Complimentary eBook
Is Your Vulnerability Management Strategy Falling Behind?
Discover 7 Telltale Signs!
Is your current Vulnerability Management (VM) strategy leaving your organization exposed to potential threats? It's time to find out!
In our latest eBook, 7 Signs Your Vulnerability Management Is Failing, we unveil the critical challenges faced by legacy VM solutions and why making the switch to Risk-Based Vulnerability Management (RBVM) is a game-changer for your security posture.
Why You Need to Upgrade to RBVM
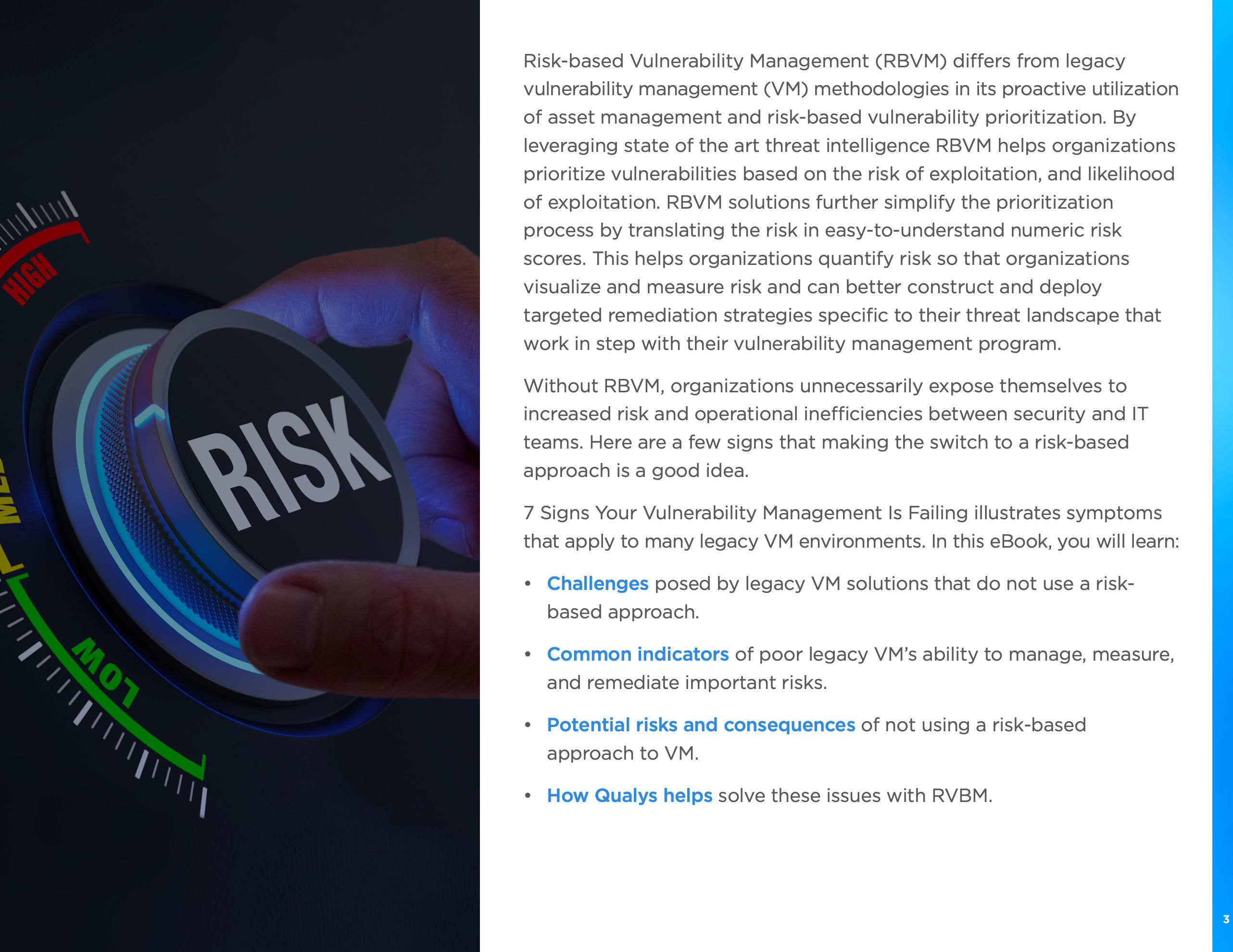
- Proactive Risk Management: It’s time to say goodbye to reactive approaches. RBVM utilizes cutting-edge threat intelligence to prioritize vulnerabilities based on their risk and the likelihood of exploitation.
- Numeric Risk Scores: No more guesswork—now you can quantify your risks effectively. RBVM simplifies the prioritization process, translating risk factors into easy-to-understand numeric scores.
- Targeted Remediation: Ready to effortlessly achieve synergy between security and IT teams? RBVM empowers you to construct and deploy highly targeted remediation strategies tailored to your unique threat landscape.
Download your copy of "7 Signs Your Vulnerability Management Is Failing" today to take your first step towards a more secure and proactive cybersecurity approach.
This eye-opening guide will show you how a Risk-Based Vulnerability Management solution by Qualys can help you tackle your toughest VM challenges head-on, bolster your security defenses, and streamline your vulnerability management program from end to end.
Download Infographic & Playbook
By submitting this form, you consent to Qualys' privacy policy.