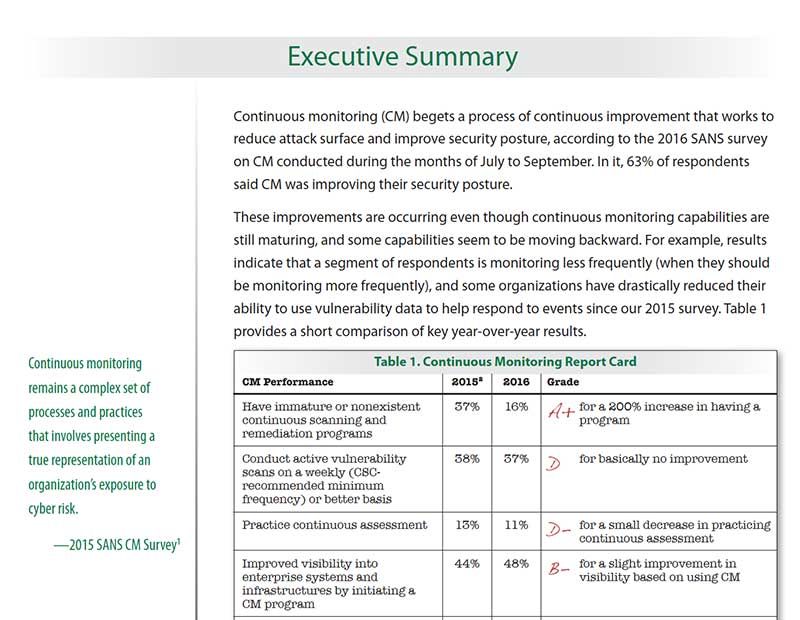
Continuous monitoring remains a complex set of processes and practices that involve presenting a true representation of an organization’s exposure to cyber risk.
One of the biggest challenges faced by IT security teams today is how to get an accurate picture of their organization’s exposure to threats.
A new survey by the SANS Institute focuses on determining how organizations conduct continuous vulnerability assessment and remediation related to the CIS Critical Security Controls 6.0.
Read the survey report to learn:
- What drives organizational use of continuous monitoring
- Which data assets should be included in assessments
- How mature continuous scanning and remediation efforts are
- The most commonly discovered types of vulnerabilities
Download report
By submitting this form, you consent to Qualys' privacy policy.