Secure Your Global Remote Workforce
Last updated on: September 6, 2020
Update June 9, 2020: Qualys adds Malware Detection to Free 60-Day Remote Endpoint Protection offering. This post has been updated to reflect this new Malware Detection capability.
IT organizations around the world are responding to the challenge posed by COVID-19 by ensuring that employees are able to work productively from remote locations. As we are experiencing a never-before-seen explosion of remote endpoints connecting to critical assets of the organization, security of these endpoints is on top of the mind of all IT and Security professionals.
As we look for ways to secure these endpoints, it is becoming immediately clear that traditional enterprise security solutions deployed inside the organization’s network are completely ineffective in protecting these remote endpoints. The sheer volume of remote endpoints connecting over VPN gateways is already creating a lot of bandwidth pressure, adding large security updates delivered to thousands of endpoints is becoming impractical. Additionally, remote endpoints cannot be protected by network perimeter security devices as a line of defense from malware attacks and intrusions.
The most effective way of addressing the security of these remote endpoints is to leverage the cloud-based solutions. The cloud-based solutions are architecturally superior to address the remote endpoint use-case as they connect directly to the cloud over the internet without routing a large volume of traffic through the VPN gateways.
Qualys worked with a lot of its existing customers to immediately release a remote endpoint protection service that will help them quickly address this challenge. This service, which is being provided at no cost for 60 days, leverages the Qualys Cloud Agent and its cloud-based architecture to deliver complete visibility into all remote endpoints; and while going a step further, provides additional ability to remotely patch these systems and detect malware that anti-virus has missed. This approach provides real-time, up-to-date vulnerability and configuration posture with the ability to respond with zero impact to organization’s internet bandwidth and connectivity, which becomes critical in such a scenario.

To help our existing customers, we are prioritizing delivery of this service for those who are already leveraging Qualys Cloud Platform. The service is extremely easy to enable for customers who already have deployed the lightweight Qualys Cloud Agents. The existing customers can sign up here – https://www.qualys.com/forms/remote-endpoint/
For those customers who would like to get Qualys Cloud Agents quickly deployed, here’s more information – https://www.qualys.com/docs/qualys-cloud-agent-windows-install-guide.pdf
We are working to prioritize other organizations who would like to sign up for this service.
Qualys Remote Endpoint Protection offering enables
#1 Tracking up-to-date inventory of all their remote endpoint hardware and the applications they are running
The service enables continuous discovery of remote devices and hosts that are connecting to the network along with their geographical location. Other than this basic information and key inventory meta-data is generated, such as hardware and installed software specifications, services, port and network information, along with software and applications running on the hosts.
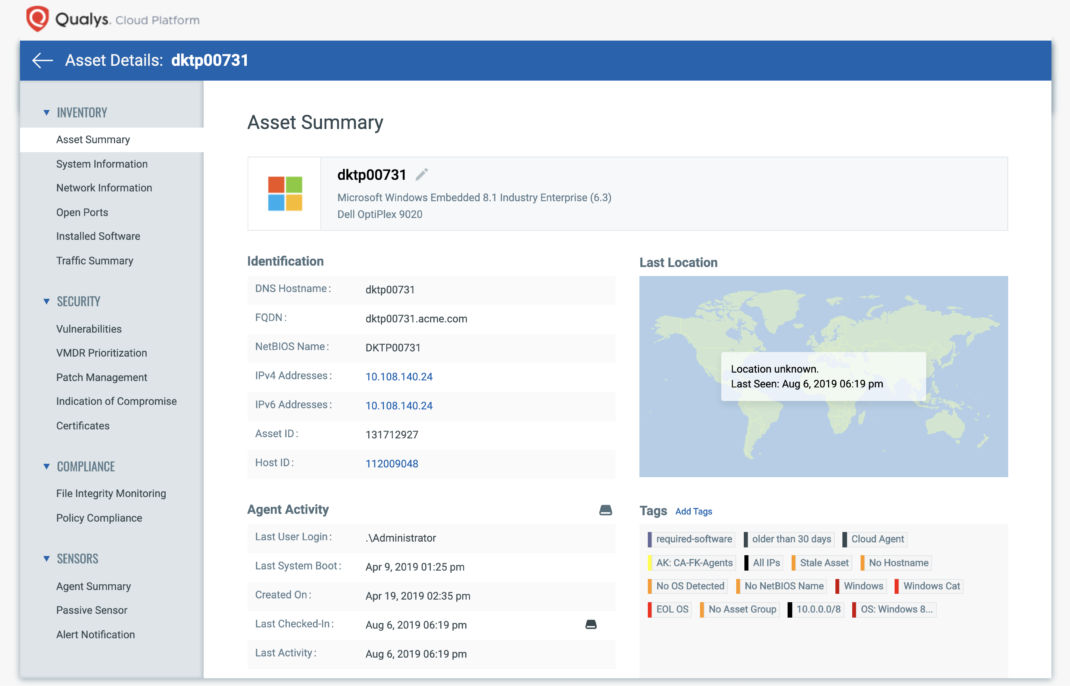
You can track remote endpoints leveraged by key executive management for critical vulnerabilities, security misconfigurations, threats, missing patches, any malicious process.
#2 Gaining a real-time view of all critical remote end-point relevant vulnerabilities impacting the Operating System and applications posing a risk to these devices
While considering remote endpoints, it is important to understand the full vulnerability posture and threats that could impact your users and IT environment. Using the lightweight Qualys Cloud Agent, you can discover and prioritize critical vulnerabilities across all endpoints – whether personal computers, completely remote, or connected to the VPN. Only identifying the OS vulnerabilities is usually not enough. Vulnerabilities are often seen in commonly deployed third-party software such as:
- Web browsers
- Browser plugins and extensions
- Productivity software and PDF viewers
- VPN software
- Web conferencing software
- Archival software
- Media players
The ability to assess vulnerabilities in third-party software is key to maintaining the security of remote endpoints. Attackers know which software is commonly deployed, and often focus their attacks on vulnerabilities using exploit kits, drive-by downloads, Trojan horses, and other types of large-scale campaigns to deliver malicious payloads such as ransomware, crypto mining malware, password stealers, and botnet software. Recent vulnerability disclosures have also involved not only the software on the endpoint, but also the wireless chipsets and drivers such as kr00k and KNOB, which could allow attackers to read confidential data if they are in proximity of wireless traffic.
Having a complete view of every vulnerability across your remote endpoints is critical for understanding where to focus your patching efforts to ensure your users and IT environment are safe. With the Remote Endpoint Protection service, we have released a ‘remote endpoint search list’, specifically for assessing the remote endpoints on Operating Systems as well third-party software.

#3 Remote patching of remote endpoint systems within hours from the cloud with the click of a mouse without using the limited bandwidth available on VPN gateways
Increasing number of remote endpoints may overwhelm VPNs and upstream limited bandwidth. Security teams are looking at efficiently using the limited VPN bandwidth and also not choke the VPN gateways, while prioritizing the patches, based on threats and vulnerabilities. For example, to fix one CVE, it’s often necessary to install multiple incremental patches for different versions of affected products; thus, it is advised that the patching is performed by directly downloading the patches on endpoints from the vendor’s websites and CDNs.
While it is an important first step, just deploying the OS patches is usually not enough. Patching for commonly deployed third-party software as below, is key to maintaining the security of remote endpoints.
- Web browsers
- Browser Plugins and Extensions
- Productivity software and PDF viewers
- VPN software
- Web conferencing software
- Archival software
- Media players

Additionally, Qualys Remote Endpoint Protection service through Patch Management lets you
- Automatically correlate vulnerabilities and patches, which speeds remediation response, especially for high-profile remote endpoints.
- Configure rules and workflows, so patches are auto-deployed when they meet certain criteria such as severity level, CVE, CVSS score, or product name.
- Provide interactive messages to end users for awareness and confidence, by prompting them to install patches, reboot their machines, or inform them about in-progress deployments.
#4 Realize visibility in device hygiene by tracking common misconfigurations that leave the endpoints exposed to exploits
It is important to monitor these remote hosts for security hygiene to minimize the asset or user downtime as well as to reduce the exposure to the breaches or exploits from malware or APTs. This also serves as an evidence for your compliance and risk audit.
The key advantage of configuration hardening is to use it as a compensating control when hosts are exposed to threats from existing unpatched vulnerabilities, especially when immediate patching or rebooting endpoints is not possible. For example, monitoring and hardening RDP settings. If a new RDP vulnerability is published tomorrow, you have already reduced your risk from this potential vulnerability.
The security configuration assessment (and if you are existing policy compliance customer), integrated in Remote Endpoint Protection service, has released two brand new policies, automatically evaluated based on data collected by a common Qualys Cloud Agent. The policies are targeted for tracking critical security settings applicable for remote endpoints such as below:
- Password and account management settings
- Anti-virus settings, anti-phishing settings
- Encryption for data-at-rest
- Web browser security

#5 Detect Malware missed by Anti-Virus and prioritize response based on malware category and family
Qualys Malware Detection, integrated with the Remote Endpoint Protection offering and powered by the Qualys Platform and Cloud Agent, uses file reputation and threat classification to detect known malicious files on remote endpoints. As a result, organizations can respond more quickly to malware ultimately increasing their overall security posture.
Threat intelligence-based file reputation extends beyond traditional anti-virus signatures to detect malware using multiple detection methods: static file analysis, dynamic file analysis, community-sourced detection, and more. This enables Malware Detection to detect malware missed by anti-virus delivering a second layer of detection defenses for remote endpoints.
Additionally, Malware Detection provides additional context to help with investigation and response priority – the type of threat by category (trojan, backdoor, keylogger, PUA, etc.) and malware family name (TrickBot, Kwampirs, Carbanak, Offergenerator, etc.).
Security analysts’ time is precious; they need to focus on the real threats in their environment that anti-virus misses like trojans and backdoors first over less impactful malware like browser tool bars and adware. Malware Detection makes it easy to find important malware attacks, quickly see what systems are infected and how widely the infection is, and deliver real-time alerts via email, ticketing systems, Slack, PagerDuty, and Splunk integration.

#6 Single pane of glass for security and executive management
One of the key metrics for service availability assurance is overall security posture of all remote endpoints.
Unified Dashboard, integrated with the Remote Endpoint Protection offering, provides ability to executive management to monitor on high-level, every facet of the organization’s security effort from inventorying the remote endpoints, to identifying endpoints vulnerable to SMBv3 ghost vulnerability, or to finding how many endpoints are awaiting a reboot after patch application, in a single pane of glass.
- Below are the examples of key metrics and trends that the Unified Dashboard lets you track –
- Endpoints with outdated VPN software versions
- Endpoints with SMB v1/2 running, with weak certificates
- Endpoints missing critical Microsoft Patch Tuesday patches versus endpoints not rebooted after patching
- Endpoints with specific vulnerabilities such as SMB v3, Bluekeep which also have running services such as SMB, RDP and weak authentication.
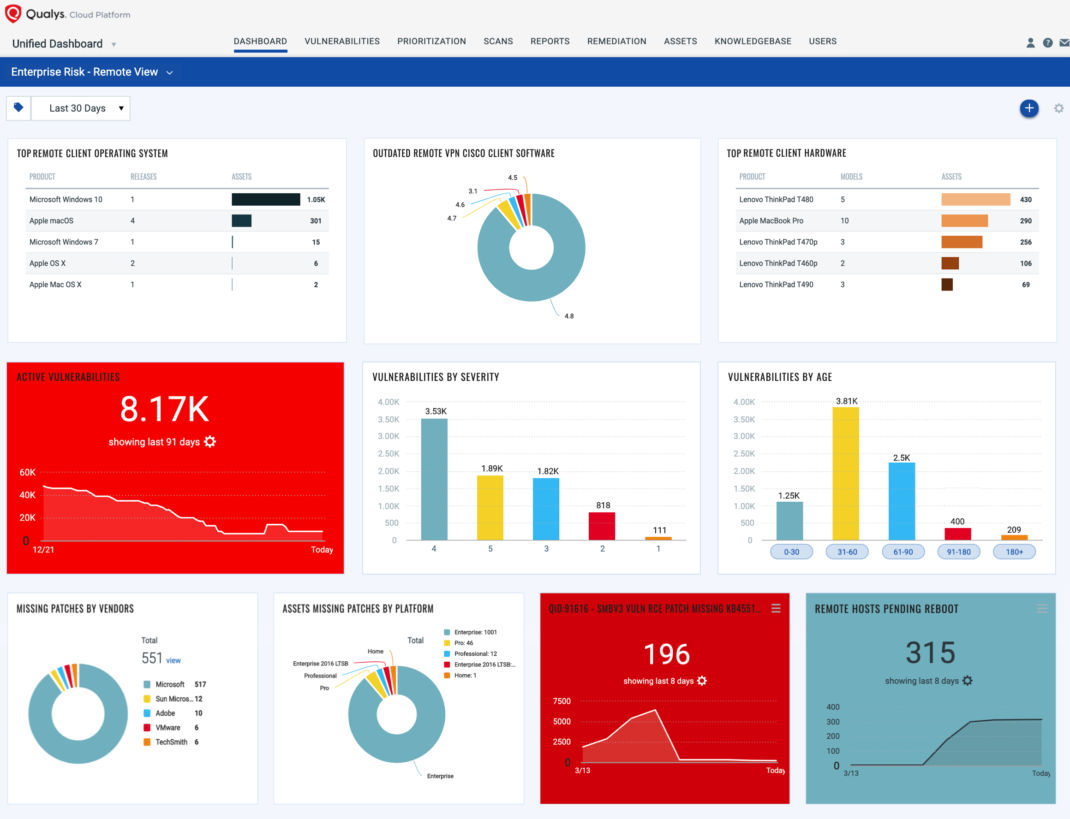
This will help you and your organization’s security management visualize intelligence provided from various security apps such as Vulnerability Management and Patch Management at a single place.
Summary:
Effective immediately, Qualys, Inc. will provide its new cloud-based Remote Endpoint Protection solution at no cost for organizations to allow security teams to gain instant and continuous visibility of remote computers. Security teams will be able to identify missing patches for critical vulnerabilities and deploy them from the cloud. The patches are delivered securely and directly from vendors’ websites and content delivery networks to ensure there is little to no impact on internet connectivity and bandwidth of the organization. Malware Detection detects malware missed by anti-virus and classifies malware into threat categories and malware families to prioritize incident response.
We hope this service helps you quickly get control over your remote endpoints. Please reach out to your technical account manager (TAM) for any questions, comments or feedback.
New customers may reach out to sales@qualys.com for activation queries.
Deepak Naik
Vice President – Platform Security Engineering & Ops, Qualys, Inc
Additional resources:
Patch Management product info and community resources
Video: How to enable and use Qualys Patch Management
Training: Patch Management video library
How Qualys Patch Management lets you automatically correlate vulnerabilities and patches, decreasing your remediation response time
Training: Cloud Agent video library
How you can leverage your existing vulnerability Qualys Cloud Agent for configuration management and remote patching