By submitting this form, you consent to Qualys' privacy policy.
Email or call us at 1 (800) 745-4355
Transform Qualys Cloud Agents into passive sensors with a single click to monitor your networks for unmanaged and unauthorized devices.
Transform Qualys agents into passive sensors that sniff your network traffic, detecting unmanaged, unauthorized, and risk devices for VM scans and remediation.
Set the foundation for Zero Trust Architecture by proactively identifying devices that are unauthenticated, missing security agents, etc.
Bring previously unknown devices under management, scan for vulnerabilities and compliance issues, and prioritize remediation according to TruRisk.
No investment or resources required
Leverage the same Cloud Agent you’ve already deployed to enable passive sensing without the cost and friction of network taps.
Take immediate action
See a device that doesn’t belong. Set up rules that alert the appropriate IT team to remove it from the network in real time.
Turbocharge vulnerability management
Ensure the full scope of your attack surface is assessed for vulnerabilities—even IoT and rogue devices.
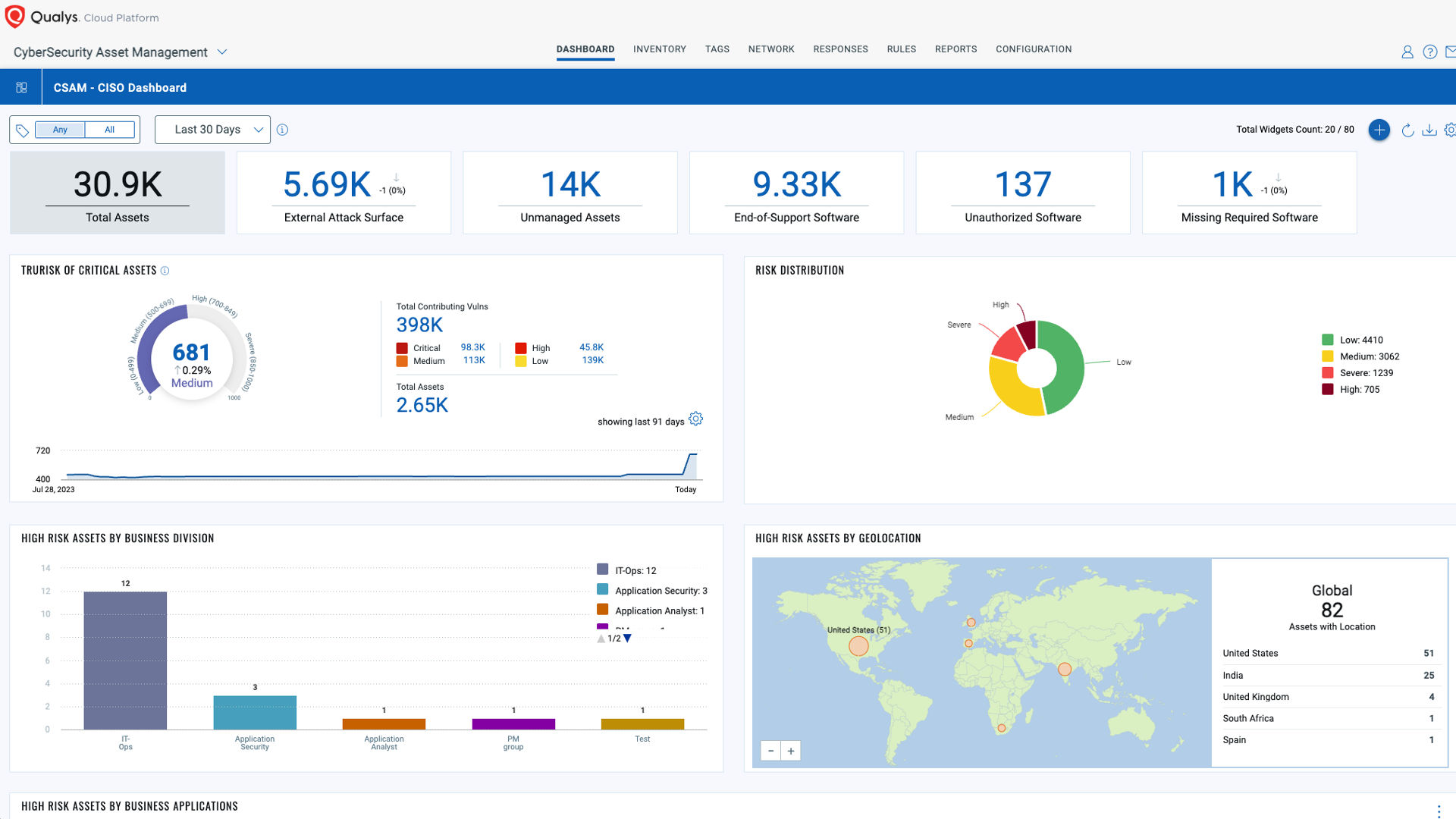
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.
By submitting this form, you consent to Qualys' privacy policy.
Email or call us at 1 (800) 745-4355
