Table of Contents
- What Is Kubernetes Security Posture Management (KSPM)?
- Why Kubernetes Requires a Specialized Security Approach
- Top Benefits of KSPM
- How Does KSPM Work?
- KSPM vs. CSPM: Understanding the Difference
- Why KSPM Should be Included in Your CNAPP
- KSPM Best Practices
- Must-Have Capabilities for Effective KSPM
- KSPM and Red Hat Considerations
- Optimizing KSPM with a Unified Platform
- Frequently Asked Questions
What is KSPM? Kubernetes Security Explained
It's been just over a decade since Google released Kubernetes, the open-source platform that revolutionized how organizations manage containerized applications. The same technology is used by millions of developers today.
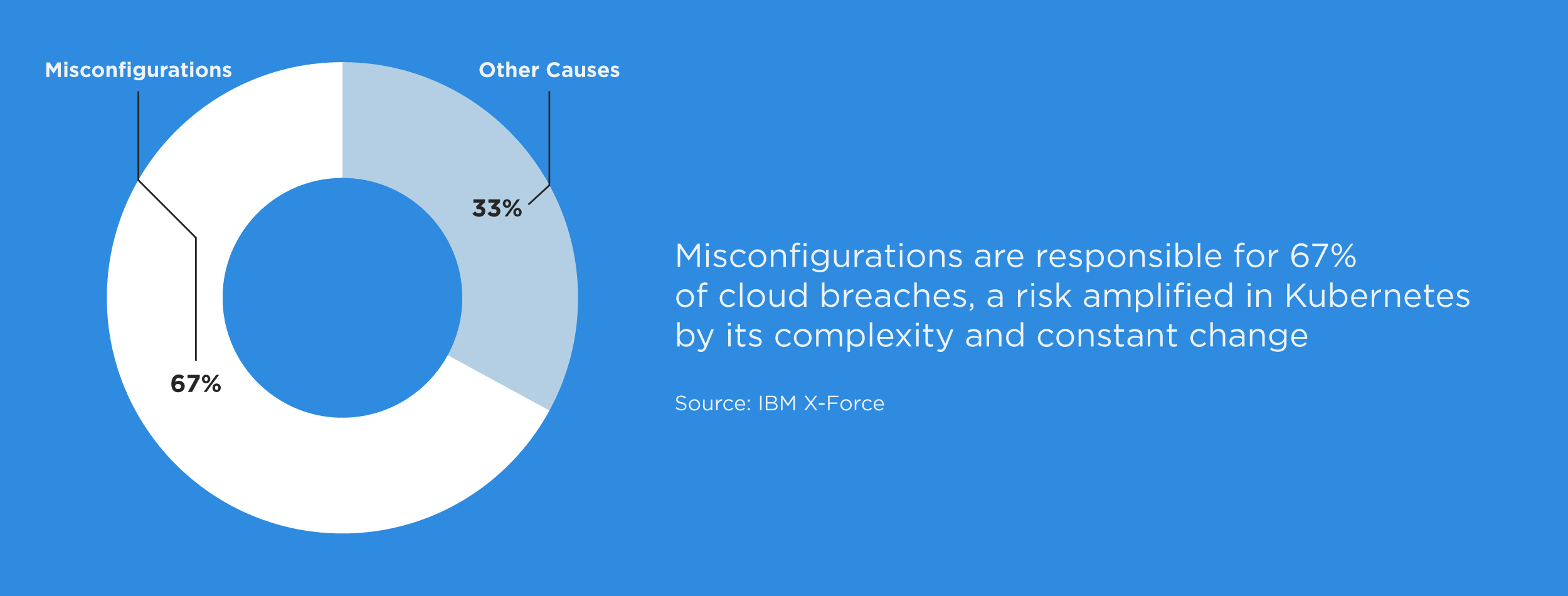
While Kubernetes streamlines the deployment and management of containerized applications by handling tasks like scaling, load balancing, and self-healing, its distributed architecture can introduce unique security challenges. The dynamic and ephemeral nature of Kubernetes clusters significantly expands a business' attack surface, necessitating a continuous, configuration-centric approach to maintain control over container security and mitigate risk in cloud-native environments.
Key Takeaways:
- KSPM continuously monitors and enforces best practices for configuration across Kubernetes clusters.
- KSPM is essential for managing risk in rapidly changing, cloud-native environments where traditional security tools often fall short.
- Core capabilities include misconfiguration detection, policy and control analysis, risk-based prioritization, and compliance reporting.
- KSPM complements CSPM and plays a critical role within a unified CNAPP platform, such as Qualys TotalCloudTM
What Is Kubernetes Security Posture Management (KSPM)?
Kubernetes Security Posture Management (KSPM) is the continuous assessment and enforcement of security and Kubernetes best practices across Kubernetes clusters, at both the control plane and workload levels. It focuses on reducing risk by identifying misconfigurations, enforcing security policies, and ensuring consistent configuration hygiene across:
- The Kubernetes control plane
- Cluster-native settings and policies
- Role-based access controls (RBAC)
- API server configurations
- Admission controls
- Network segmentation
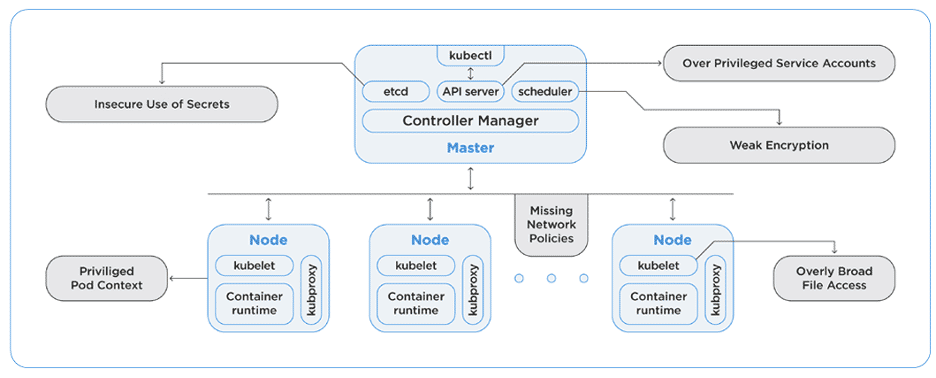
As Kubernetes becomes the backbone of modern workloads, including AI/ML and other data-intensive applications, its importance as a security priority continues to grow. With Gartner predicting that 95% of organizations will run containerized applications in production by 2029, Kubernetes environments have become a major target for attackers. KSPM equips teams to stay ahead by proactively managing configuration risk before it can be exploited.
Why Kubernetes Requires a Specialized Security Approach
Traditional security solutions were not designed to address the internal complexities of Kubernetes. Instead of protecting static infrastructure, security must evolve to manage the dynamic and highly distributed environments of the modern enterprise, which includes:
Multi-Layered Architecture
Kubernetes clusters comprise multiple components, including control planes, nodes, workloads, and APIs, which introduce their own category of risk. Securing them requires coordination across teams; for instance, vulnerabilities in base images may fall to platform or DevSecOps teams, while application-layer flaws need developer intervention. This fragmentation can complicate ownership and remediation.
It also creates openings for attackers when misconfigurations occur in high-value areas such as the control plane, where overly permissive role bindings or misaligned integrations can expose administrative paths. Even managed services like EKS or GKE are not immune, underscoring how central orchestration components remain prime targets.
Decentralized Configuration
Because Kubernetes environments are managed by different teams (often simultaneously), it's common for misconfigurations to go unnoticed, including insecure default settings or improperly provisioned configurations. Without a unified view or shared governance model, teams may apply conflicting settings, bypass guardrails, or overlook critical dependencies.
Issues such as overly permissive RBAC, insecure network policies, unauthenticated APIs, or misconfigured namespaces often arise from this decentralization and act as immediate entry points that enable attackers to gain footholds or move laterally inside the cluster.
Ephemeral Workloads
In Kubernetes, pods and containers are constantly starting, stopping, and shifting, sometimes in a matter of seconds. This rapid pace leaves no room for manual security checks. Instead, organizations need tools that can continuously track changes, detect misconfigurations as they occur, and enforce policies in real time.
Because clusters in public cloud environments are scanned or probed within minutes of deployment, these ephemeral workloads can expand exposure almost instantly, especially when static or periodic audits cannot keep up with the pace of container churn.
Watch How Scaled Container Security Is Governed Through Risk Operations.
Top Benefits of KSPM
KSPM is vital for businesses deploying containerized applications in cloud-native environments. By continuously assessing configurations and enforcing best practices, KSPM provides a centralized, real-time view of your clusters' security posture, helping identify risks early and maintain control at scale.
The top benefits of implementing KSPM include:
- Enhanced visibility: Gain a centralized view of security posture across Kubernetes clusters and environments, eliminating blind spots from both control and data planes.
- Proactive misconfiguration detection: Automatically identify risky configurations, such as exposed API servers or over-permissive RBAC roles, and tie them to relevant vulnerabilities before attackers can exploit them.
- Risk-based prioritization: Assess misconfigurations in context, using factors such as exploitability, exposure, and business impact to guide remediation efforts and identify the issues most likely to be exploited.
- Streamlined compliance: Map cluster configurations to industry standards with automated evidence collection to reduce audit preparation time and simplify ongoing compliance.
How Does KSPM Work?
KSPM assesses and enforces the security posture of Kubernetes clusters by focusing on their internal configuration and security controls. Rather than relying on external protections, KSPM helps secure critical components (e.g., namespaces, network policies, RBAC), ensuring that security best practices are consistently applied as clusters scale and evolve.
Discovery
KSPM begins with discovering and monitoring Kubernetes resources, configurations, and metadata to establish visibility across the environment. This includes:
- Scanning manifest files (YAML/JSON) and live cluster objects such as Pods, Deployments, Services, Config Maps, and Network Policies.
- Identifying exposed services and insecure network configurations, such as public-facing ports, missing network policies, or open ingress/egress paths that could allow unauthorized access.
- Auditing RBAC policies for violations of least-privilege principles, such as roles that grant unnecessary or overly broad access.
Configuration Assessment
Once discovery is complete, KSPM evaluates the collected data against established policies and benchmarks. This assessment identifies misconfigurations and policy violations that could introduce security risk or operational gaps, helping teams determine what needs to be addressed.
Risk Prioritization
After misconfigurations are identified, KSPM evaluates them against a defined set of Kubernetes controls to determine where policies pass or fail. In parallel, it connects these failed controls to a broader risk model that considers associated vulnerabilities, potential exploits, and blast radius. This dual view helps teams quickly identify the issues most likely to be weaponized and prioritize remediation accordingly.
Remediation
In addition to prioritizing risks, a KSPM solution typically provides clear remediation guidance for failed controls and misconfigurations, often leveraging best practices from benchmarks such as the Center for Internet Security (CIS). Many platforms also support automated remediation, but effective implementation must ensure that any changes made at runtime are reflected back in infrastructure-as-code templates to prevent configuration drift. This helps security teams resolve high-priority issues quickly while maintaining long-term consistency across the Kubernetes environment.
Reporting
Best-of-breed KSPM tools will also provide contextualized dashboards and audit-ready reports that make security posture data easy to understand. This helps security teams demonstrate posture improvements, communicate risk reduction efforts to stakeholders, and show how KSPM supports broader business goals.
KSPM vs. CSPM: Understanding the Difference
While Cloud Security Posture Management (CSPM) is a key part of cloud-native security, KSPM provides deeper container security by focusing on the internal workings of Kubernetes clusters. CSPM focuses on securing cloud service configurations such as identity and access management (IAM) roles, storage settings, and network controls. KSPM goes deeper, providing container- and cluster-level security by evaluating the internal workings of Kubernetes itself.
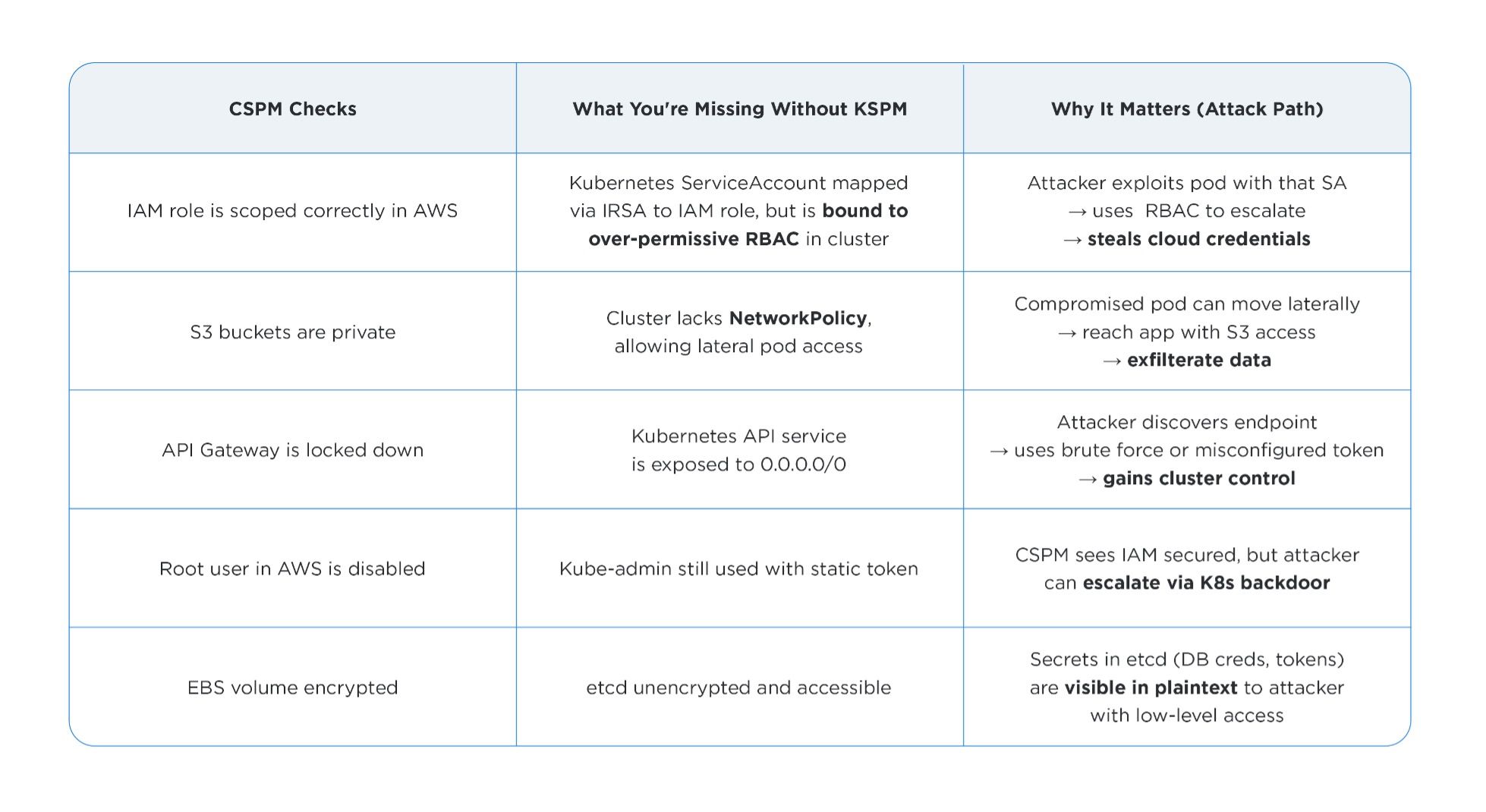
Why KSPM Should be Included in Your CNAPP
Cloud-Native Application Protection Platforms (CNAPPs) bring together key cloud security functions like posture management, workload protection, and identity governance into a unified set of tools. Rather than relying on separate solutions for each layer, CNAPPs provide a comprehensive view of cloud risk across infrastructure as a service (IaaS), containers, continuous integration and continuous delivery (CI/CD) pipelines, and more.
Within this broader framework, KSPM plays a critical role by focusing on Kubernetes clusters, one of the most complex and frequently misconfigured components in cloud-native stacks. KSPM capabilities secure the control plane, workloads, network policies, and access configurations inside Kubernetes, complementing CSPM to close a significant gap in cloud risk visibility.
KSPM Best Practices
To get the most value from KSPM, organizations need a disciplined approach rooted in proven best practices for reducing risk and scaling security across every Kubernetes environment.
These include:
Establish Control Plane Visibility
The Kubernetes control plane is the cluster's central management layer, responsible for scheduling, orchestration, and enforcing the desired state. Its elevated privileges mean a single misconfiguration can impact the entire environment. Strong KSPM means having continuous visibility into control plane settings, audit logs, and components so teams can detect and respond to risky changes before they escalate.
Use Industry Standards and Benchmarks
Industry benchmarks and security frameworks help define the policies that safeguard your Kubernetes environment. They provide a shared baseline that aligns teams around what "good" looks like. A strong KSPM solution continuously evaluates your cluster configurations against these standards, triggering alerts and prioritizing risks based on how far they deviate from best practices.
Essential resources include:
- The CIS Kubernetes Benchmarks (Center for Internet Security)
- Kubernetes Hardening Guide (NSA and CISA)
- Kubernetes Top 10 Risks (OWASP)
Enforce the Principle of Least Privilege
In Kubernetes, over-permissive access is one of the most common and dangerous misconfigurations. That's why it's crucial to use continuous RBAC audits to ensure that users, service accounts, and workloads have only the permissions necessary to perform their functions and nothing more. Pay close attention to service accounts used in CI/CD pipelines or across namespaces, as they can be exploited for lateral movement within the cluster.
Least privilege also applies to how containers and pods interact. Restrict communication paths between pods and between containers and the host to the bare minimum required. This will reduce the blast radius if a component is compromised.
Automate Reporting
Manual audit preparation in Kubernetes environments is resource-intensive and doesn't scale with dynamic infrastructure. KSPM tools help automate this process by tracking configuration changes over time, collecting evidence, and mapping findings to benchmarks like CIS and OWASP. This gives security leaders a defensible, real-time view of posture progress, which makes it easier to prove control effectiveness and align security with business priorities.
Must-Have Capabilities for Effective KSPM
Not all KSPM tools offer the depth required to secure complex Kubernetes environments. When evaluating a solution, look for capabilities that support continuous visibility, policy enforcement, and risk-based remediation at scale:
1. True Hybrid Kubernetes Coverage
A KSPM solution must span the full reality of enterprise Kubernetes: self-managed clusters, managed services (EKS, AKS, GKE), and OpenShift-on-prem and in the cloud. This is critical because managed platforms often introduce default configurations and inherited permissions that expand the attack surface and are frequently overlooked by posture-only tools.
2. Control Plane + Data Plane Visibility
- Control plane: RBAC, service accounts, admission controls, API access
- Data plane: workloads, networking, storage, runtime permissions
3. Risk-Based Prioritization Beyond Misconfigurations
- Correlate misconfigurations with vulnerability exploitability
- Identify toxic combinations (e.g., exposed workload + overly permissive RBAC + exploitable CVE)
- Prioritize based on attack feasibility and blast radius, not benchmark severity alone
4. Integrated Automation and Remediation
- Automated guardrails (policy-as-code, admission controls)
- Guided remediation tied to risk context
- Native integration with CI/CD, ITSM, and cloud workflows
5. Code-to-Cloud Protection
- Infrastructure-as-Code
- Container images and build pipelines
- Application and runtime context
KSPM and Red Hat Considerations
Organizations deploying Red Hat OpenShift often face challenges such as misconfigurations, insecure defaults, excessive permissions, and policy drift, which can expose Kubernetes environments to risk and complicate compliance efforts. OpenShift-specific constructs like Security Context Constraints (SCCs), integrated OAuth-based identity and RBAC mappings, and inconsistent use of sealed secrets or etcd encryption can unintentionally introduce privilege escalation, identity overreach, or sensitive data exposure.
Through Continuous Kubernetes Security Posture Management (KSPM), Qualys addresses these risks by delivering continuous visibility and control across OpenShift environments. It evaluates cluster configurations against benchmarks such as CIS for OpenShift, identifying insecure SCC assignments, excessive RBAC and identity permissions, mismanaged sealed secrets, and insecure defaults across control planes, nodes, and namespaces. By correlating findings with asset criticality and applying TruRisk™️ prioritization, Qualys enables security and platform teams to harden OpenShift clusters, reduce the attack surface, and maintain continuous compliance across hybrid and multi-cloud deployments.
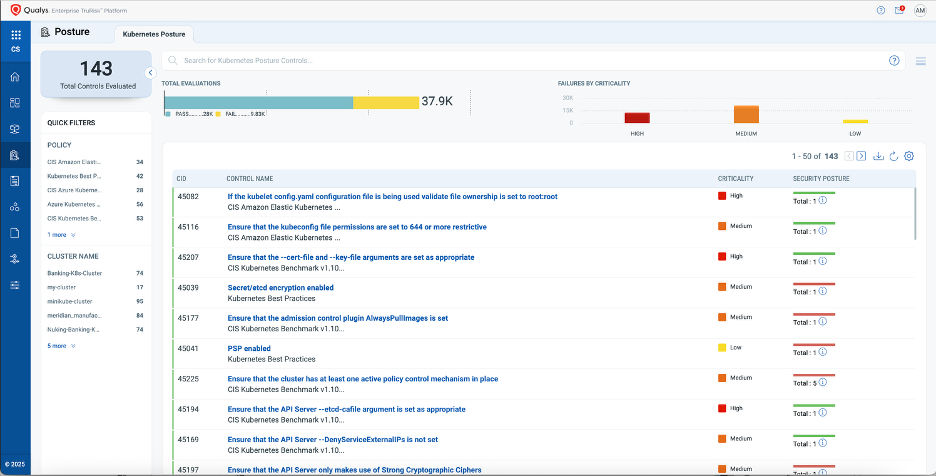
Optimizing KSPM with a Unified Platform
Kubernetes has become a cornerstone of modern application development, but its dynamic and distributed nature introduces unique risks that traditional security tools can't fully address. KSPM fills this gap by delivering continuous visibility, policy enforcement, and proactive risk reduction across clusters, all at the speed that cloud-native environments demand.
Qualys TotalCloud™ brings these capabilities together in a unified platform that integrates KSPM with CSPM, CIEM, and Cloud Workload Protection (CWPP). This end-to-end visibility and control empower teams to detect critical misconfigurations, enforce least privilege across complex environments, and stay audit-ready without the overhead.
Frequently Asked Questions
Do managed Kubernetes services require KSPM?
Yes. Even with managed Kubernetes services like AWS EKS, Google GKE, or Azure AKS, customers are still responsible for securing the configurations inside the cluster. KSPM helps ensure these internal layers are hardened and consistently monitored.
How does KSPM integrate with DevOps and CI/CD pipelines?
KSPM supports shift-left security by integrating posture checks earlier in the CI/CD pipeline, flagging risky configurations before they're deployed. Some platforms, like Qualys TotalCloud, can provide real-time policy validation and remediation guidance directly within developers' workflows.
Can KSPM detect runtime threats?
No, KSPM focuses on preventing misconfigurations and securing Kubernetes posture before runtime. However, when integrated into a CNAPP platform like Qualys TotalCloud, posture insights from KSPM can be correlated with real-time workload activity from CWPP, providing both preventive and runtime threat visibility.
What are common Kubernetes misconfigurations KSPM can help prevent?
KSPM is designed to prevent common misconfigurations that could have a high impact, such as overly permissive RBAC, missing network policies, and insecure secrets storage.
How do KSPM tools differ from traditional Kubernetes security tools?
Traditional Kubernetes security tools often rely on point-in-time scans or runtime defenses, which can miss risky configurations introduced earlier in the lifecycle. KSPM takes a more proactive approach by continuously monitoring configuration posture, identifying drift, and preventing misconfigurations before they impact production.