Kenna is a software-as-a-service Vulnerability and Risk Intelligence platform that accurately measures risk and prioritizes remediation efforts before an attacker can exploit an organization’s weaknesses. Kenna automates the correlation of vulnerability data, threat data, and zero-day data, analyzing security vulnerabilities against active Internet breaches so that InfoSec teams can prioritize remediations and report on their overall risk posture. For more information, visit kennasecurity.com.
Kenna automates the correlation of vulnerability scan data with real-time threat intelligence, enabling Information Security teams to understand precisely where to prioritize and remediate.
The integration of Kenna with Qualys gives enterprises the ability to prioritize what to fix first, to report and track their risk trend over time, and to automate the analysis of three data sources—vulnerability scan data, real-time threat intelligence, and zero-day data—in order to measure their overall exposure to risk.
Kenna supports the Qualys vulnerability management solution right out-of-the-box, making it easy to consume the latest Qualys scan data. Kenna adds real-time context using threat intelligence data sources such as AlienVault OTX™, Dell CTU, Metasploit, ExploitDB and Verisign iDefense. Contextualizing vulnerabilities with what is happening this minute in the real-world allows you to automatically identify weaknesses based on your unique environment, allowing you to save massive amounts of time in your vulnerability management process.
Prioritize Where You Are Most Likely to Be Breached
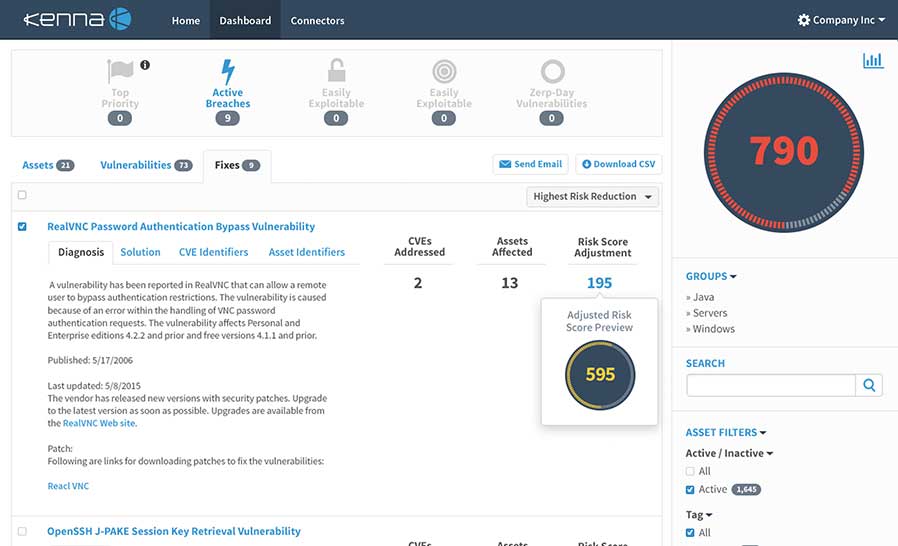
Sync your vulnerability scan data from Qualys and Kenna will contextualize it against active threats including attacks in-the-wild, active Internet breaches, and zero-day vulnerabilities, so you know the threats putting you most at risk. Receive an early warning of exploited vulnerabilities the moment something changes, empowering you to make the right decision within seconds.

Resolve Security Issues at a Faster Rate
Receive real-time scoring on how vulnerable your organizational assets are to real-world attacks and exploits, and see which threats in your data will be the most critical now and over time. Connect the dots between disparate vulnerability data, and share your security risk posture with your team. Spend less time on vulnerability management and keep your systems more secure.
Remediate with Confidence
Kenna matches available patches with vulnerabilities in your environment and helps you prioritize which remediations will truly make an impact. Find out what to fix first (and why), and make remediation decisions backed by analytical rigor to take meaningful actions.
Remediate vulnerabilities that provide the greatest reduction in risk based on real-world threat intelligence, not just internal weaknesses. Know the exact “fix” to give your Development team and confirm proper remediation and prove your actions with data.

Measure Your Risk
See your exposure to threats at-a-glance and report and track your risk trend over time. Use the highs and lows in the dashboard reports to track the progress of your remediation (and identify areas of improvement). And rather than basing your exposure on vulnerability counts, visualize your trending risk in real-time. When everyone in your company has access to the same view of your organization’s risk—from the Remediation Team to the Board Room—communicating and understanding your risk posture is simple.

Automate Your Analysis
Use the power of Kenna to correlate vulnerability scan data, real-time threat intelligence, and zero-day data into one easy-to-understand dashboard display. With Kenna’s sophisticated analysis, manual processes are made automatic with no need to add headcount. With less time spent on parsing scan results, integrating with threat intelligence and creating reports, your Infosec team can double their efficiency and productivity.
How Kenna Prioritization Works
The integration of Kenna with Qualys allows mutual users to connect their Qualys instance into Kenna for advanced vulnerability management. Once connected, each time a security scan is administered in Qualys, the scan data appears in Kenna, where it is correlated with data from Kenna users, publicly available vulnerability repositories, threat data feeds and zero-day data. Kenna then uses predictive analytics to automatically detect and alert on any high priority issues.
Kenna uses metrics that are indicative of risk to determine the probability of risk exposure. Using threat data from the broadest community-sourced threat feeds, Kenna performs an actual risk analysis with these metrics and compares them to each other. Kenna also takes into consideration the motivation of attackers and the real-time tracking of exploitations in this analysis. The riskiest vulnerability on an asset determines the overall risk of that asset.
More information about Kenna can be found at kennasecurity.com
