Qualys SCA is an add-on for Qualys Vulnerability Management, Detection and Response that lets you assess, report, monitor and remediate security-related configuration issues based on the Center for Internet Security (CIS) Benchmarks. It supports the latest out-of-the-box CIS benchmark releases of operating systems, databases, applications and network devices.
Qualys Security Configuration Assessment (SCA)
Automate configuration assessment of global IT assets.
Cloud solution for expanding VM programs with configuration scanning and simplified workflows to address configuration issues
Both vulnerability assessment and security control assessment capabilities are critical because many regulations prescribe technical control assessments (which drives SCA) and also explicitly prescribe vulnerability assessments.
Anton ChuvakinResearch Vice President & Distinguished Analyst, Gartner
Qualys SCA Highlights
Broad coverage
Accountability for controls
Qualys SCA controls are developed and validated in-house by Qualys security experts and certified by CIS. The controls are optimized for performance, scalability, and accuracy. Qualys SCA can be used in IT environments of any size, from small ones to the largest.
Ease of use
SCA’s CIS assessments are provided via a web-based user interface and delivered from the Enterprise TruRisk Platform, enabling centralized management with minimal deployment overhead. CIS controls can be selected and customized according to an organization’s security policies. This eliminates the cost, resource and deployment issues associated with traditional software point products for configuration management.
Reports and dashboards
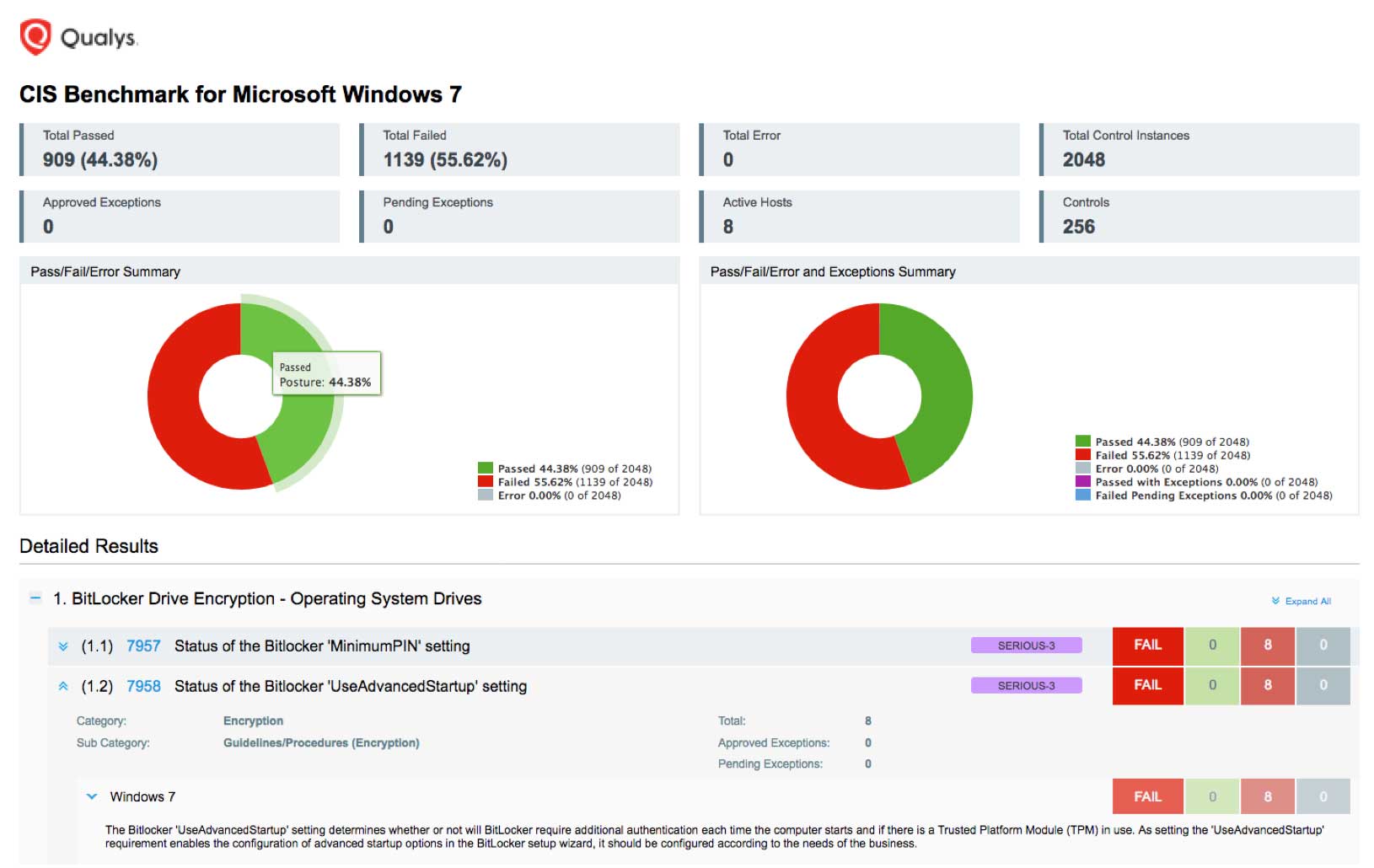
SCA users can schedule assessments, automatically create downloadable reports of configuration issues, and view dashboards for improving their security posture. This brings full circle Qualys SCA’s automation of security best practices behind leading benchmarks, and lets InfoSec teams take a proactive approach towards digital business security.
Augment your Qualys VMDR cloud service
Configuration assessment is an essential part of a comprehensive vulnerability management program. However, our competitors either combine lightweight vulnerability and configuration assessment, or offer the functionalities in separate products that aren’t integrated. Qualys gives you the best of both worlds. Qualys Vulnerability Management, Detection, and Response (VMDR) continuously scans and identifies vulnerabilities with Six Sigma (99.99966%) accuracy, protecting IT assets on premises, in the cloud and mobile endpoints. Qualys SCA, designed to work natively with Qualys VMDR, can be added seamlessly to your account with one click. Qualys SCA complements Qualys VMDR’s capabilities for detecting IT asset flaws with capabilities for assessment and reporting of configuration settings in 4 easy steps:
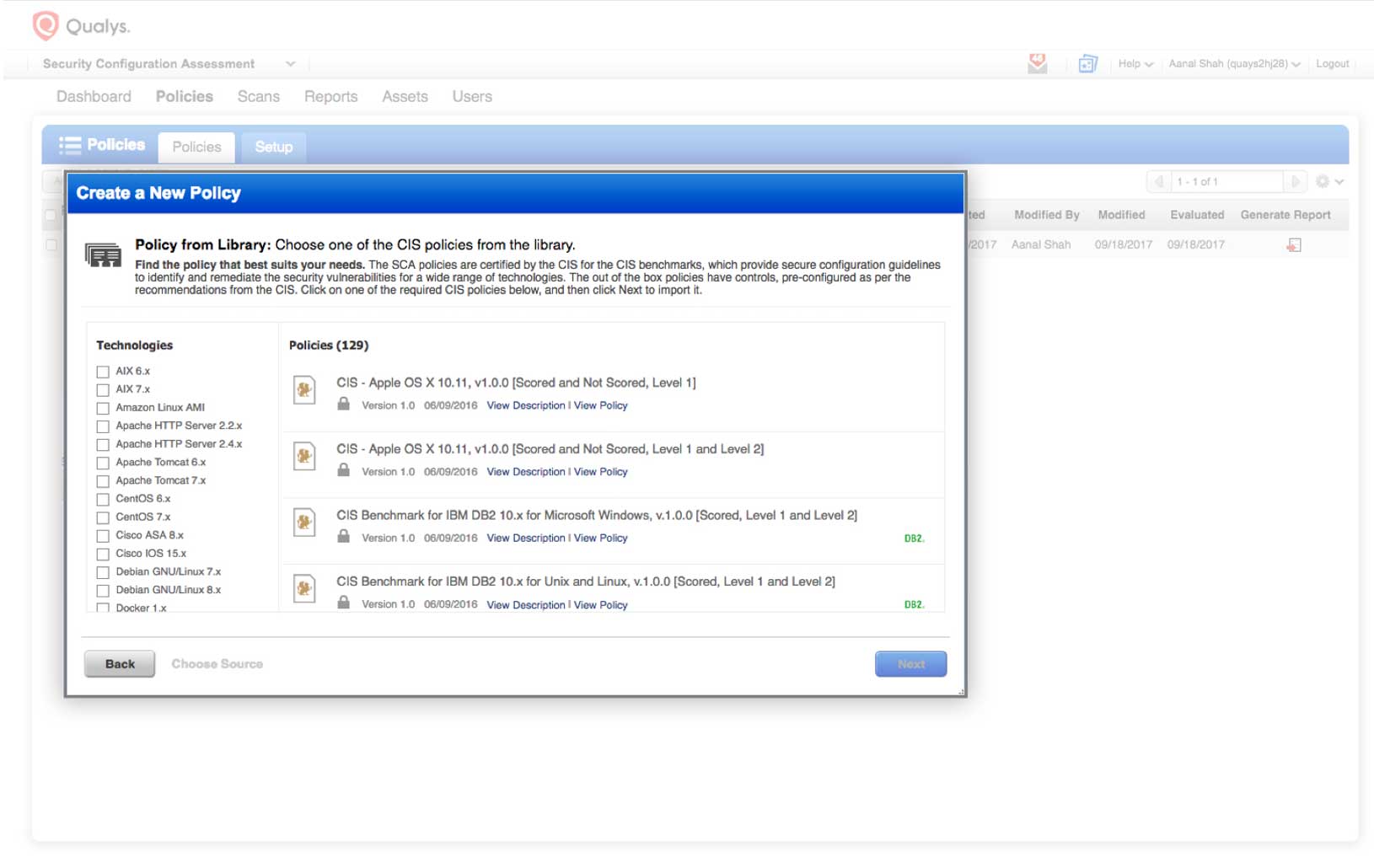
DEFINE: Import the applicable CIS policies in your subscription, and then customize the control values in the policy or policies per your security standards, or select/deselect the controls, all using Qualys SCA’s simple, web-based UI
ASSESS: Scan your IT assets and map the asset to the right CIS policy.
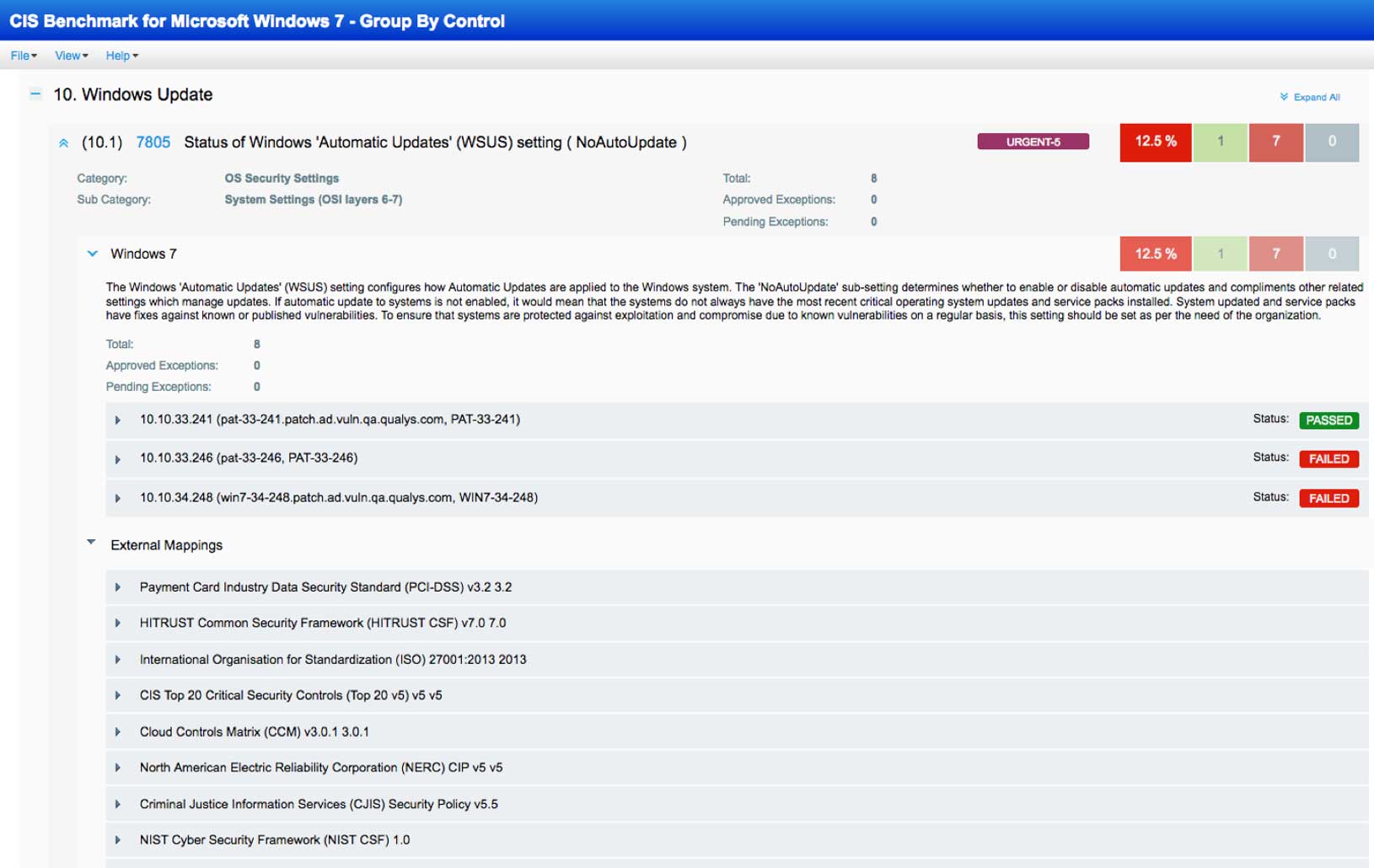
REPORT: Generate the report showing your control posture against the CIS Benchmarks, Qualys-provided remediation information, and the evidence for failure or passing, as well as the references to compliance standards. You can activate and deactivate controls as necessary for reporting purposes.
REMEDIATE: Remediate the failed controls, using Qualys-provided control remediation information.

Perform configuration assessments quickly and comprehensively
Improperly configured IT assets put your organization at an increased risk for breaches. However, it’s common for organizations to rush systems into production with default settings and without basic hardening. Addressing these issues is key for data protection, regulatory compliance, and secure digital transformation initiatives.
With Qualys SCA, you’ll be able to automatically and continuously check that your IT assets — on premises, in clouds and on mobile endpoints — are configured securely according to CIS guidelines. This will give your organization a solid foundation not only for security but also for compliance with most regulations like HIPAA and with industry mandates like PCI-DSS.
Providing the industry’s widest coverage for CIS Benchmark technologies, Qualys SCA assesses the configuration of elements such as:
Operating systems
Server software
Cloud providers
Network devices
Desktop software

Leverage the knowledge of industry experts
Qualys SCA operationalizes the non-profit Center for Internet Security’s (CIS) Benchmarks by supporting them out of the box and automating the assessment of critical configuration settings on your IT assets against these guidelines.
The CIS Benchmarks , applicable to over 100 technologies and platforms, are unbiased and not motivated by profit considerations, and created via consensus by a community of international cybersecurity experts, including experts from Qualys.

Powered by Enterprise TruRisk Platform
Single-pane-of-glass UI
See the results in one place, in seconds. With AssetView, security and compliance pros and managers get a complete and continuously updated view of all IT assets — from a single dashboard interface. Its fully customizable and lets you see the big picture, drill down into details, and generate reports for teammates and auditors. Its intuitive and easy-to-build dynamic dashboards to aggregate and correlate all of your IT security and compliance data in one place from all the various Qualys Cloud Apps. With its powerful elastic search clusters, you can now search for any asset – on-premises, endpoints and all clouds – with 2-second visibility.
Centralized & customized
Centralize discovery of host assets for multiple types of assessments. Organize host asset groups to match the structure of your business. Keep security data private with our end-to-end encryption and strong access controls. You can centrally manage users’ access to their Qualys accounts through your enterprise’s single sign-on (SSO). Qualys supports SAML 2.0-based identity service providers.
Easy deployment
Deploy from a public or private cloud — fully managed by Qualys. With Qualys, there are no servers to provision, software to install, or databases to maintain. You always have the latest Qualys features available through your browser, without setting up special client software or VPN connections.
Scalable and extensible
Scale up globally, on demand. Integrate with other systems via extensible XML-based APIs. You can use Qualys with a broad range of security and compliance systems, such as GRC, ticketing systems, SIEM, ERM, and IDS.