A day in the life
Bruce Wayne
Application Security Analyst
See how Bruce leverages Qualys API Security to address the critical vulnerability in an unauthenticated API endpoint, ensuring the security of millions of customers’ personal information and other sensitive data.
1.Data Breach Sparks Crisis
One morning, Bruce receives an alert about a critical security breach. Attackers have exploited an unauthenticated API endpoint to compile a list of millions of personal data belonging to customers. Understanding the gravity of the situation, Bruce logs into Qualys API Security to address this threat.
2.Unauthenticated API Discovery
Bruce's first step is to utilize the API inventory feature in Qualys API Security. He accesses the APIs tab under Applications to get a complete overview of all API endpoints in the environment for detailed information, including the security status of each API. He filters the list using Qualys Query Language (QQL) to quickly locate the unauthenticated API endpoint that was compromised.
3.Critical Communication and Remediation
With the detailed application report, Bruce informs the CISO and security managers about the vulnerability details and the necessary remediation steps. He uses existing integrations with JIRA to automatically create tickets for the development teams, ensuring that security fixes are promptly addressed.
4.Proactive Monitoring for Future Scans
After the initial remediation, Bruce conducts a re-scan to confirm all issues have been resolved. He updates the scan settings, scanning schedules and option profiles for future Authentication Tests using Authentication & Session Management, Information Disclosure, API Compliance and OWASP API Top 10 categories to check for PII and sensitive data exposures.
5.Configuring Advanced Authentication
Bruce configures the authentication settings to simulate real-world scenarios where the API might be exploited. He also sets up header-based injections to authenticate the API and enable in-depth scans, covering all potential entry points.
6.Vulnerability Testing and Prioritization
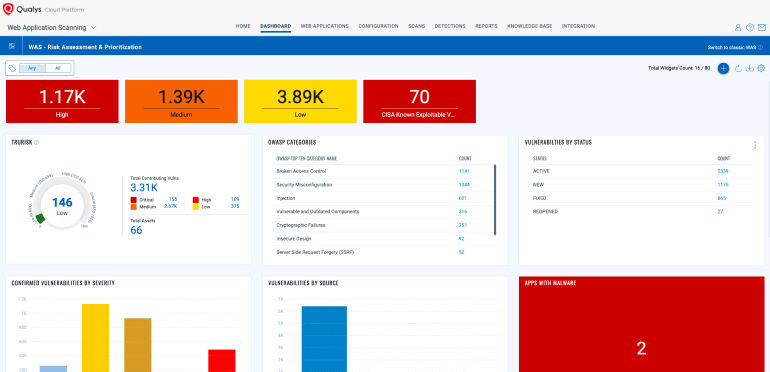
As time progresses, Bruce monitors the Detections tab for critical vulnerabilities like API key and sensitive data exposures via URLs. He checks if passwords, credentials, API keys or tokens are improperly exposed and uses the TruRisk™ scoring system to prioritize these vulnerabilities based on overall business impact.
7.Early Development API Compliance
Bruce navigates to the API Compliance tab to check for deviations from OpenAPI specifications for issues, such as improper input validation, weak encryption protocols, missing '500' error responses, lack of rate limiting and improper string size definitions. Bruce uses these insights to inform the development team about necessary fixes to ensure compliance.
8.Dashboard and Reporting
Bruce creates a dashboard that visualizes the scan results, highlighting OWASP API Top 10 vulnerabilities and sensitive data exposures to be reassured that API assets and the personal data of customers are secure. He categorizes the vulnerabilities by status (new, active, fixed) to have a clear overview for the CISO and other stakeholders.
Data Breach Sparks Crisis
One morning, Bruce receives an alert about a critical security breach. Attackers have exploited an unauthenticated API endpoint to compile a list of millions of personal data belonging to customers. Understanding the gravity of the situation, Bruce logs into Qualys API Security to address this threat.
Unauthenticated API Discovery
Bruce's first step is to utilize the API inventory feature in Qualys API Security. He accesses the APIs tab under Applications to get a complete overview of all API endpoints in the environment for detailed information, including the security status of each API. He filters the list using Qualys Query Language (QQL) to quickly locate the unauthenticated API endpoint that was compromised.
Critical Communication and Remediation
With the detailed application report, Bruce informs the CISO and security managers about the vulnerability details and the necessary remediation steps. He uses existing integrations with JIRA to automatically create tickets for the development teams, ensuring that security fixes are promptly addressed.
Proactive Monitoring for Future Scans
After the initial remediation, Bruce conducts a re-scan to confirm all issues have been resolved. He updates the scan settings, scanning schedules and option profiles for future Authentication Tests using Authentication & Session Management, Information Disclosure, API Compliance and OWASP API Top 10 categories to check for PII and sensitive data exposures.
Configuring Advanced Authentication
Bruce configures the authentication settings to simulate real-world scenarios where the API might be exploited. He also sets up header-based injections to authenticate the API and enable in-depth scans, covering all potential entry points.
Vulnerability Testing and Prioritization
As time progresses, Bruce monitors the Detections tab for critical vulnerabilities like API key and sensitive data exposures via URLs. He checks if passwords, credentials, API keys or tokens are improperly exposed and uses the TruRisk™ scoring system to prioritize these vulnerabilities based on overall business impact.
Early Development API Compliance
Bruce navigates to the API Compliance tab to check for deviations from OpenAPI specifications for issues, such as improper input validation, weak encryption protocols, missing '500' error responses, lack of rate limiting and improper string size definitions. Bruce uses these insights to inform the development team about necessary fixes to ensure compliance.
Dashboard and Reporting
Bruce creates a dashboard that visualizes the scan results, highlighting OWASP API Top 10 vulnerabilities and sensitive data exposures to be reassured that API assets and the personal data of customers are secure. He categorizes the vulnerabilities by status (new, active, fixed) to have a clear overview for the CISO and other stakeholders.