Why FedRAMP High Authorization Can Ensure High Cybersecurity Maturity
Last updated on: February 3, 2023
The Federal Risk and Authorization Management Program (FedRAMP) is a U.S. government initiative that promotes the adoption of secure cloud services across the U.S. federal government by providing a standardized approach to security and risk assessment for cloud technologies. FedRAMP reduces duplicative efforts to comply with multiple federal agency requirements by placing all requirements under a common security framework. FedRAMP approval ensures that federal agencies and other organizations can remain compliant while using a cloud service offering.
FedRAMP provides four types of security baselines, defined as Low, Moderate, High, and Tailored (LI-SaaS). Each baseline refers to applicable NIST Special Publication (SP) 800-53 security controls. A High Impact level requires adherence to about 421 controls, Moderate 325, and Low 125. For each level, vendors can attain a Ready or Authority to Operate (ATO) status, with Ready preceding ATO.
Obviously, all U.S. federal agencies require FedRAMP Ready or ATO solutions. They will need Low, Moderate, or High Impact designations depending upon specific agency security requirements. Many U.S. state and local governments now also require or prefer FedRAMP cloud solutions to ensure best-practice security postures and eliminate friction when working with federal agencies. Many private sector firms also prioritize FedRAMP security solutions to ensure compliance, reduce security risks, and mitigate litigation concerns.
For example, firms that have underscored their Written Information Security Programs (WISPs) using frameworks from the National Institute of Standards and Technology (NIST) or similar models, such as the Center for Internet Security (CIS), could fail audits for non-compliance if they don’t adhere to NIST SP 800-53 v5 controls—the same controls required to gain FedRAMP ATO. Furthermore, organizations that do not comply could face expensive lawsuits and brand damage in the event of a breach, as prosecutors will imply that these firms did not employ the latest best practice recommendations.
Cybersecurity challenges for federal agencies were recently compounded by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which published the Binding Operational Directive (BOD) 23-01. This requires U.S. federal agencies to make measurable progress toward enhancing visibility into asset discovery and vulnerability. Included are several requirements that may not be fully addressed by point solutions such as vulnerability management or endpoint detection and response (EDR/XDR). Moreover, while many private sector firms may believe BOD 23-01 is only relevant to U.S. federal agencies, that might not be true. BOD 23-01 extends Executive Order 14028 (May 2021), which applies to any firm, large or small, in the U.S. or abroad, that conducts business with federal agencies. Also, CISA advises that any organization committed to improving cybersecurity maturity and reducing risks should consider implementing BOD 23-01 as it offers researched best practices to ensure compliance and mitigate breaches.
CISA Director Jen Easterly recently said, “While this Directive applies to federal civilian agencies, we know that organizations across the country, including critical infrastructure entities, are targeted using these same vulnerabilities. It is therefore critical that every organization adopt this Directive and prioritize mitigation of vulnerabilities listed in CISA’s public catalog.”
How can selecting a FedRAMP Ready or ATO solution that also ensures compliance with BOD 23-01 reduce your risks for security breaches, brand damage, compliance failures, and litigation? Since its inception in 2011, less than 220 ATOs have been granted to SaaS firms and other cloud service providers (CSPs) under the FedRAMP program. The typical time and effort required by a vendor to gain authorization is extensive. The cost may be well over seven figures and could take many long months or years, depending upon the level attained. Achieving this designation ensures that a vendor’s solution has been thoroughly evaluated to meet all NIST SP 800-53 requirements. While several cybersecurity vendors now have FedRAMP Moderate ATO, Qualys was the first and is again the first to achieve a High Ready status for our Cloud Platform, with High ATO status expected by the end of 2023. Here’s why that’s important to you:
Qualys GovCloud is currently the only FedRAMP Ready status at the High impact level vulnerability and patch management platform that meets Executive Orders and NIST compliance comprehensively. Qualys GovCloud, including its integrated capabilities, is ‘ready’ to meet the stringent cybersecurity assurance requirements of FedRAMP at the High impact level. High certification is the most stringent with 421 security and risk management controls. Qualys GovCloud is a comprehensive offering including – asset inventory with external attack surface visibility, vulnerability risk and remediation management and compliance management – that federal agencies can use as the foundation for their cybersecurity programs. State, local and other government organizations, as well as private sector firms, can also benefit from the GovCloud platform where stringent security and compliance requirements are needed.
With sensors that include physical, virtual and cloud scanners, a passive network sniffer, APIs and the lightweight and multi-purpose Qualys Cloud Agent, the Qualys Cloud Platform collects telemetry data continuously across your entire IT environment and analyses it in real-time, so you can quickly respond to emerging threats.
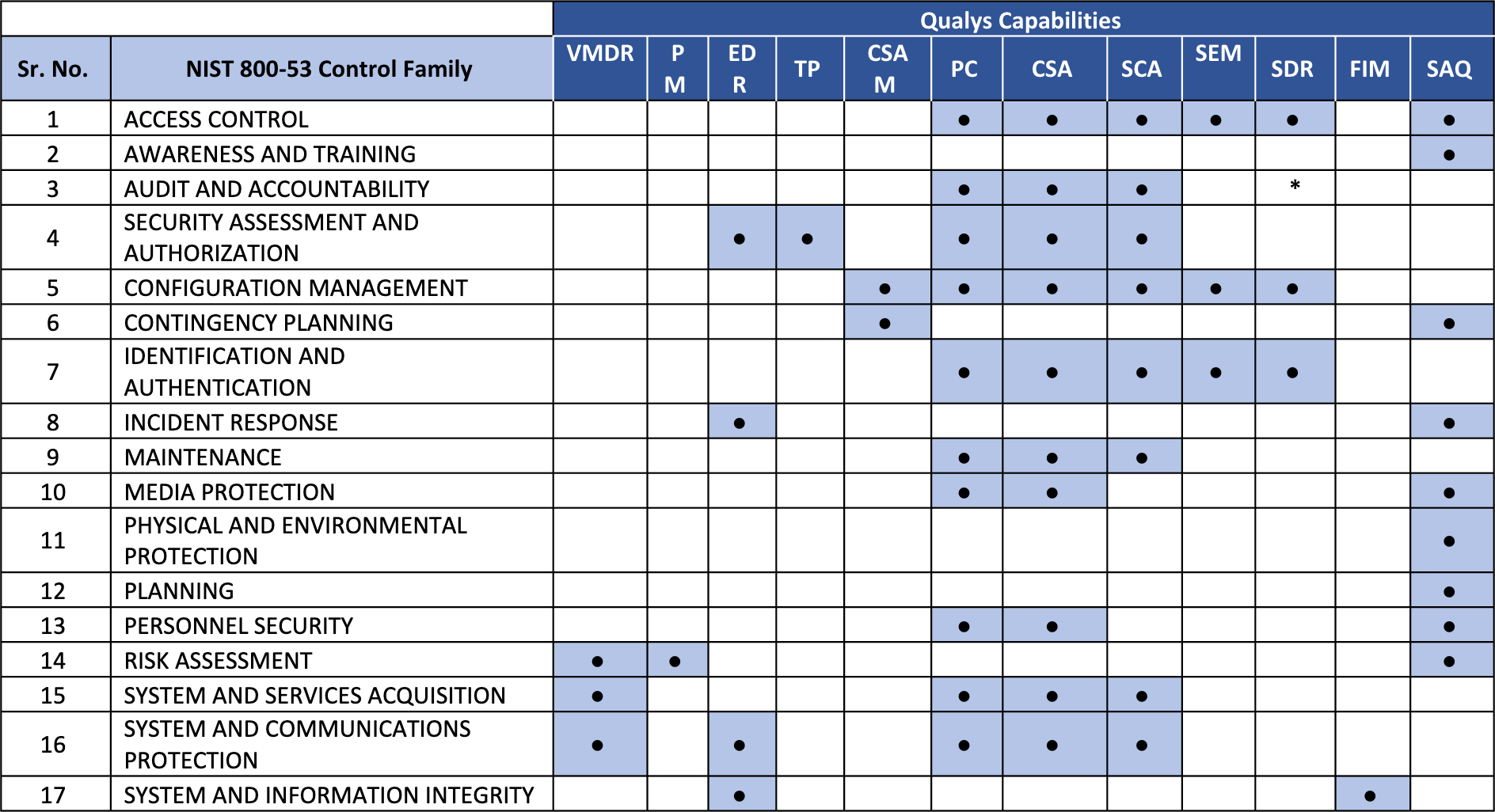
The Qualys GovCloud integrated platform includes all the critical security and compliance solutions needed to address Executive Orders, such as EO14028, and aligns with NIST 800-53 v5 standards, eliminating the need to stitch together siloed solutions. By delivering a comprehensive portfolio and platform-wide capabilities, Qualys helps public and private sector organizations meet the stringent NIST requirements as noted in the chart below, which maps FedRAMP High ATO controls to Qualys solutions.
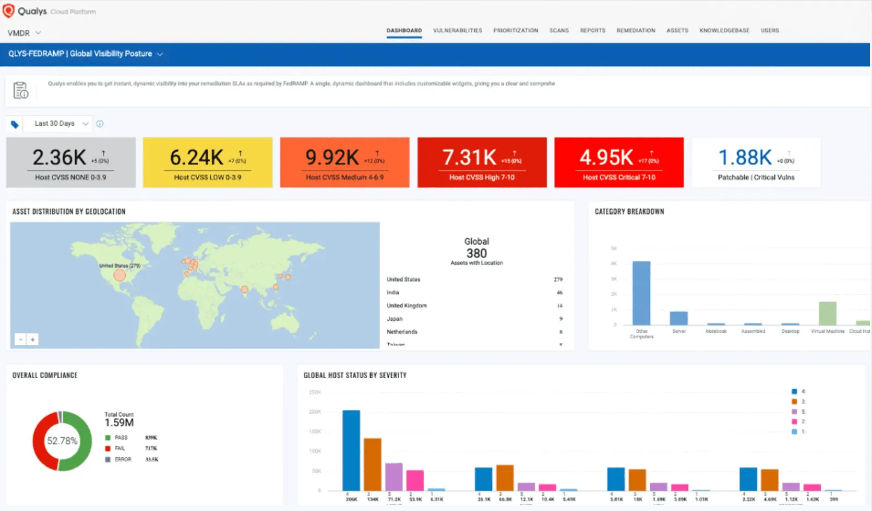
The Qualys Unified Dashboard coalesces compliance data from all Qualys apps and capabilities into one easy-to-manage location. The dashboard delivers a holistic view of your FedRAMP compliance posture, offering single-pane-of-glass visibility across your entire organization. The Unified Dashboard provides greater agility and insight, allowing you to visualize data from all applications together, gain a deeper understanding, gain new insights, and better answer pertinent security and compliance questions.
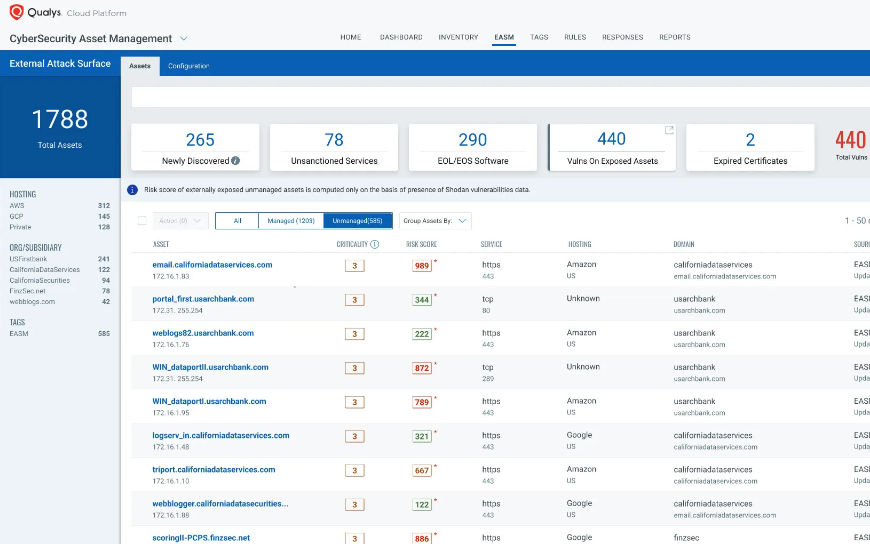
Cybersecurity teams can’t protect what they can’t see. Visibility into your up-to-date inventory is one of the most important and fundamental compliance requirements. Not just for FedRAMP, but for almost any regulatory mandate. Qualys Cyber Security Asset Management (CSAM) helps you meet the CM-8 requirement. With CSAM, you can continuously inventory assets, apply business criticality and risk context, detect security gaps such as unauthorized or EOL software, and respond with appropriate actions to mitigate risks. Qualys CSAM offers an out-of-the-box FedRAMP inventory report that helps you generate an Asset Inventory Report aligned with FedRAMP requirements.
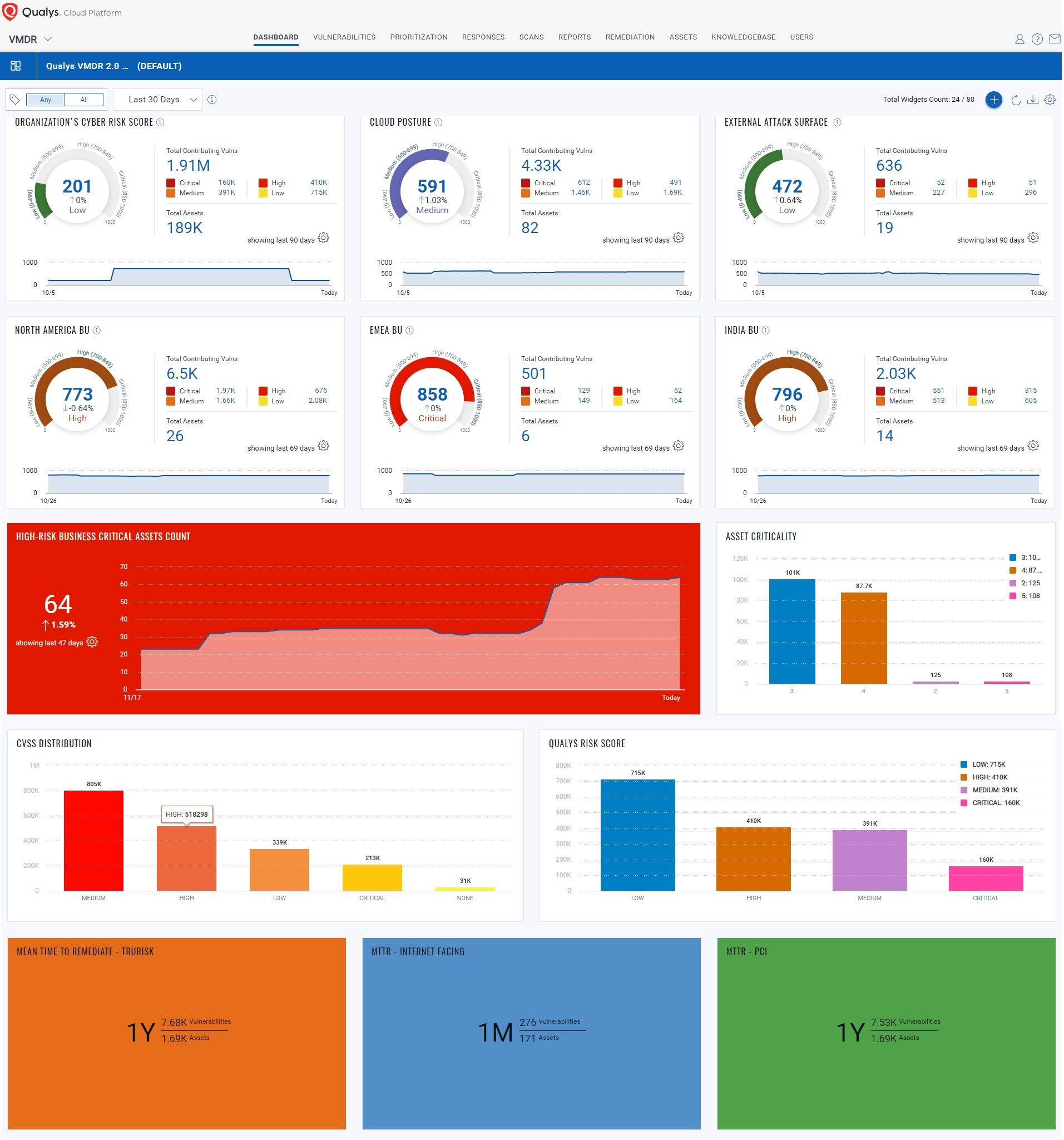
FedRAMP’s RA-5 requirement addresses the vulnerability management process. This requires scanning of your IT environment on a regular basis to check for vulnerabilities and timely or automated patching. Qualys Vulnerability Management Detection and Response (VMDR) helps you meet all RA-5 control requirements to submit a monthly Plan of Action and Milestones (POA&M) report. Qualys VMDR helps you discover, assess, prioritize, and patch critical vulnerabilities in real-time, across your global hybrid-IT landscape. Qualys VMDR uses real-time threat intelligence, advanced correlation, and powerful machine learning to automatically prioritize the highest-risk vulnerabilities on your most critical assets. Prioritizing by criticality can help reduce thousands of discovered vulnerabilities down to only a few hundred that matter the most. Qualys VMDR further prioritizes remediation by assigning a business impact to each asset, such as devices that contain sensitive data, mission-critical applications, public-facing assets accessible via the Internet, and more.
FedRAMP’s SI-7 requirement states that, “The information system must employ cryptographic mechanisms to detect unauthorized changes to software, firmware, and information.” Qualys File Integrity Monitoring (FIM) provides out-of-the-box profiles to monitor highly critical files, registry objects, and actions in support of SI-7. This helps you to kick-start your monitoring efforts and also comply with various compliance standards in addition to FedRAMP.
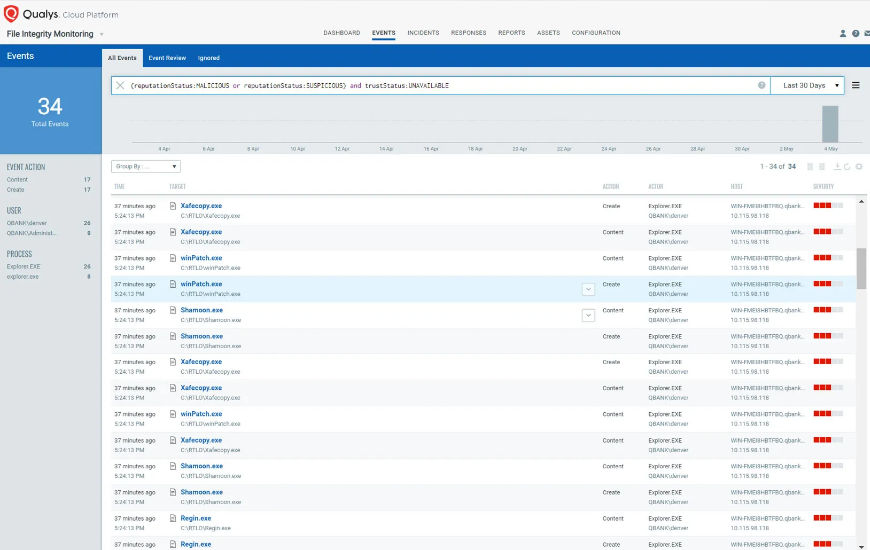
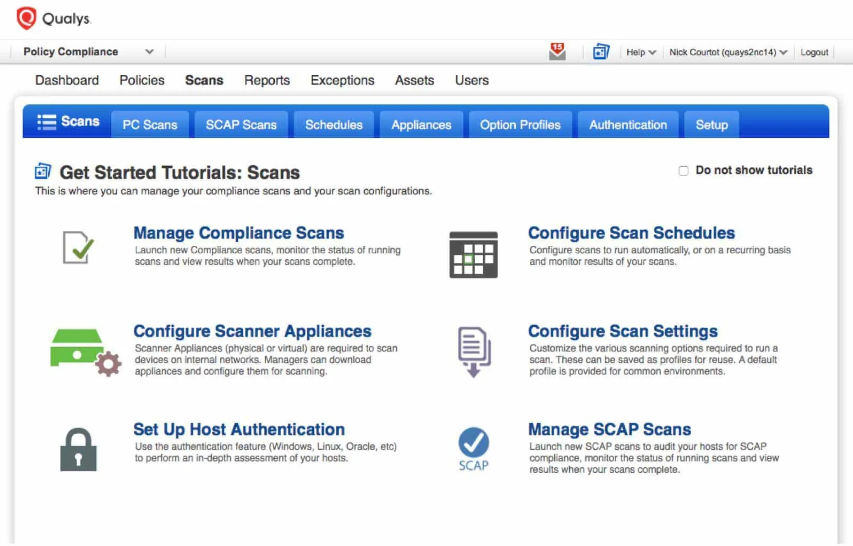
FedRAMP requires that you define stringent baseline policies for your IT environment that include critical servers, hardware, and software. However, definitions are not sufficient. You need to ensure that policies are properly implemented across your entire IT environment. The Qualys Policy Compliance (PC) and Qualys Cloud Security Assessment (CSA) apps help you comply with this important FedRAMP mandate. With Qualys PC and CSA, you can create your own policies with configuration control settings to assess your environment against these to identify misconfigurations, and then remediate any issues automatically. Additionally, Qualys Container Security (CS) helps you address all FedRAMP container-related requirements such as container infrastructure security, DevOps pipeline security, image hardening, registry scanning, container-native vulnerability analysis, and container asset management and tracking.
Leading analysts and industry experts agree that misconfigurations and mistakes are leading causes for security breaches and compliance failures. Going beyond FedRAMP requirements, the CISA BOD-23-01 directive requires addressing these potential issues. Qualys PC includes 850 preconfigured policies, 19,000 controls, 350 technologies, and 100 supported regulations and frameworks. A few relevant Qualys PC capabilities that can help you comply with BD 23-01 include:
- DISA STIGs library content: Security Technical Implementation Guides (STIGs) are configuration standards developed by the Defense Information Systems Agency (DISA). Having this capability helps ensure best practice compliance.
- Expanded control library: PC provides 19K controls to ensure broader support to comply with PCI DSS 4.0, new State Civil Codes such as CCPA, GDPR Availability Breach requirements, and new NIST guidelines.
- Mandate-based reports: best practices to meet compliance mandates include the initiation of robust reports. Having this capability ensures audit-readiness and full compliance.
- Auto-discovery of middleware: most compliance mandates include the ability to initiate on-demand asset discovery within short timeframes. Organizations are advised to comply to ensure cybersecurity best practices and audit-readiness.
- Vendor hardening guidelines: the intent of many compliance mandates is to reduce attack surfaces and risks. Cybersecurity best practices to achieve this include hardening, and proper guidelines improve implementation and reduce efforts.
- Advanced reporting and customized dashboards: this ensures full audit-readiness by reducing time to generate custom reports.
- Remediation: a key intent for many compliance mandates is to address outdated software versions, missing updates, and misconfigurations. Remediating these compliance issues improves cybersecurity best practice maturity.
- MITRE ATT&CK framework: nearly all auditors view the MITRE framework as an important resource to reduce attack surfaces and ensure compliance.
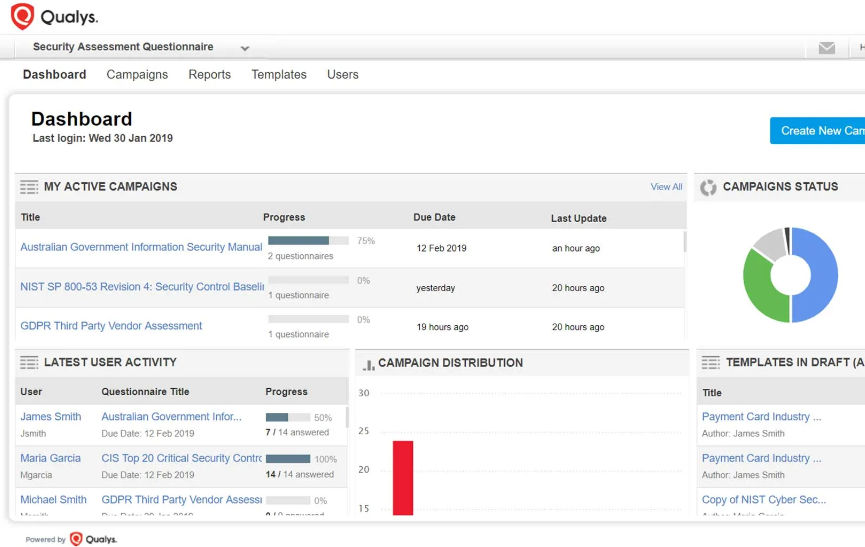
FedRAMP adherence requires you to have policies and procedures in place, and to review these on a regular basis. This is highlighted for every FedRAMP Impact level. Qualys Security Assessment Questionnaire (SAQ) can help you create a security questionnaire and assign it to each respective stakeholder to confirm availability of their policies and procedures, as well as compliance controls. Qualys SAQ also provides out-of-the-box templates that can be used directly for these internal assessments.
Conclusion
Ransomware and other malicious attacks now occur every few seconds. Given frequent changes to compliance mandates and frameworks, and the average cost of a security breach exceeding $4.5 million, public and private sector firms need to fortify defenses by implementing industry best practices. The most comprehensive and effective controls, practices, and guidelines have been created by the U.S. Federal Government. The most stringent of these, which can ensure the highest level of cybersecurity maturity, are outlined in the NIST SP 800-53 publication, which governs FedRAMP ATO. Therefore, selecting a cloud security vendor that has achieved FedRAMP High Ready status, with ATO pending, can help you avoid serious security breaches and audit failures that can lead to expensive remediation and litigation costs. The Qualys GovCloud platform offers the first and only FedRAMP High security assurance in the industry.