Implement CISA’s Shields Up Guidance
Risk Assessment & Remediation Service, No Cost for 60 Days
Assess and remediate your exposures
Given the heightened global risk environment as a result of the Russia/Ukraine conflict, Qualys remains committed to the security of our customers and their data now more than ever.
Our Cybersecurity Risk Assessment service leverages Qualys' leading-edge security research and CISA, MS-ISAC, and NIST guidance to proactively identify, prioritize, track, and remediate assets exposed to attacks emanating from Russia and beyond. A single, dynamic dashboard allows users to view critical vulnerabilities and drive prioritized remediation workflows to continuously monitor for cyber risk. The service includes:
Identification of internet-facing assets and security blind spots
Inventory all your assets and monitor your external attack surface. Qualys provides comprehensive visibility of your external-facing IT infrastructure by natively correlating asset telemetry collected by Qualys sensors (e.g. internet scanners, cloud agents, passive sensors) and key built-in integrations such as Shodan.io and Public Cloud Providers.
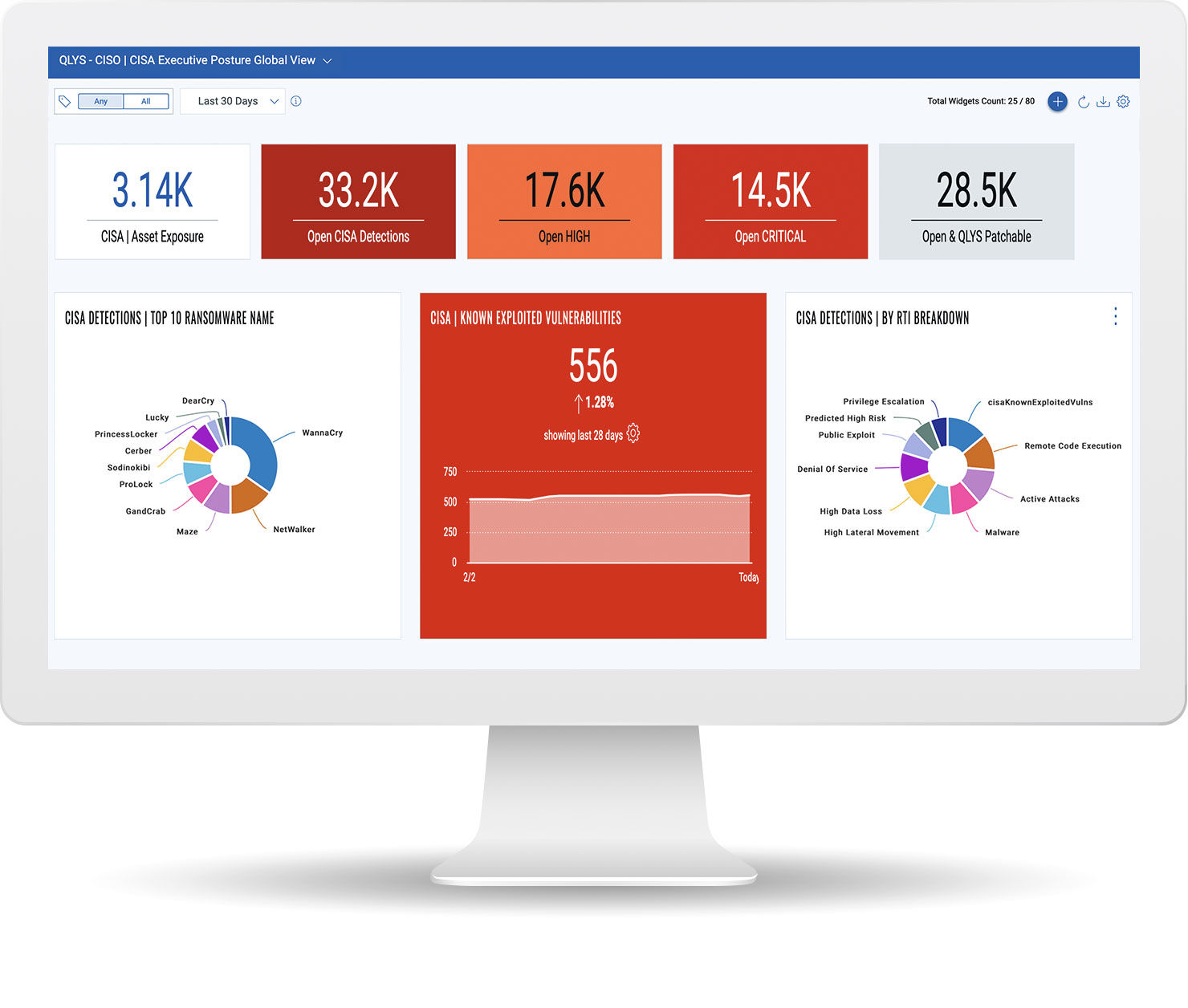
Detecting, prioritizing and remediating CISA-cataloged vulnerabilities known to be exploited by Russian state-sponsored actors
Qualys' Vulnerability KnowledgeBase includes all 300+ CVEs from CISA’s known exploited vulnerabilities. These can be filtered and prioritized to focus on CISA-exploited open vulnerabilities in your environment, with relevant patches applied automatically to remediate those vulnerabilities and protect yourself now and in the future from Russian state-sponsored actors.
Detection and disabling all non-essential ports and protocols on internet-exposed assets
Visibility into your open ports, and services running on each. Qualys supports extensive query language that enables teams to report and act on detected external-facing assets that have a remote-control service running (for example, Windows Remote Desktop).
Ensuring that all systems are protected with up-to-date antivirus/anti-malware software
Flag assets within your inventory that are missing antivirus, or with signatures that are not up to date. Qualys allows you to define software rules and assign required software on a specific scope of assets or environment. For example, all database servers should have antivirus and a data loss prevention agent. Proactively protect, detect, and respond to Malware, Indicators of Compromise (IOC), and ATT&CK techniques.
To learn more, read our blog post titled Russia-Ukraine Crisis: How to Strengthen Your Security Posture to Protect against Cyber Attack, based on CISA Guidelines.
Listen to our recent webcast on responding to this cyber threat: How To Implement CISA's Shields Up Guidance
Create your 60-day account
By submitting this form, you consent to Qualys' privacy policy.