Free Guide
Narrowing The Security Gap With Automated Configuration Assessment
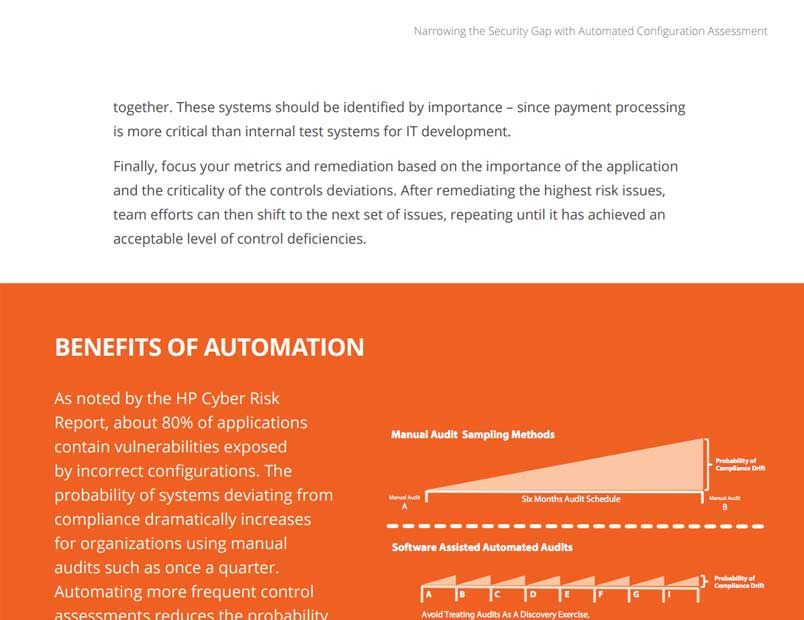
As a security professional, you are on constant alert for external threats. But many breaches are caused internally by incorrect configuration of IT resources. According to HP, 80% of applications contain vulnerabilities caused by incorrect configuration. How do you find these and ensure that system settings stay correct? In this guide you will learn how Qualys Policy Compliance lets you automate IT configuration assessments for stronger security and compliance.
Download the guide now to learn more about:
- How incorrect configurations cause severe vulnerabilities
- Best practices to help you find and enforce configuration policies
- Benefits of automating configuration assessments
- How to reduce risk from incorrect configuration of IT resources with an easy, automated solution to maintain correct settings
Download guide
By submitting this form, you consent to Qualys' privacy policy.