Qualys Continuous Monitoring.
A continuous monitoring tool that alerts you in real time about network irregularities.
Next-generation cloud service for identifying threats and monitoring unexpected network changes before they turn into breaches
![Regional Medical Center]()
The Qualys Cloud Agent helps our medical center improve its vulnerability management efforts and achieve the real-time, continuous security the security team sought.
Information Security Analyst
Handling Cyber Operations a Large,
Regional Medical Center
Add custom alerts to your vulnerability assessment program for immediate response

Qualys Continuous Monitoring Highlights
Combine continuous monitoring and vulnerability management
The deep, native integration between Qualys Continuous Monitoring and Qualys Vulnerability Management Detection Response generates a new approach to information security in which you continuously identify and proactively address potential problems, instead of waiting to respond to incidents.
A wizard guides you step by step in the process of setting up Qualys CM, including configuring your rulesets, your monitoring profiles and your notifications
- MONITORING PROFILES: This defines where (i.e. which systems) you want to monitor. You can identify systems to monitor via asset tagging or by IP or by IP range
- RULESETS: This defines what (i.e. which events) you want to monitor. For example, you can define rulesets to only monitor for new ports on non-Windows systems. These rulesets can be defined at a granular level so recipients get alerts only for events relevant to them
- NOTIFICATIONS: This defines who (i.e. which individuals or teams) receive alerts. All alerts display on the Alerts Dashboard, but you can define subsets of alerts that go via email to specific individuals or distribution groups. You can define different distribution groups for different sets of alerts, and you can configure individual alerts or digests summarizing alerts over different timeframes
Be alerted right away about vulnerabilities, misconfigurations and other issues that can put you at risk of breaches, including:
Sharpen and streamline your network security
By constantly monitoring your network for changes that could put you at risk, Qualys CM gives you a comprehensive and up-to-date view of your IT environment, letting you reap a variety of benefits, including:
-
Unparalleled breach prevention
- Discover threats and unexpected changes before hackers do
- Know what hackers can see on your perimeter and internal IT assets
- Get alerted to anomalies in your critical assets
- Mitigate vulnerabilities before they get exploited
-
Outage prevention
- Catch expiring SSL certificates before service gets disrupted
- Apply alerting policies consistently across all your perimeter systems
-
Time and money savings
- Quickly identify highest priorities for IT security teams
- Target alerts for each issue to the people responsible for fixing them
- Free security teams from sifting through long reports
-
Regulatory compliance
- Address mandates like NIST 800-53 that require continuous monitoring
- Gain immediate visibility – without waiting for periodic scans
- Reduce risk of system changes going unnoticed
- Boost auditors’ trust


Customize alerts
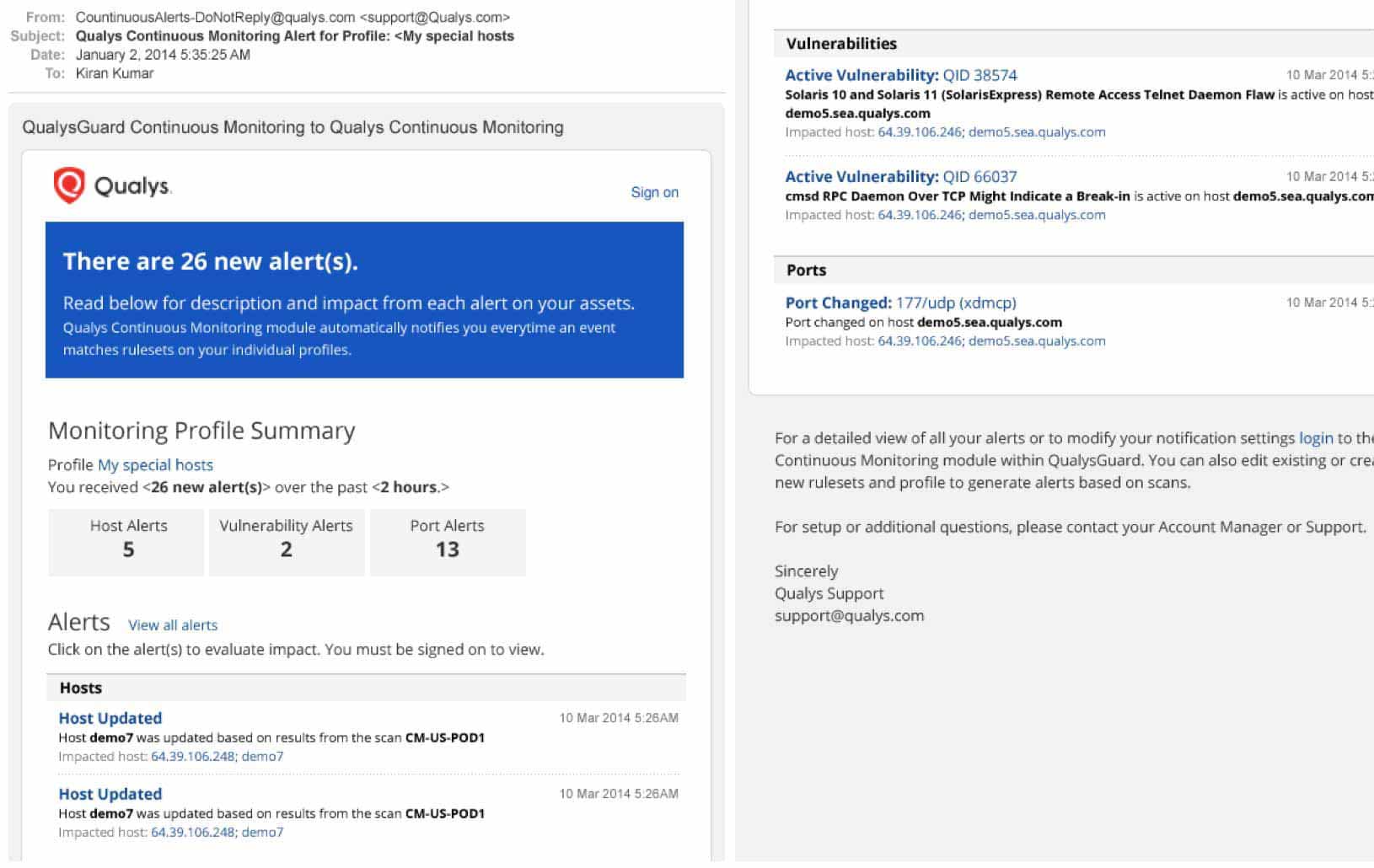
For continuous monitoring and quick detection of security and compliance problems to be effective, it’s also necessary that the appropriate staffers be notified, so that prompt action can be taken. Email notifications feature intuitive layouts and are rich in context and content, giving recipients a succinct yet complete account of events.
-
Leveraging a policy engine, notifications are sent to specific first responders on operations teams responsible for priority assets requiring remediation
-
Multiple intervals can be set for event notification, matching them to criticality levels, so that alerts for the most important events will be triggered right away, and on the other extreme, low level incidents are communicated once a day, or once a week
-
Alerts can be sent to people who are not authorized users of Qualys services but who nonetheless should be aware about urgent vulnerabilities or other important issues
-
Alert rules can be configured for common, general scenarios, or specific ones, and for multiple conditions affecting a variety of assets and elements
-
Security teams are freed from the delays and burdens of waiting for scheduled scanning windows and from sifting through long reports
-
Email notifications display the number of new alerts for each category in your selected timeframe. Alerts are also grouped by category. For each alert, you will see the impacted host’s IP address and hostname as well as other event specific details, such as the vulnerability detected, software added or open ports.
-
Using the Qualys CM API (application programming interface), you can integrate Qualys CM alerts with your Security Information and Event Management (SIEM) solutions


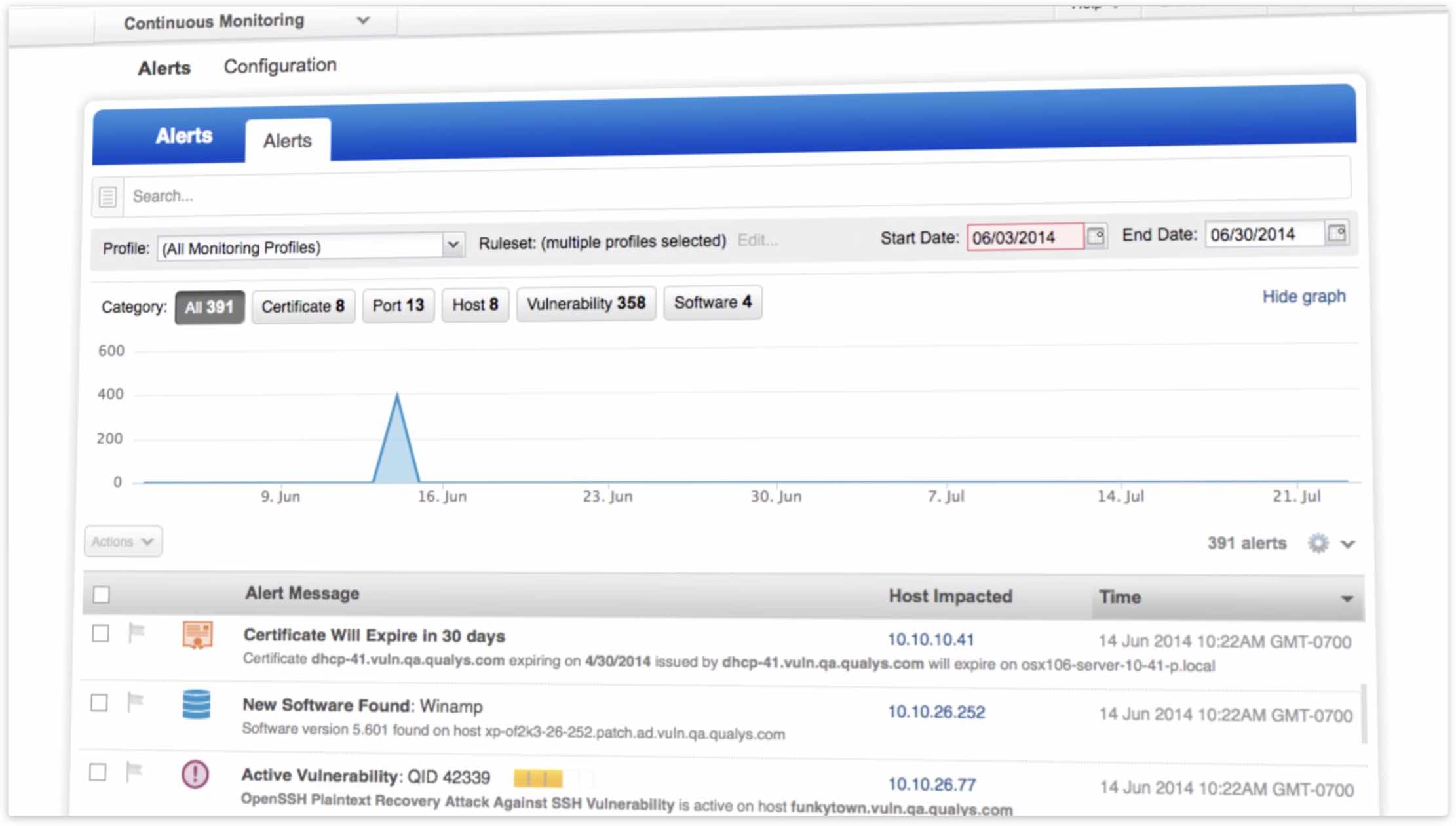
Immediate Insights
Qualys CM’s dashboard gives you a panoramic, comprehensive, graphics-rich, high-level view of your network, and lets you filter alerts in several ways. You can filter by category — such as Certificate, Host and Vulnerability) — and see all alerts that are configured and applicable within your environment. You can filter by date, so you get all alerts generated within a specified timeframe. These other dashboard features let you:
-
Closely monitor your security posture, issues and trends
-
Create customizable reports and views
-
Quickly and easily identify problem areas
-
Search alerts to, for example, get a historic view of events leading up to the current alert, or for forensic research
-
Make precise, informed decisions about appropriate actions to take by calling up granular details, such as:
- When and where an event occurred and what changes were involved
- What other alerts have been generated about the host involved in the incident, to help you correlate multiple alerts related to a single root cause. Host-level data available includes: vulnerabilities, new open ports, new or changed software

See for yourself. Try Qualys for free.
Start your free trial today. No software to download or install. Email us or call us at 1 (800) 745-4355.