-
OVERVIEW
Everything you need to measure, manage, and reduce your cyber risk in one place
CAPABILITIES
PLATFORM APPS
-
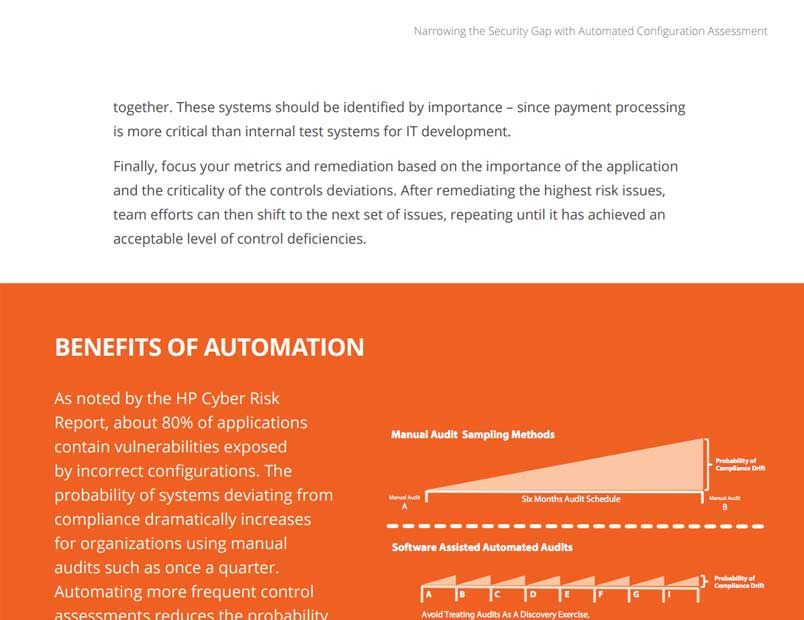
CyberSecurity Asset Management (CSAM)
See entire attack surface, continuously maintain your CMDB, and track EOL/EOS software
-
External Attack Surface Management (EASM) - New
Gain an attacker’s view of your external internet-facing assets and unauthorized software
-
Vulnerability Management, Detection & Response (VMDR) - Most Popular
Discover, assess, prioritize, and patch critical vulnerabilities up to 50% faster
-
Enterprise TruRisk Management (ETM) - New
Consolidate & translate security & vulnerability findings from 3rd party tools
-
Web App Scanning (WAS)
Automate scanning in CI/CD environments with shift left DAST testing
-
Cloud Workload Protection (CWP)
Detect, prioritize, and remediate vulnerabilities in your cloud environment
-
Patch Management (PM)
Efficiently remediate vulnerabilities and patch systems
-
Custom Assessment and Remediation (CAR)
Quickly create custom scripts and controls for faster, more automated remediation
-
Multi-Vector EDR
Advanced endpoint threat protection, improved threat context, and alert prioritization
-
Context XDR
Extend detection and response beyond the endpoint to the enterprise
-
Policy Compliance
Reduce risk, and comply with internal policies and external regulations with ease
-
File Integrity Monitoring (FIM)
Reduce alert noise and safeguard files from nefarious actors and cyber threats
-
TotalCloud (CNAPP)
Cloud-Native Application Protection Platform (CNAPP) for multi-cloud environment.
-
Cloud Security Posture Management (CSPM)
Continuously discover, monitor, and analyze your cloud assets for misconfigurations and non-standard deployments.
-
Infrastructure as Code Security (IaC)
Detect and remediate security issues within IaC templates
-
SaaS Security Posture Management (SSPM) - New
Manage your security posture and risk across your entire SaaS application stack
-
Cloud Workload Protection (CWP)
Detect, prioritize, and remediate vulnerabilities in your cloud environment
-
Cloud Detection and Response (CDR)
Continuous real-time protection of the multi-cloud environment against active exploitation, malware, and unknown threats.
-
Container Security (CS)
Discover, track, and continuously secure containers – from build to runtime
ASSET MANAGEMENT
Vulnerability & Configuration Management
Risk REMEDIATION
Threat Detection and Response
Compliance
Cloud Security
-
CyberSecurity Asset Management (CSAM)
-
More
- Platform
- Solutions
- Resources
- Customers
- Partners
- Support
- Company
- Community
- Login
- Contact us
- Try it
-
Overview
-
Enterprise TruRisk Platform
Everything you need to measure, manage, and reduce your cyber risk in one place
-
CAPABILITIES
- Asset Management
- Vulnerability & Configuration Management
- Risk Remediation
- Threat Detection & Response
- Compliance
- Cloud Security
-
Platform Apps
- CyberSecurity Asset Management (CSAM)
- External Attack Surface Management (EASM) - New
- Vulnerability Management, Detection & Response (VMDR) – Most Popular
- Enterprise TruRisk Management (ETM) - New
- Web App Scanning (WAS)
- Patch Management (PM)
- Custom Assessment and Remediation (CAR)
- Qualys Endpoint Security
- Context XDR
- Policy Compliance
- File Integrity Monitoring (FIM)
- TotalCloud (CNAPP)
- Cloud Security Posture Management (CSPM)
- Infrastructure as Code Security (IaC)
- SaaS Security Posture Management (SSPM) - New
- Cloud Workload Protection (CWP)
- Cloud Detection & Response (CDR)
- Container Security (CS)
- Overview
-
Resources
- Resources Library
- Blog
- Webinars
- Qualys Stream
-
Research
- Threat Research Unit
- Security Alerts
- Security Advisories
-
Contact us below to request a quote, or for any product-related questions
- Chat With Us
- Schedule a Demo
- +1 800 745 4355
- Request a Call or Email
- Global Offices and Contacts
-
Enterprise TruRisk Platform
- Cloud Platform - Free Trial
-
Free Services
- 60-Day Remote Endpoint Protection
- Global AssetView
- Community Edition
- SSL Labs
- CertView
- BrowserCheck
- Overview
-
Platform Apps
-
CyberSecurity Asset Management (CSAM)
See entire attack surface, continuously maintain your CMDB, and track EOL/EOS software
-
External Attack Surface Management (EASM) – New
Gain an attacker’s view of your external internet-facing assets and unauthorized software
- Overview
-
Platform Apps
-
Vulnerability Management, Detection & Response (VMDR) - Most Popular
Discover, assess, prioritize, and patch critical vulnerabilities up to 50% faster
-
Enterprise TruRisk Management (ETM) - New
Consolidate & translate security & vulnerability findings from 3rd party tools
-
Container Security (CS)
Discover, track, and continuously secure containers – from build to runtime
-
Cloud Workload Protection (CWP)
Detect, prioritize, and remediate vulnerabilities in your cloud environment
-
Web App Scanning (WAS)
Automate scanning in CI/CD environments with shift left DAST testing
- Overview
-
Platform Apps
-
Patch Management (PM)
Efficiently remediate vulnerabilities and patch systems
-
Custom Assessment and Remediation (CAR)
Quickly create custom scripts and controls for faster, more automated remediation
- Overview
-
Platform Apps
-
Qualys Endpoint Security
Advanced endpoint threat protection, improved threat context, and alert prioritization
-
Context XDR
Extend detection and response beyond the endpoint to the enterprise
- Overview
-
Platform Apps
-
Policy Compliance
Reduce risk, and comply with internal policies and external regulations with ease
-
File Integrity Monitoring (FIM)
Reduce alert noise and safeguard files from nefarious actors and cyber threats
- Overview
-
Platform Apps
-
TotalCloud (CNAPP)
Cloud-Native Application Protection Platform (CNAPP) for multi-cloud environment.
-
Cloud Security Posture Management (CSPM)
Continuously discover, monitor, and analyze your cloud assets for misconfigurations and non-standard deployments.
-
Infrastructure as Code Security (IaC)
Detect and remediate security issues within IaC templates
-
SaaS Security Posture Management (SSPM) - New
Manage your security posture and risk across your entire SaaS application stack
-
Cloud Workload Protection (CWP)
Detect, prioritize, and remediate vulnerabilities in your cloud environment
-
Cloud Detection and Response (CDR)
Continuous real-time protection of the multi-cloud environment against active exploitation, malware, and unknown threats.
-
Container Security (CS)
Discover, track, and continuously secure containers – from build to runtime