The cloud is a primary target for attackers, and protecting your cloud assets should be a top priority. The 2023 Qualys TotalCloud Security Insights report provides data-backed Risk Facts to help your team ensure effective cloud protection
The research and analysis completed by the Qualys Threat Research Unit will help stakeholders understand what to prioritize and how to remediate the most prevalent cloud risks.
Download the 2023 Qualys Cloud Security Research Insights report to better understand your organization’s cloud security needs. Learn how to better communicate threat data to executives and leaders who might need help understanding cloud security within a cyber risk context.
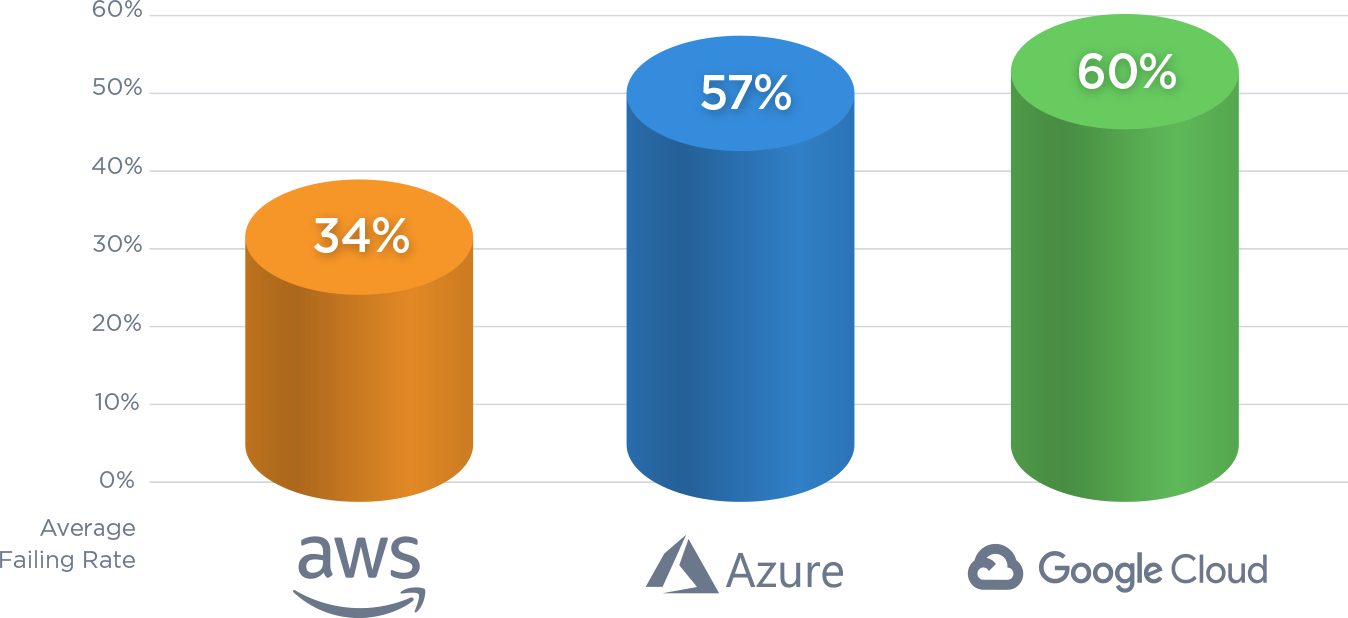
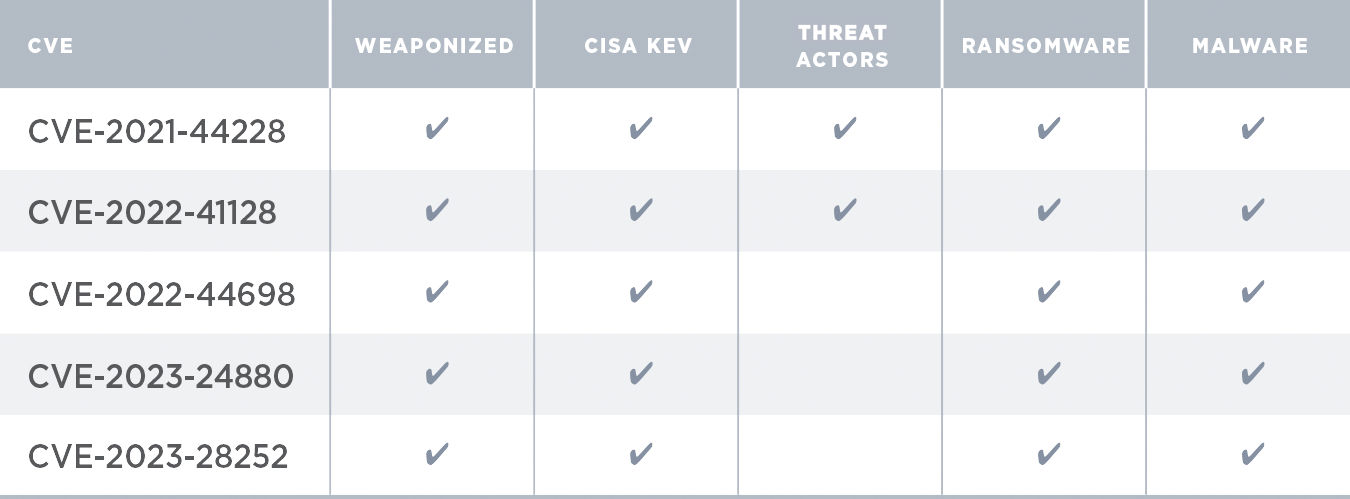
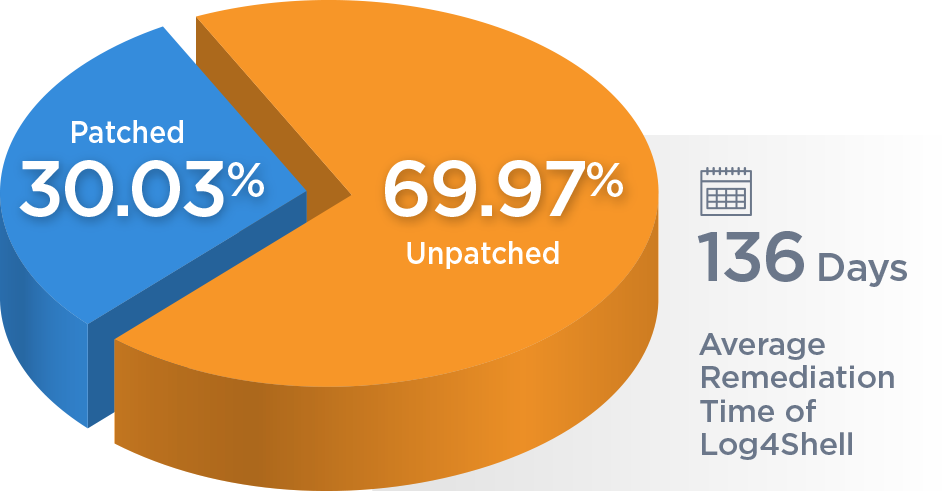
Key findings and risk facts: