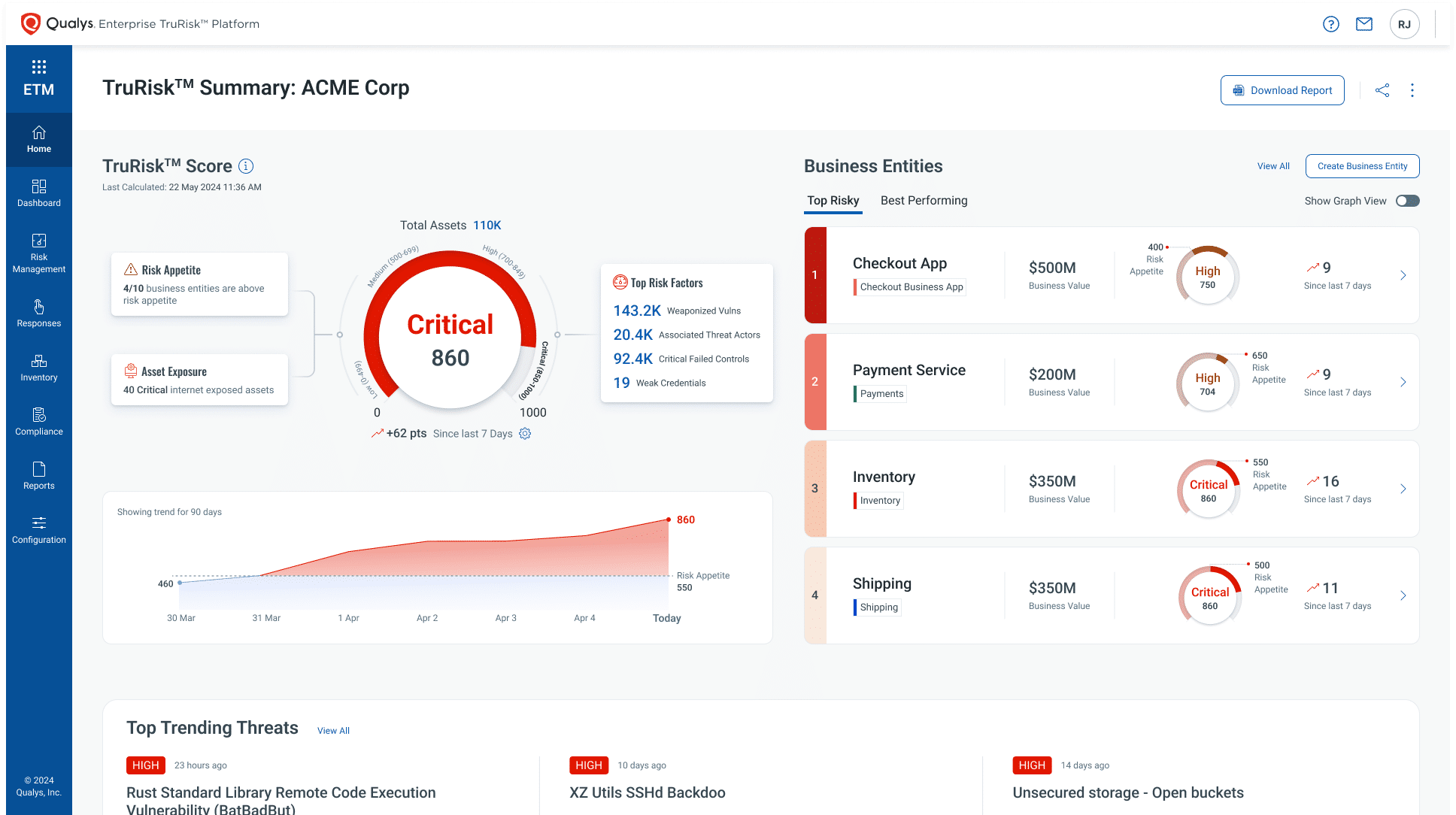
Navigating Cisco Vulnerability Management (formerly Kenna VM) End-of-Life (EOL)
Cisco has announced end-of-life (EOL) for its Vulnerability Management solution (formerly Kenna VM). Kenna's vulnerability-centric approach made sense in 2018, but in 2026:
- Attack surfaces have expanded and are more fluid
- Advanced threats outpace existing patching cycles
- Organizational risk is no longer just about managing CVEs
- Remediation processes need to be tightly orchestrated
Organizations need a unified cyber risk platform that stays ahead of today's AI‑driven threats. Qualys delivers the visibility, context, and automation to turn exposure insights into measurable risk reduction.
Aggregate
findings for
40% faster
risk identification across your siloed security tools
Prioritize
critical risks
85% quicker
using TruRisk™ Score and business context for financial impact
Remediate
risks
50% swifter
with automated patching, IT tickets, & real-time alerts.
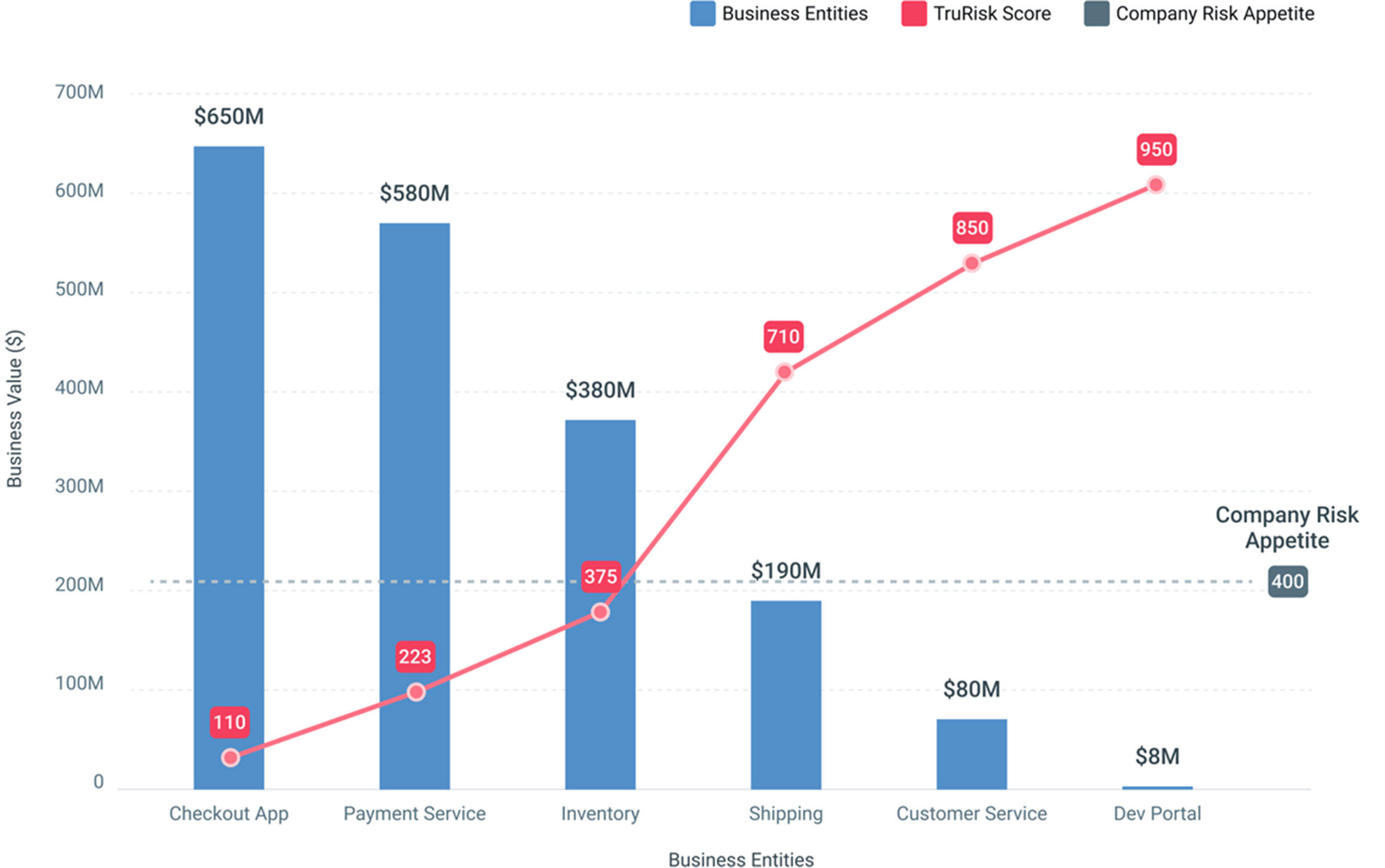
Why Exposure-Focused Risk Management Matters
How Qualys compares to Cisco/Kenna VM
 | Cisco/Kenna VM |
Primary FocusOptimized risk operations by measuring, communicating, and eliminating cyber risk across all attack surfaces. | Primary FocusVulnerability‑centric risk scoring with prioritization based on CVE severity and limited threat intelligence | |
Data AggregationIngests and correlates telemetry across VM, cloud, container security, identity, and third‑party sources | Data AggregationPrimarily from traditional vulnerability scanners | |
Attack Surface CoverageHolistic- infrastructure, cloud, containers, applications, APIs and external attack surface | Attack Surface CoverageInfrastructure‑centric; limited native cloud and AppSec coverage | |
Risk PrioritizationTruRisk™ model combining exploitability, 25+ sources of threat intelligence, asset criticality, business context, and environmental factors | Risk PrioritizationEPSS‑driven likelihood + severity‑based prioritization | |
Business ContextContextual enrichment that ties threat impact to quantified business risk | Business ContextLimited environmental and business context | |
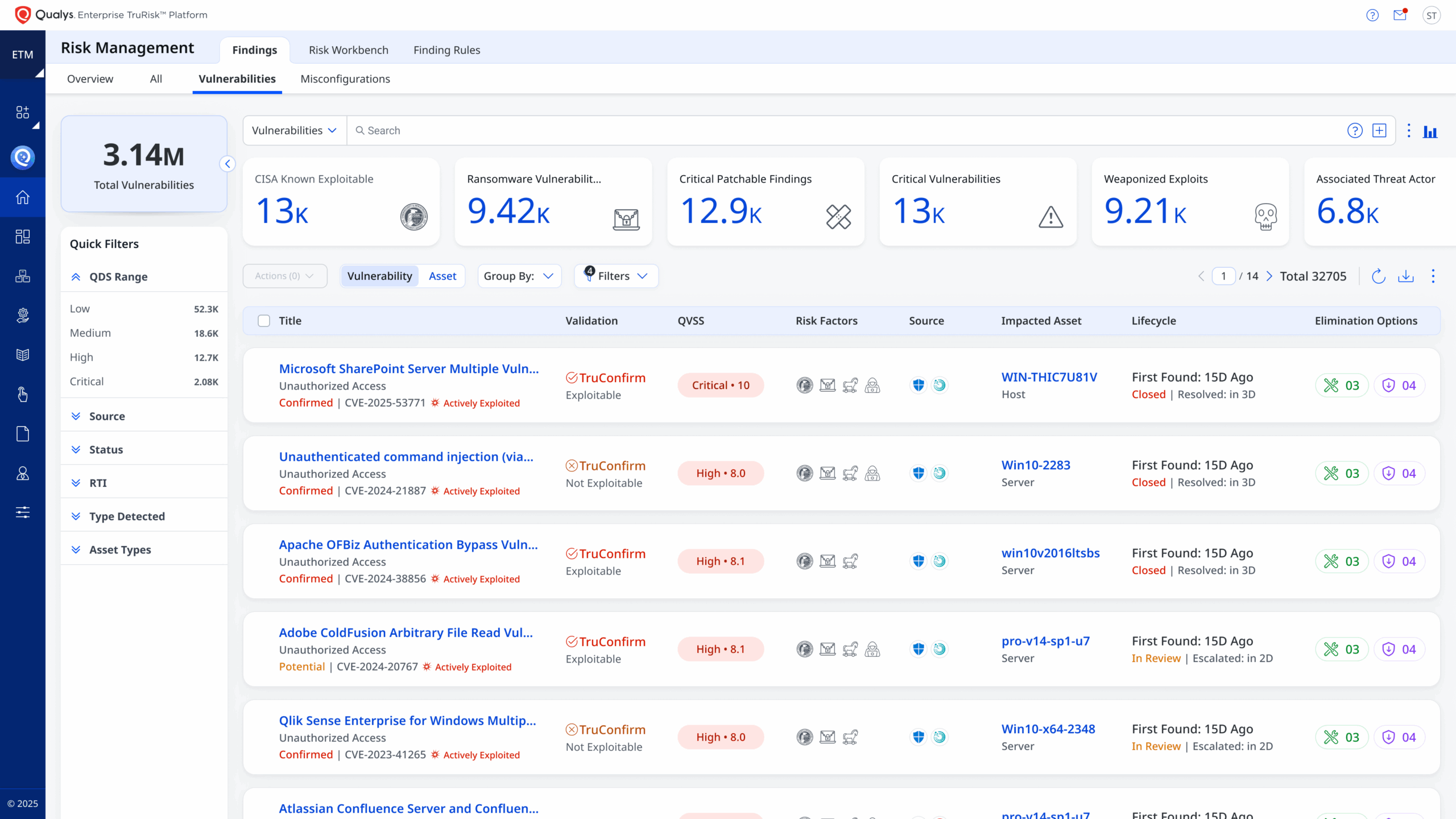
Exploit ValidationValidate exploitability and verify remediation effectiveness | Exploit ValidationRelies on external intelligence and assumptions | |
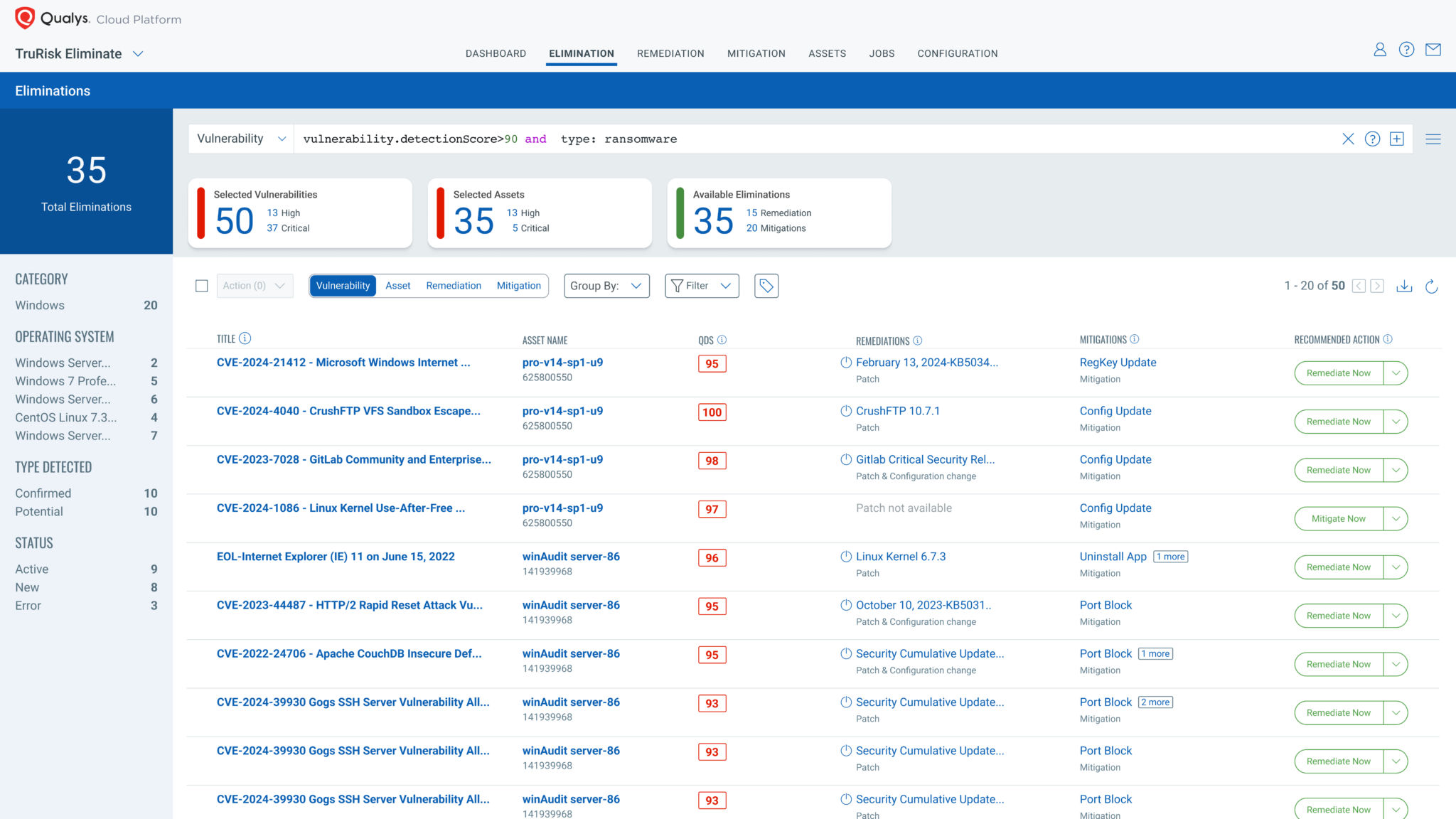
Remediation ApproachOrchestrated remediation with native capabilities (patching, mitigations, compensating controls) with outcome tracking | Remediation ApproachTicket‑centric workflows | |
Executive ReportingBusiness‑focused reporting with risk highlighted in operational and financial terms | Executive ReportingVulnerability and score‑based views |
De-risk your business with the world's #1 cloud-based Risk Operations Center
Measure Risk with Complete Asset Visibility
Unify inventory across all environments to reveal hidden exposures and assess risk posture in real time.
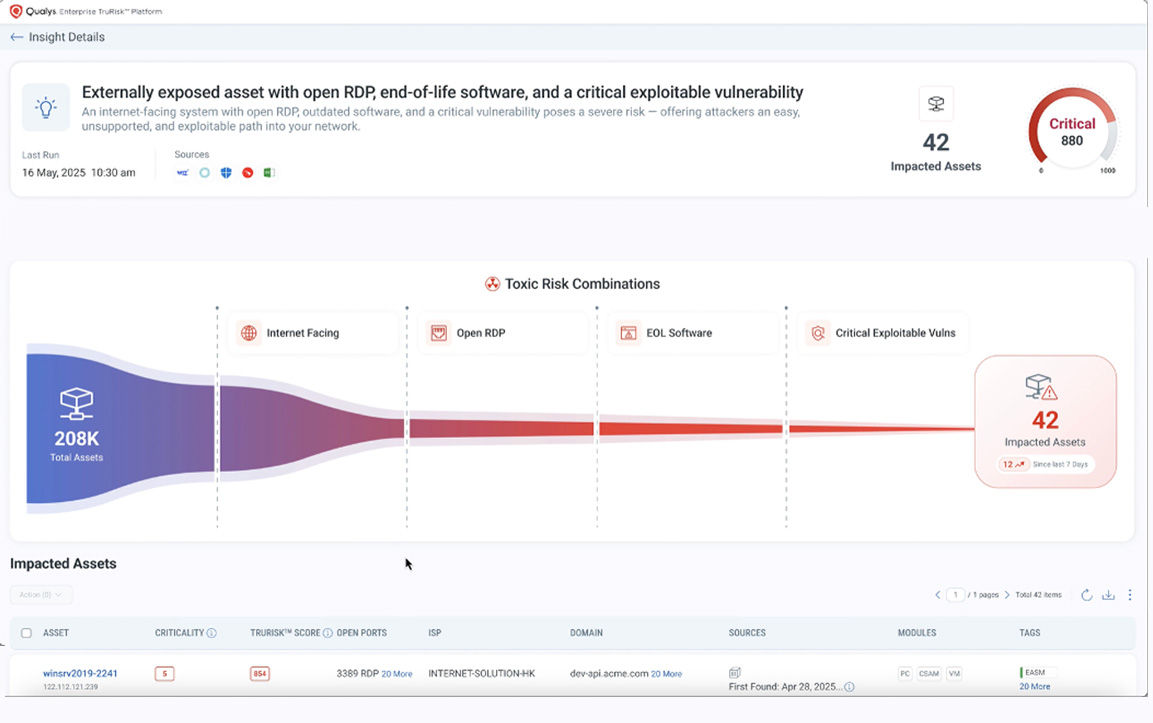
Communicate Risk with Context and Clarity
Enrich and normalize risk data with threat intel and business context to drive confident, board-ready reporting.
Eliminate Critical Risk with Intelligent Automation
Prioritize and remediate threats using TruRisk™ scoring and AI-driven workflows for faster, smarter action.
Scale with Confidence Across Your Enterprise
Seamlessly adapt to growing infrastructure and evolving threats—without adding operational complexity.
Transforming Modern Cybersecurity Risk Management
Discover how the ROC helps organizations unify teams, streamline remediation, and gain continuous visibility across the full attack surface. Download the whitepaper to learn more.