By submitting this form, you consent to Qualys' privacy policy
Email or call us at 1 (800) 745-4355
Discover, track, and continuously secure Kubernetes and containers from build to runtime.

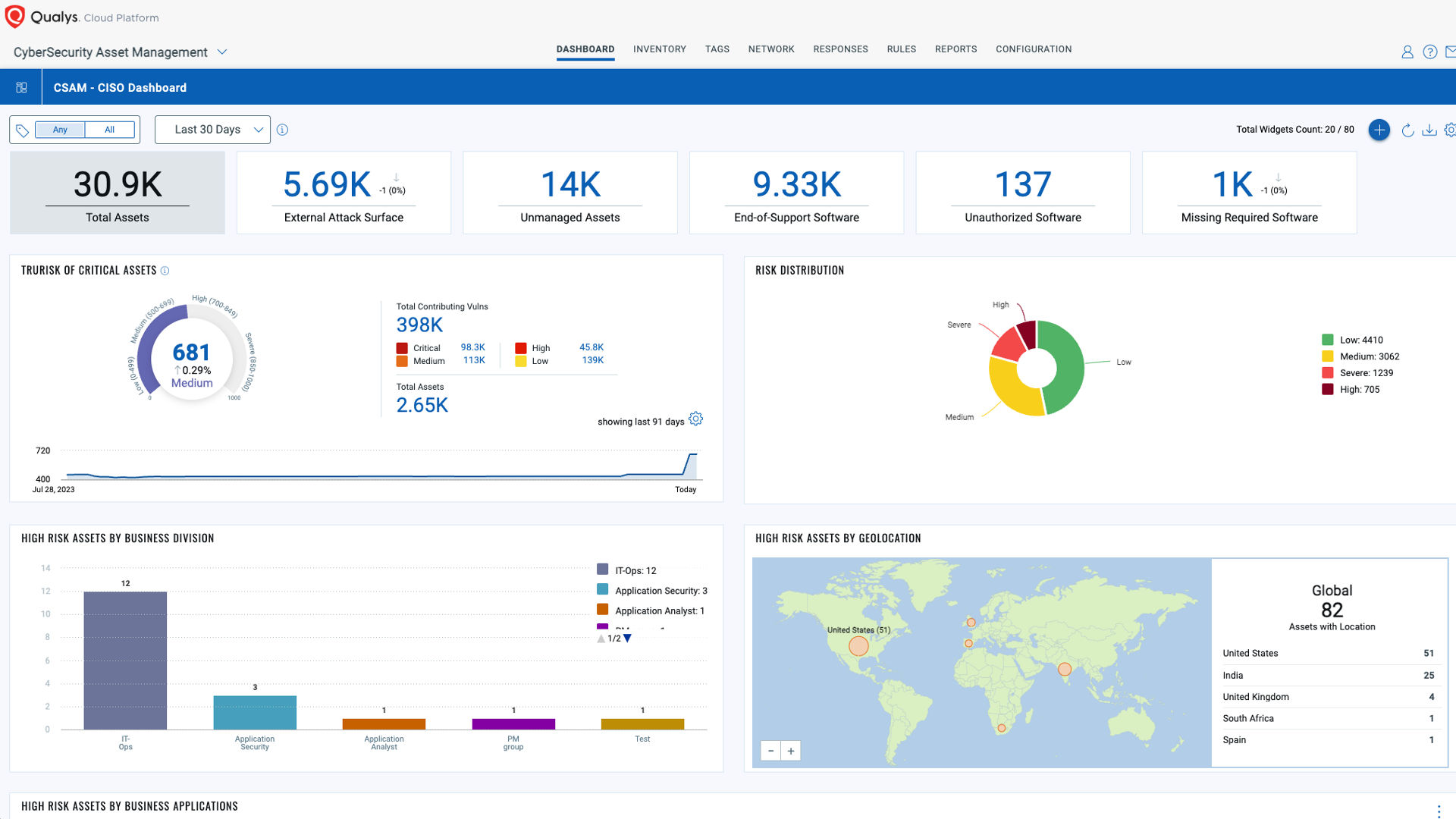
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.