Are Your Publicly Facing Websites Vulnerable to Log4Shell?
The Qualys’ research team has created specific tests to quickly identify if your websites are vulnerable.
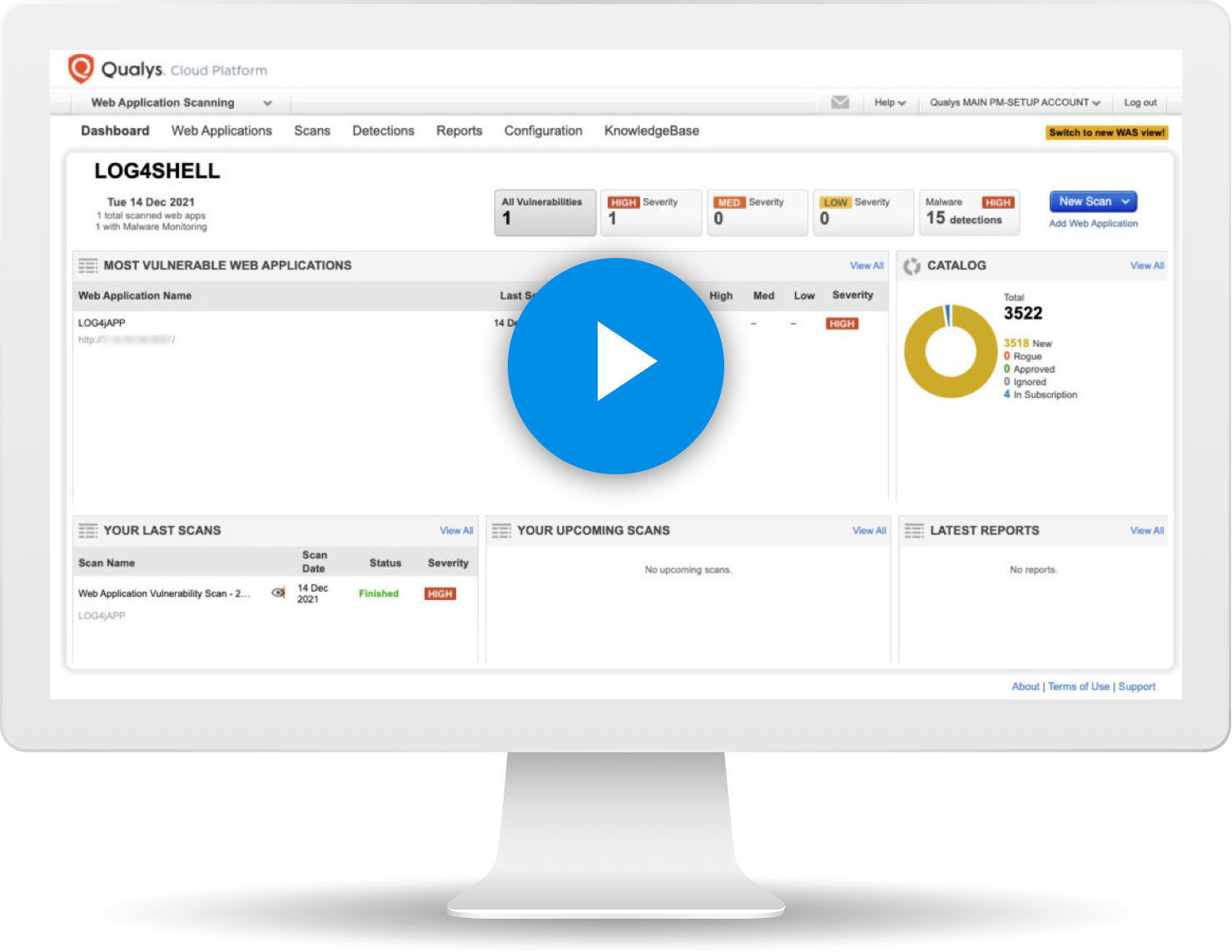
Attackers are already leveraging Log4Shell to attack internet facing websites. Attackers will likely target your internet-facing applications first. As such Qualys recommends all its customers use Qualys’s Web Application Scanner, as soon as possible, to scan their external websites for the Log4Shell (CVE-2021-44228) vulnerability.
Web Application Scanning (WAS)
Scan your internet facing web applications and APIs to find applications that are vulnerable to Log4j2 (CVE-2021-44228).
Scan From the Cloud
All scans are done directly from the Qualys cloud and do not require customers to install any software or make any network configuration change, allowing customers to leverage this capability without delay.
Log4Shell Detection Logic
Qualys researchers have created highly accurate tests that simulate common Log4Shell attacks in order to detect vulnerable web applications. Qualys research team is constantly working on expanding its Log4Shell detection logic and will constantly update Log4Shell related signatures as soon as needed.
Create your 30-day account
Enable Qualys Web Application Scanner for 30 days with no cost
By submitting this form, you consent to Qualys' privacy policy.